Application tracking in Wacom tablets.
Dave Bittner: [00:00:03] Hello everyone, and welcome to the CyberWire's Research Saturday, presented by Juniper Networks. I'm Dave Bittner, and this is our weekly conversation with researchers and analysts tracking down threats and vulnerabilities, and solving some of the hard problems of protecting ourselves in a rapidly evolving cyberspace. Thanks for joining us.
Dave Bittner: [00:00:25] And now a word from our sponsor, Juniper Networks. Organizations are constantly evolving and increasingly turning to multicloud to transform IT. Juniper's connected security gives organizations the ability to safeguard users, applications, and infrastructure by extending security to all points of connection across the network, helping defend you against advanced threats. Juniper's connected security is also open, so you can build on the security solutions and infrastructure you already have. Secure your entire business, from your endpoints to your edge, and every cloud in between with Juniper's connected security. Come see Juniper at RSA 2020 in Booth 6161 to see why NSS Labs says Juniper is back in security. And we thank Juniper for making it possible to bring you Research Saturday.
Dave Bittner: [00:01:19] Thanks also to our sponsor Enveil, whose revolutionary ZeroReveal solution closes the last gap in data security: protecting data in use. It's the industry's first and only scalable commercial solution, enabling data to remain encrypted throughout the entire processing lifecycle. Imagine being able to analyze, search, and perform calculations on sensitive data, all without ever decrypting anything – all without the risks of theft or inadvertent exposure. What was once only theoretical is now possible with Enveil. Learn more at enveil.com.
Robert Heaton: [00:01:59] Well, I had one of these Wacom tablets for a while, and then I had to reinstall to get it working on a new computer.
Dave Bittner: [00:02:06] That's Robert Heaton. He's a software engineer with Stripe. The research we're discussing today is titled "Wacom drawing tablets track the name of every application that you open."
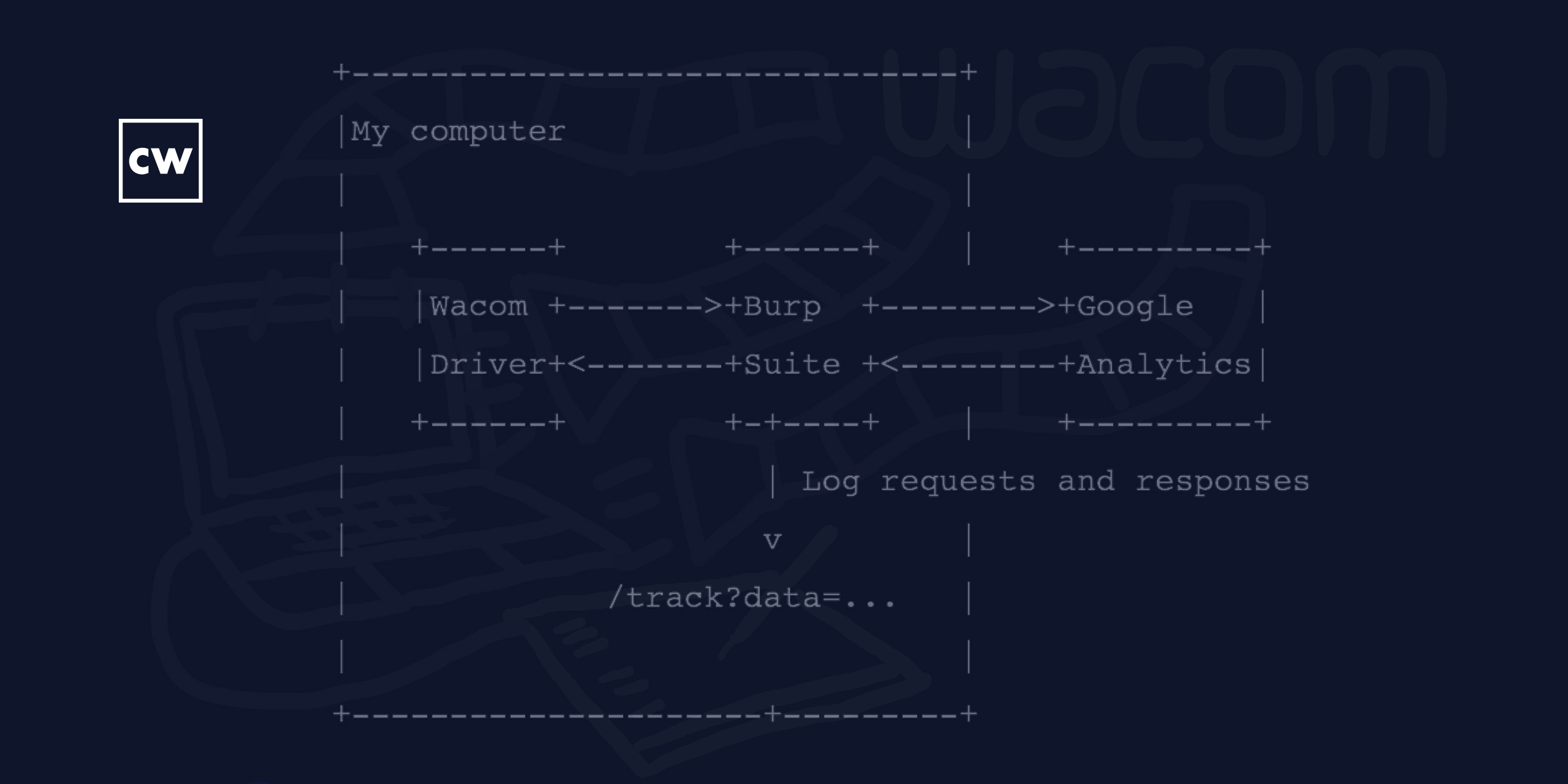
Robert Heaton: [00:02:17] So I downloaded the drivers, I plugged it in, and as I was installing the drivers, it said, please, could you accept our privacy policy? And I found that quite surprising, because a tablet is essentially a mouse. So, I was like, well, why does a mouse need a privacy policy? So, I know no one ever actually reads these things, but I did. And to be fair, it was quite clear – sort of in the standard of these kinds of things. But it said, we sort of want to send a bit of information to Google Analytics, it's not very much, don't worry. And so I was like, hmm, this seems worth looking into. So I did. It was quite simple to do. I just set up a proxy to route the traffic through a program called Burp Suite so that I could have a look at the information. And as I wrote, it turned out that they were sending, most interestingly, the name of every program that I opened, that I tabbed to, which I found quite surprising.
