CSO Perspectives is a weekly column and podcast where Rick Howard discusses the ideas, strategies and technologies that senior cybersecurity executives wrestle with on a daily basis.
Resilience Case Study: Colonial Pipeline attacks of 2021 (Cyber Sandtable).
This past weekend in northern Virginia, we had glorious weather. My wife Kathy and I took the opportunity to do a little antiquing (actually, she did the antiquing and I mostly drove and napped in the car). As I parked near the “Roaches In the Attic Antiques shop,” one of Kathy’s favorites, I just happened to notice on the GPS that we were very close to something called the Colonial Pipeline Dulles Junction.
Yes, that Colonial Pipeline; the energy conduit that gave us all so much trouble back in 2021 when cyber criminals extorted Colonial Pipeline, the company, with ransomware, and the company leadership shut down their gas distribution pipeline just to be safe. I gave Kathy my go-to look (with over 35 years of marriage practice) that said, “We just gotta go see it.” She returned the favor with her own steely gaze, complete with an eye roll, that signified that I could do whatever I wanted as long as I was back by noon to take her to lunch. With permission in hand, I set off to see if I could find anything interesting.
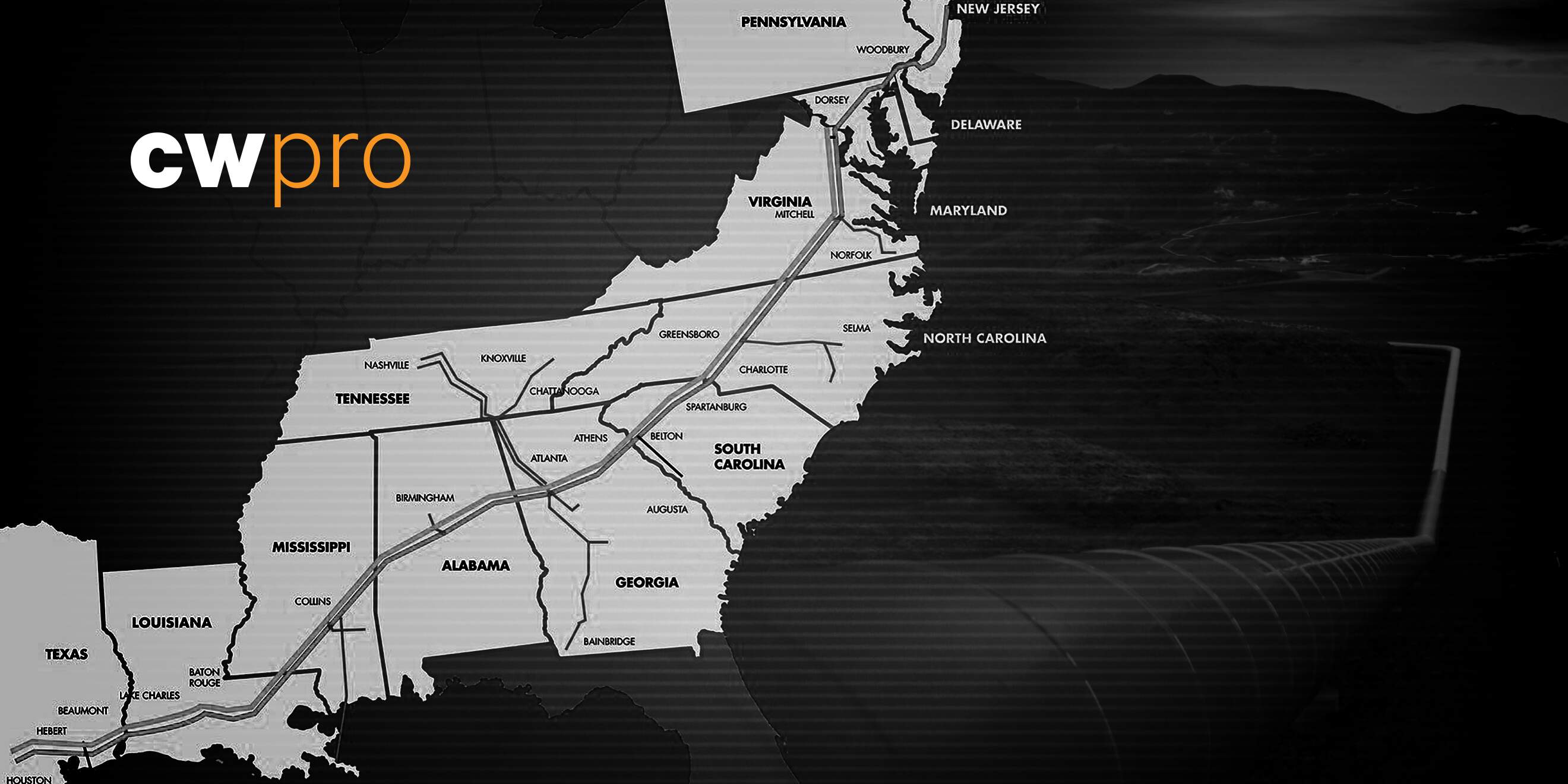
I don’t know what I was expecting, but there wasn’t much to look at. It’s pretty small, a tad tinier than your typical house plot, situated between two neighborhoods near the Dulles International Airport and sitting alongside the Horsepen Run Stream Valley Park. The space is flat and surrounded by a six foot high fence. Inside the perimeter on the left side, is a silver gas pipe, 32 inches in diameter, that protrudes from the ground for maybe 15 horizontal feet and then sinks back into the dirt to continue its journey to Baltimore. This line, line 4, moves roughly 700 thousand barrels of gas per day from Greensboro, North Carolina to Baltimore, Maryland.
It’s one of the many connecting points for the Colonial Pipeline system and is part of the largest pipeline in the United States. The entire system can carry roughly three million barrels of fuel a day over 5,500 miles from Houston to New York. It connects directly to several major airports, including Atlanta, Nashville, Charlotte, Greensboro, Raleigh-Durham, Dulles, and Baltimore-Washington. In other words, this is how your airports on the East Coast get their jet fuel.
When you think of the pipeline in those terms, the scale of it, you quickly realize the significance of the system to the national economy. One small glitch in any of those pipeline junction points from Houston to New York could send rippling waves of energy shortages across the country. The Colonial Pipeline ransomware attack of 2021 did just that, and the attack sequence didn’t even touch the pipeline’s Operational Technology (OT) and Industrial control systems (ICS). The attackers went after the traditional business IT systems. They caused the shortages by being in the general vicinity of the pipeline. That’s kind of scary.