Dave Bittner: [00:03:10] Yeah, I mean, let's dig into that. I think, like you, on the one hand, I think I would be surprised that something like a tablet like this – as you say, similar to a mouse – would require some sort of privacy statement. I suppose, on the other hand, it doesn't surprise me that anything has a privacy statement these days in the world we live in. Is that your sense as well?
Robert Heaton: [00:03:33] I suppose so. But I still did find it quite jarring. I think I would say if it didn't connect to the Internet in any way and didn't send any information anywhere – I'm very much not a lawyer – but I would expect it not to need one.
Dave Bittner: [00:03:49] Well, let's go through some of the details of how you were able to see what exactly they were sending home.
Robert Heaton: [00:03:55] Sure. Using a technique and a tool called a proxy – and it just means that instead of having the traffic go directly from the program, from the Wacom driver to their servers, I instead said, OK, could you please just send it via something, a program that I was running on my local computer. As I mentioned before, this program is called Burp Suite. So, the way you use it is you start Burp Suite on your laptop or your computer, and you say, OK, listen on localhost – just locally on the computer – on a port. It doesn't really matter what port. And then you tell your system in this case, just saying, OK, could you send all HTTP or HTTPS traffic via this proxy?
Robert Heaton: [00:04:42] So, that means that, again, instead of sending traffic directly to Wacom or to Google Analytics, the driver, because it was well-behaved, it respected these settings. It would send that traffic to Burp Suite, and Burp Suite could log it, just to the screen so that I could see what it was, and then it would just send it off to the place where it was originally intended to go.
Robert Heaton: [00:05:02] One sort of other interesting thing you have to make sure to get right here is because this traffic is TLS encrypted, that means that the Wacom driver is expecting to receive a TLS certificate, it's called – that is valid for www dot – I think it's google dash analytics dot com. And obviously, because I'm not Google, I don't have that kind of certificate available, so you have to self-sign a certificate, meaning you generate a fake authority who is allowed to sign these things, you tell your computer it's okay, trust certificates that come from this authority, and then you tell Burp to present this certificate. So, the Wacom driver receives this certificate that is signed by your sort of fake certificate authority, but it's fine with that. It says, okay, this looks great, I'm happy to complete a TLS connection with you, and then everything proceeds as I described it before.