When we talk about cybersecurity first principle strategies, the sexy ones today are zero trust and intrusion kill chains. There were a lot of interesting developments in the 2010s from vendors and security researchers that will contribute to making it easier to deploy those ideas in the future. There isn’t a lot of discussion about resilience and risk forecasting, though. We don’t talk about risk forecasting because it’s hard. We don’t talk about resilience because it's hard and not sexy.
For resilience specifically, I think a lot of us feel like it’s kind of the cybersecurity equivalent of eating your vegetables. And, to pile on, resilience is much bigger than just cybersecurity alone. As my favorite Swedes (Björck, Henkel, Stirna, and Zdravkovic) said in a paper published in 2020, resilience is “… the ability to continuously deliver the intended outcome despite adverse cyber events.” That includes cybersecurity attacks but also an entire slate of other business continuity issues that security leaders don’t own and probably don’t want. Truth be told, the leaders that do own those programs don’t want the CISOs help either.
Still, for the Colonial Pipeline attacks, I think there are some lessons to be learned about resilience by reviewing how the hackers orchestrated their attacks and how the Colonial Pipeline leadership responded. Were there resilience things that could have been improved that would have prevented the crisis? That sounds like a pretty decent cyber sand table exercise to me. Let’s get started.
Setting up the sand table: Colonial Pipeline.
According to Clifford Krauss at the New York Times, the Colonial Pipeline started as a consortium of big oil companies (Phillips, Sinclair, and Continental Oil) back in 1961. Today, it's owned by Royal Dutch Shell, Koch Industries and many other international investment companies. The reason it’s so vital to many Eastern Seaboard airports is that they mostly only have a supply of three-to-five days of fuel stored locally.
Claudia Piccirilli, reporting for the WTW website, said that at the time of the attack, Colonial Pipeline didn’t have a Chief Information Security Officer (CISO), and so the security responsibility for the company’s infosec program fell to the CIO who had been in the seat since 2016.
Let that sink in for a second. In a critical infrastructure company, a company that’s responsible for providing the fuel for many of the airports on the eastern seaboard of the United States, didn’t have an executive dedicated to security. The mind boggles.