Dave Bittner: [00:05:59] And so, in terms of the information that was being sent back and forth, what sort of view did you have into that?
Robert Heaton: [00:06:05] You could just see the exact contents of the HTTP requests that were going out to Google Analytics, which, as I said, the most – so you could just see the exact data that was going. Though, as I said, the most interesting part was very much these – the names of the programs that you were tabbing to.
Dave Bittner: [00:06:25] I suppose, on the one hand, I could see a company like Wacom being able to use this sort of information. I could see them saying, well, we want to make sure that our product works with a variety of software packages out there, and one of the best ways for us to do that is to know what people are using our products with, so that we don't end up having a bunch of people using something that we haven't tested for. I can see that being a reasonable explanation from their point of view, but still raises some flags for you.
Robert Heaton: [00:06:56] Yeah, exactly. I mean, I absolutely believe that that was the purpose behind this, and that it's not like they were getting this data and then doing something evil or horrendous with it – that they did just want to know how their product works, and that's sort of a natural thing to want to do. I feel like that just doesn't give you the right to take this information. This is still surprising information that people were quite unhappy that was being taken from them. And I think something that I was thinking about is that it's almost unfortunate for Wacom that their product, in its natural state, the natural way that it works doesn't require them to send these HTTP requests. If you were just, like, some kind of SaaS product – like, I don't know, Asana or Trello or literally anything – then, in order to use your products, the users have to send you data. They have to tell you what they want, how they want to interact with your product, so you get this usage information automatically. And it's almost just unfortunate for Wacom the product doesn't require that. So when they try and do that, it seems surprising and jarring.
Dave Bittner: [00:08:02] Now, with the tools that you were using, would it have been within your capabilities to simply shut off the flow? To interrupt that data being sent back to them?
Robert Heaton: [00:08:12] Yeah, certainly. There are several ways to do that. I mean, and again, to Wacom's credit – I very much things is not something they should do – but to their credit, it's something you can just turn off in the driver settings, you can say – I think it's called the "Wacom Experience Program" – I don't want to participate in this. And if you click "No," as far as I know, I'm sure it just stops sending this data.
Robert Heaton: [00:08:34] But then, alternative ways, if you didn't trust that, or you wanted something more sort of broad and far-reaching, you could, for example, probably the easiest way is if you use something like – a device or software called a "Pi-hole," that I believe you put on your network and you do your DNS resolutions via that. So, DNS is when you, say you want to talk to a domain – say Google Analytics dot com – your computer, or the Internet backbone, it doesn't really understand domain names. It doesn't say, okay, I'm going to route this to Google Analytics dot com – it only understands IP addresses. So in order to send data to Google Analytics, first your computer does a DNS lookup. It asks a DNS server, what is the IP address for this domain? And then it will say, oh, it's 152 dot 14 dot whatever. And I believe the way that these kinds of devices work is that you send your DNS requests via them. Which means that it can either send the request onto a real DNS server to get a real response, or it can just black-hole it and say, I'm going to throw this away or just return gibberish or something like that. And that would mean that your entire computer or potentially any device on your network would be unable to figure out where on the Internet Google Analytics dot com is, which means that none of them would ever be able to talk to it.
Dave Bittner: [00:09:53] Now, when you posted this blog post, did you expect to get the attention that you've gotten here? There's been quite some widespread light shown on what you discovered.
Robert Heaton: [00:10:05] I actually sort of did. I felt like I've found a couple of things like this in the past which have all been quite – received similar sorts of interest. And I think my favorite one was, I think a year or two ago, which was another Chrome extension called "Stylish," which is – it was a wonderful Chrome extension where you could add custom CSS rules to change the way that different websites look. Except – and it was just wonderful. It means you could hide distracting bits of Facebook or change the color of a background or something like that. But at the same time, it just secretly logged the URL – the full URL – of every single website that you visited and sent it back to their servers and nefarious tracking reasons.
Robert Heaton: [00:10:49] And so, this was something I discovered just by chance, and I wrote about it and published it. And that was – it was a very similar reaction, where people were just sad and upset that this thing they liked was taking data from them. I think that is much more nefarious, in my opinion, than what this Wacom product is doing, but I think it's something that people find suspicious and don't like and get upset when they find out what's happening.
Dave Bittner: [00:11:15] Has there been any response from Wacom themselves?
Robert Heaton: [00:11:18] I think they did write a blog post that I actually only found recently, just explaining basically what you were suggesting before, where they're saying, well, look, we just want to know how our device is used, it's all anonymous, et cetera, et cetera. Which, again, I get it. It's fair enough. But I just don't – I still don't think it gives you the right to take this data like that.