Christopher Burgess, from CSO Online, cited an AP interview with a consulting firm, iMerge, that said in a 2018 audit report that Colonial Pipeline’s network security was severely deficient. This is three years before the ransomware attack. That said, the CIO did take some steps to improve the situation by hiring a senior director of technology solutions and increasing the IT budget by 50%--not the security budget, but the IT budget, and presumably some of that money was spent on improving Colonial’s security environment.
Setting up the sand table: Darkside.
The Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) almost immediately attributed the Colonial Pipeline cyberattack to a ransomware-as-a-service offering called DarkSide, with headquarters based in Russia but with no known ties to the Russian government. My editor, John Petrik, says that yes, of course, “No known direct ties, but long standing protection, toleration, and enablement by the Russian government. DarkSide was in all probability a privateer.” In other words, Darkside probably had unofficial State approval to harass and disrupt foreign enemies with cyber crime.
Researchers over at Votiro say they started seeing the first instances of the DarkSide service back in November of 2020, but there is some evidence that hackers behind the service were experimenting with the tools as far back as April of 2019. Their typical attack pattern was to compromise the victim and then go dark for a while before launching the ransomware.
In the past, their one-two punch consisted of the exfiltration of data for blackmail purposes and then encryption of that data for ransom purposes. John Petric says that they were early adopters of this double extortion idea. Researchers observed them gaining initial access through phishing attacks. They preferred to target remotely accessible accounts and Virtual Desktop Infrastructure (VDI) and they maintained persistence with the Remote Desktop Protocol (RDP). According to Snir Ben Shimol at Varonis, the Darkside malware checks device language settings to avoid Russian victims (like looking for a Cyrillic keyboard, a mark of a privateer), and it works on both Windows and Linux systems.
On their deep web advertising site, DarkSide’s marketing people (and the gangs do have marketing crews) professed to have an honor code of not attacking hospitals and schools, and they claimed to have on several occasions donated some of their proceeds to charities.
CSO Online’s Cynthia Brumfield interviewed CrowdStrike’s Josh Reynolds and Eric Lou in 2021. Those two attributed the DarkSide attack pattern to another adversary playbook: Carbon Spider (a.k.a. Fin7, a.k.a. G0046, and a.k.a. JokerStash). According to Cynthia, Carbon Spider started in 2013 using the Carbanak malware to target financial institutions. The CrowdStrike researchers said that the group split into two in 2016: Cobalt Spider targeted credit card data theft and Carbon Spider, the group behind the Colonial Pipeline attacks, stayed with financial entities.
Turn one: Carbon Spider (DarkSide), the red team, 29 April - 6 May 2021.
On 29 April, DarkSide hackers started their initial journey across the Colonial Pipeline kill chain. According to Shimol, they gained the initial beachhead into the Colonial Pipeline’s IT infrastructure, not their OT and ICS infrastructure, through a phishing email targeting a contractor who used a VDI system put into place during the pandemic.
Before this, they performed stealthy reconnaissance, and when they did attack, “they took steps to ensure that their attack tools and techniques would evade detection on monitored devices and endpoints.” Shimol says that DarkSide hackers installed the TOR browser on victim machines to establish their main command-and-control (C2) channel. They configured them to run as a persistent service and redirected traffic through the TOR network. He said that his team found evidence of TOR clients on many servers and collected telemetry on many active TOR connections.
As a secondary C2 channel, the DarkSide hackers used Cobalt Strike. The Veronis team found evidence of dozens of Cobalt Strike stagers that Darkside deployed using WinRM (Windows Remote Management). They configured every stager differently and connected each to its own unique remote server, which indicates a relatively large C2 infrastructure. Shimol said that the hackers stored TOR Browser executables on Colonial Pipeline file shares but avoided systems with deployed EDR (Endpoint Detection and Response) clients.
For lateral movement, the Veronis team said that DarkSide hackers logged into many VDI accounts, sometimes several at once, and created .lnk files back to the compromised victim’s home folders. They used these shortcuts to keep track of successful machine breaches and the associated accounts used. They collected credentials using the Mimikatz DCSync attack tool to steal credentials from the entire domain and an Active Directory reconnaissance tool called ADRecon.ps1 that siphoned out information about users, groups, and privilege. They also retrieved browser user profile credentials from Microsoft, Firefox and Google and took care to delete each attack tool after use.
Shimol says that the DarkSide hackers mined data from hundreds of victims’ machines simultaneously using a batch routine and then compressed them into zip files. He said that even though they had gained elevated privileges, they chose to instead reduce restrictions on the various file shares so that normal users without any privilege could access them. “The batch file, target data, and the archives were deleted by the attackers within hours of collection.”
According to Veroinis, DarkSide delivered the ransomware code (the data encryption piece and the accept-payment piece), through the already established C2 infrastructure.
On 6 May, the hackers behind the DarkSide attack completed their exfiltration of 100 gigabytes of data (the equivalent of a stack of paper taller than the tower over the Burj Khalifa, one of the tallest skyscrapers in the world), encrypted everything, and then demanded payment not only to decrypt the data but to prevent the release of it to the public. The actors then threatened to publicly release the data if the ransom was not paid
Turn one: Colonial Pipeline, the blue team, 7 - 15 May 2021.
According to Joseph Blount, the Colonial Pipeline CEO, on 7 May (Friday), just before 5 AM, a control room employee saw the ransom demand appear on his computer screen. Once notified, the employee’s supervisor began shutting down the pipeline as a precautionary step and completed the task by 6:10.
That same day, the Colonial Pipeline leadership team decided to inform the FBI about the attack. They also authorized and delivered the payment of the 75 Bitcoin ransom (nearly $5 million). Let’s pause on that little factoid a second. Within hours of the ransom request, Colonial Pipeline leadership was able to put its hands on $5 million dollars and execute a Bitcoin transaction. I mean, I knew that the oil industry was rich and connected, but if I want to extract $500 dollars out of my own bank account, it usually takes three days. They were able to call the bank, grab a cool $5 million and transfer it out to some shady ransomware players all in one day. I'm just saying .
I have been unable to find this out for sure, but the execution speed for this three-step action list (ransomware notification, notify the FBI, and execute a Bitcoin payment) was so swift that it leads me to believe that this was part of a planned crisis action response; something that the leadership team had practiced and were prepared to execute. I could be wrong about that. I asked the Colonial Pipeline CIO to come on the show to discuss, but she didn’t respond. I don’t blame her either. But I thought I would ask.
The next day, 8 May (Saturday), Colonial Pipeline announced to the public that they had been hit by a ransomware crew and what they were doing about it. Again, this is another piece of evidence that this was part of the crisis action playbook, announce early and keep the public informed. They continued the public broadcast of information throughout the crisis.
But, according to Derek Johnson at SC Media, “The company had a plan in place for undergoing a controlled shut down of pipeline operations in the event of a loss of SCADA or voice communications control, but federal regulations specifically require companies to have and test a plan for resuming operations manually in those conditions. Colonial didn’t do that.”
Incident responder contractors, with help from the FBI, CISA, and the NSA, identified the Colonial Pipeline internal staging servers that DarkSide was using to exfiltrate data and took them offline. This was too late to stop the 100 gigabytes of data already exfiltrated but prevented even more damage. A computer security company specializing in cryptocurrency (Elliptic) announced that it had identified the Bitcoin wallet used by DarkSide to collect the Colonial Pipeline ransom payment.
The next day, 9 May (Sunday), U.S. President Joe Biden declared a state of emergency and removed restrictions concerning fuel transportation by road. On Monday (10 May), Georgia Governor Brian Kemp declared a state of emergency and waived collection of the state’s taxes on diesel and gasoline. President Biden announced that the attacks were of Russian origin but not sponsored by the Russian government, and the FBI confirmed that DarkSide was behind the attack. Colonial Pipeline leadership announced that it had manually opened a piece of the pipeline temporarily (Line 4 from North Carolina to Maryland) for a short period to get the existing oil it had on hand down the line.
On 11 May (Tuesday), CISA and the FBI issued a cybersecurity advisory that described how the DarkSide ransomware worked and provided suggested risk mitigation strategies. Colonial Pipeline outlined their alternative fuel shipping strategies that they now had in place to lessen the impact of the crisis.
The next day, Wednesday (12 May), Colonial Pipeline resumed basic operations. It had taken the previous five days to verify that the pipeline OT and ICS systems weren’t infected by the Darkside ransomware. Still, more than 1,000 gas stations didn’t have any gas and U.S. citizens were in the middle of a “panic-buying” spree across the Southeastern United States. Remember the picture of the guy filling plastic bags at the pump with gasoline, the same kind of plastic bag that would disintegrate in minutes because of its reaction to the fuel? Ya, that kind of panic buying.
On 13 May (Thursday), the FBI announced that it had hacked the DarkSide Bitcoin wallet and moved the digital currency to a wallet that they controlled. Essentially, they stole the money back from DarkSide. Law enforcement officials wouldn’t elaborate on how they did it but, according to Mathew Schwartz writing for Euroinfosec, clues exist. He quotes Pamela Clegg, the director of education and investigations for blockchain analytics at CipherTrace, who claimed that the FBI got the DarkSide wallet key from some other international law enforcement agency who had penetrated the DarkSide cryptocurrency infrastructure prior to the pipeline attacks. According to Schwartz, reading from an affidavit in support of a search warrant filed with the Northern District of California U.S. District Court, “the cryptocurrency was moved through at least six other bitcoin wallets.” The FBI followed the flow of funds until they ended up in a wallet for which they had the private key.
By 15 May (Saturday), Colonial Pipeline had everything turned on again but, at this point, there were over 10,000 gas stations still out of fuel. It still took several days to get back to normal.
Turn two: Carbon Spider (Darkside), the red team, 14 May - 21 July 2021.
On 14 May, Darkside told its affiliates that because of pressure from U.S. law enforcement, it was closing shop. But, many intel analysts were skeptical, and suspected that this was just another rebranding exercise similar to those other ransomware groups in the past had undertaken: like Bitpaymer changing to Dopplepaymer to and ultimately to Grief, or Hermes rebranding from Ryuk to eventually Conti.
According to Cynthia Brumfield at CSO Online, a new ransomware-as-a-service emerged on 21 July, called BlackMatter. CrowdStrike said there was enough overlap in tools in the attack sequence that they were fairly certain the service was just DarkSide operating under another name.
Turn two: Colonial Pipeline, the blue team, 9 May 2022.
Almost to the day, a year after the DarkSide attacks against Colonial Pipeline, The U.S. Department of Transportation announced it was seeking to levy nearly $1 million in fines against Colonial Pipeline for a series of safety violations that they say contributed to the pipeline’s decision to temporarily shut down gas operations on that first day. According to SC Media, Colonial Pipeline leadership welcomes the investigation and wants everybody to know that this was "the first step in a multi-step regulatory process and we look forward to engaging with PHMSA to resolve these matters." They also defended the contingency planning in the wake of the ransomware attack, saying it was "necessary" and tailored to the company's operating environment.
Colonial Pipeline resilience hotwash.
In this podcast, we talk about cybersecurity first principle strategies. Resilience is one of them, and it’s of the same importance as the other three: zero trust, intrusion kill chain prevention, and risk forecasting. As I said at the top of the essay, resilience is “… the ability to continuously deliver the intended outcome despite adverse cyber events.” Clearly, the Colonial Pipeline response to the DarkSide ransomware attacks did not meet that standard. Not only did the leadership not continuously deliver fuel to their customers during the crisis, but there was an eastern seaboard shortage for over a week. To have a well deployed resilience strategy though, you have to be pretty good at several resilience tactics: crisis planning, backup and encryption of material data, and incident response.
For crisis planning, it appears they had a plan to deal with ransomware and had at least talked about how they would execute it before the crisis happened. The way Colonial Pipeline came out of the gates swinging, immediately shutting down the pipeline, notifying the FBI, and paying the ransom, all on the first day of the attacks, shows some prior planning. As I said, I haven’t confirmed that with anybody at Colonial Pipeline, and the U.S. Department of Transportation has some concerns with the plan they executed. But it looks like they had a plan.
Colonial Pipeline didn’t encrypt their material data, or probably any data for that matter, especially the 100 gigabytes of data DarkSide exfiltrated to their own servers. And it’s unclear if Colonial Pipeline had a decent backup of their material data. That didn’t seem to factor into their incident response plan, though. They saw the ransom demand and immediately shut down the pipeline.
The one bigger error in their plan was that they couldn’t determine whether the ransomware attack was isolated to the IT side of the house or had contaminated the OT and ICS side. They just assumed that everything was contaminated and shut everything down. That was the safe call for sure, but it didn’t meet the resilience standard of continuously delivering the intended outcome.
And I'm not even really talking about how Colonial Pipeline failed to implement the other three first principle strategies either. A simple zero trust tactic, like two-factor authentication, would have prevented the DarkSide initial entry point. But we are focusing on resilience here.
The cybersecurity sandtable.
As I said when I did the OPM sandtable exercise, it’s easy to Monday-morning-quarterback massive failures in preventive cybersecurity. But, for all network defenders, during the heat of the battle, it’s tough to take a beat and reflect on what could be done better next time. This is why cybersecurity sand table exercises are important. When there isn’t a crisis afoot, you can learn quite a bit by taking a few moments to analyze what happened on both sides. I highly recommend you insert them into your first principle programs.
Colonial Pipeline timeline.
April 2019
First evidence of Darkside tools being tested on the Internet.
November 2020
First instances of the Darkside service being used.
29 April 2021
- Darkside Hackers gain entry into the networks of Colonial Pipeline through a virtual private network account.
6 May 2021
- Darkside Hackers execute ransomware campaign by stealing 100 gigabytes of data before locking computers with ransomware and demanding payment.
7 May 2021
- Colonial Pipeline notifies The FBI of a network disruption.
- Colonial Pipeline shutdown their IT systems and temporarily paused production on a majority of their pipelines.
- Colonial Pipeline paid nearly $5 million to Russian hackers.
8 May 2021
- Colonial Pipeline issues statement on attack stating they have been victims of ransomware and have engaged a third-party cybersecurity firm and alerted law enforcement.
- Colonial Pipeline, unnamed U.S. companies and several U.S. government organizations (including the White House, the FBI, CISA and NSA) shut off key servers operated by the hackers. The steps stopped the flow of stolen Colonial Pipeline data from the United States to alleged hacker locations in Russia.
- Elliptic, a computer security company specializing in cryptocurrency, said that it had identified the Bitcoin wallet used by DarkSide to collect the Colonial Pipeline ransom payment.
9 May 2021
- Colonial Pipeline issued a second statement giving an update of their investigation into the attack and the status of their pipeline operations.
- Joe Biden, the U.S. president, declared a state of emergency and removed restrictions concerning fuel transportation by road.
10 May 2021
- Georgia Governor Brian Kemp declared a state of emergency and temporarily waived collection of the state’s taxes on diesel and gasoline.
- President Biden said that the hackers operate out of Russia.
- The FBI confirmed that DarkSide ransomware is responsible for the compromise of the Colonial Pipeline networks.
- Colonial Pipeline opens Line 4 (which runs from Greensboro, N.C., to Woodbine, Md.) under manual control for a limited period of time while existing inventory is available.
11 May 2021
- The CSIA and FBI issued a cybersecurity advisory that described DarkSide ransomware and associated risk mitigation strategies.
- Colonial Pipeline described alternative fuel shipping strategies that are now in place amid the effort to safely restore the pipeline.
12 May 2021
- Colonial Pipeline managed to resume pipeline service (5:00 p.m. ET) though it will take a few days for the supply chain to return to normal performance.
- Panic Buying: More than 1,000 fuel stations have run out of gasoline amid “panic buying” in the Southeastern United States.
14 May 2021
- DarkSide announced that it is shutting down because of unspecified “pressure” from the United States.
15 May 2021
- The pipeline operations were fully restarted
- The DarkSide RaaS operation was shut down.
18 May 2021
- Despite the authorities best efforts, 10,600 gas stations were still out of fuel.
7 June 2021:
- The U.S. government recovered a “majority” of the millions of dollars paid in ransom to hackers behind the Colonial Pipeline cyberattack.
21 Jul 2021
- A new group called BlackMatter emerged seeking access to big game ransomware targets with annual revenues above $100 million in the US, Canada, Australia, and the UK. CrowdStrike reverse-engineered the DarkSide and BlackMatter Windows variants and saw sufficient overlaps to believe that BlackMatter is simply DarkSide in a new guise.
9 May 2022:
- The Department of Transportation is seeking to levy nearly $1 million in fines against Colonial Pipeline for a series of safety violations. The violations allegedly contributed to the pipeline’s decision to temporarily shut down gas operations in the wake of the May 2021 DarkSide ransomware attack.
References.
“CARBON SPIDER Embraces Big Game Hunting, Part 1” by Eric Loui, CrowdStrike, 30 August 2021.
“China Compromised U.S. Pipelines in Decade-Old Cyberattack, U.S. Says,” by Dustin Volz, The Wall Street Journal, 20 July 20 2021.
“CISA: China Successfully Targeted US Oil and Natural Gas Infrastructure,” by Christopher Burgess, CSO Online, 20 July 2021.
“Colonial May Open Key U.S. Gasoline Line by Saturday after Fatal Blast,” by Devika Krishna Kumar, Reuters, 31 October 2016.
“Colonial Pipeline Cyberattack: Timeline and Ransomware Attack Recovery Details,” by Joe Panettieri, MSSP Alert, 9 May 2022.
“Colonial Pipeline Cyber Incident,” Energy.gov, 2021.
“Colonial Pipeline One Year Later: Are Critical Infrastructure Operators More Secure?,” by Scott Kannry, Axio, 18 May 2022.
"Colonial Pipeline Paid a $5M Ransom—and Kept a Vicious Cycle Turning," by LILY HAY NEWMAN, Wired, 14 MAY 2021.
“Colonial Pipeline Take-Away for CISOs: Embrace the Mandates,” by Christopher Burgess, CSO Online, 7 June 2021.
“Colonial Pipeline – Timeline of Events,” by nGuard, 2021.
"Cyber Resilience – Fundamentals for a Definition,” by Fredrik Björck, Martin Henkel, Stockholm University, Janis Stirna, Jelena Zdravkovic, Stockholm University, Article in Advances in Intelligent Systems and Computing, January 2015.
“DarkSide, Blamed for Gas Pipeline Attack, Says It Is Shutting down,” By Michael Schwirtz and Nicole Perlroth, NYTs, 14 May 2021.
“DarkSide Ransomware: Best Practices for Preventing Business Disruption from Ransomware Attacks,” by CISA, 2021.
“DarkSide Ransomware Servers Reportedly Seized, Operation Shuts Down,” by Lawrence Abrams, BleepingComputer, 14 May 2021.
“Hackers Breached Colonial Pipeline Using Compromised Password,” by William Turton and Kartikay Mehrotra, Bloomberg, 4 June 2021.
“History of Colonial Pipeline in Timeline - Popular Timelines,” populartimelines.com, 2012.
“How Did FBI Recover Colonial Pipeline’s DarkSide Bitcoins?,” by Mathew J. Schwartz, euroinfosec, 11 June 2021
“How Many Pages in a Gigabyte? A Litigator’s Guide,” by Keheley Paulette, Digitalwarroom.com, 2020.
“How Shape-Shifting Threat Actors Complicate Attack Attribution,” by Cynthia Brumfield, CSO Online, 14
“How the Colonial Pipeline Attack Occurred,” by Claudia Piccirilli, WTW, 21 May 2021.
“How the Colonial Pipeline Became a Vital Artery for Fuel,” By Clifford Krauss, The New York Times, 10 May 20221.
“One Password Allowed Hackers to Disrupt Colonial Pipeline, CEO Tells Senators,” by Stephanie Kelly and Jessica Resnick-ault, Reuters, 9 June 2021.
“OT, ICS, SCADA – What’s the Difference?” 2015. by Graham Williamson, KuppingerCole. July 7, 2015.
“Regulator Proposes $1 Million Fine for Colonial Pipeline One Year after Cyberattack,” By Eduard Kovacs, Securityweek.com, 9 May 2022.
“Return of the Darkside: Analysis of a Large-Scale Data Theft Campaign,” by Snir Ben Shimol, Varonis, 18 March 2021.
“Secret Chats Show How Cybergang Became a Ransomware Powerhouse,” By Andrew Kramer, Michael Schwirtz, and Anton Troianovski, The NYTs, 3 June 2021.
“The Aftermath of the Colonial Pipeline Ransomware Attack of May 7th,” by Diana Panduru, ATTACK Simulator, 28 June 2021.
“The Facts to Know about the Colonial Pipeline Ransomware Attack,” by Votiro, 19 May 2021.
“US Gov Issues Emergency Order While Colonial Pipeline Is Down,” by Kim Zetter, Zero Day, Substack, 10 May 2021.
“US Proposes $1 Million Fine for Colonial Pipeline Ransomware Attack,” by Derek Johnson, SC Media, 9 May 2022.