Dave Bittner: [00:11:40] Ideally, how would you like to see them set this up? What would be a way for them to do this that you would find acceptable?
Robert Heaton: [00:11:49] Shortly after I published this, I installed – I actually set up a new iPhone, and as part of that installation process that you set up your name and email address and all of that. And then there's a very big screen that says, do you want to send analytics data to Apple? And I think it tells you something about what that might involve. And you can just click, "yes, I do" or "no, I do not." And that's it. That's the end of it. And I think that that was quite pleasantly clear – I understood that. I felt like, well, I personally never send people data like that, but I could see someone saying, well, actually, I'm happy to send this stuff if it makes products better.
Dave Bittner: [00:12:25] So that sort of thing, rather than, I suppose, you know, burying it within an end-user license agreement – to be overt about it and really require some sort of an acknowledgement or a response from the user – that's the sort of thing that that you find more appropriate?
Robert Heaton: [00:12:43] I think so. And in this situation, to be fair, again, installing the driver, it did require you to say, yes, I would like to join the Wacom experience program, but it's – no one really knows what that is. To me, it looked like something you had to click "yes," otherwise the product just wouldn't work. Which is not true – you could click "no." But it very much didn't look like that. It was very unclear.
Robert Heaton: [00:13:05] In fact, someone said to me, oh, well, if you're interested in this, you'll be interested in – I think it was the Logitech mouse that does something very similar. So I got all excited, I downloaded some Logitech drivers, and I started installing them. And they actually did exactly what I just described for Apple, where they said – they had one big screen saying, is it okay if we send analytics to ourselves? You can click "no" if you want, and that's fine. And again, it was quite open upfront. And so it kind of – I think that's a good way to approach it, although in that situation it did spoil my fun.
Dave Bittner: [00:13:38] It really is interesting how it seems as though as awareness of these sorts of things increases, there's more subtlety here – the things that people find acceptable versus what they don't, what they find just creepy. It seems like we're establishing what the norms should be, where we're starting to settle in on what people are willing to accept and are not.
Robert Heaton: [00:14:03] I think so. I think it's generally fair enough for an application or a device to record some information of some sort about the way that you use it, specifically – not how you interact with other things on your system or anything like that, but just the way that you use it. I personally, again, given a choice, I don't give anyone any of this information. But I think at that point, it's sort of fair enough.
Robert Heaton: [00:14:28] But then, I sort of think about it where I feel like this Wacom case is quite convenient, where it was very easy to find. It was even in their terms of service and it was very surprising and upsetting to people. But if you think about the data that the much larger companies and more ubiquitous ones, like Facebook and Google and so on, are collecting, that's much harder to track. You can't sort of just put a proxy on your computer and then say, aha! I've got you. Now I can write a blog post that will get everyone very interested and so on. It's instead maybe sort of purchasing some data from over here, or they're getting this data and joining up from two different products that – and you use both on their services. So, it's almost more concerning, I think, and has more impact, but it's harder to pinpoint and harder to reason about because it's much murkier.
Dave Bittner: [00:15:18] What is your advice for people who feel like they want to have a better view into these sorts of things in their day-to-day, to have a sense for what's being collected? Do you have any tips for folks?
Robert Heaton: [00:15:31] I would suggest just start by if something asks for access to something I did, I personally just almost always click "no" until there's some very useful reason for it. If you want to access my contacts, no, if you want to access the camera, no. And eventually, maybe if you prove your reliability and trustworthiness and usefulness, then maybe we can start sharing some information there.
Robert Heaton: [00:15:54] No matter what you think about the sort of economic trade-offs of using ad blockers, I think it's just – I think you just have to use ad blockers at the moment to stop yourself getting tracked as much all around the Internet.
Robert Heaton: [00:16:09] I've noticed recently that – I don't know if this is a new thing, but the large social media companies like Facebook and Twitter have these pages where you can view the information that they – or at least some of the information that they have on you. Which is quite eye-opening. I think there's actually a lot that they don't show you as well, but it shows you, for example, what companies have given them your email and then said, oh, yeah, this person's my customer, or what companies have sent Facebook additional information about you. And that's just quite interesting, if nothing else.
Dave Bittner: [00:16:42] Yeah, yeah, it really is. It's eye-opening, I think.
Robert Heaton: [00:16:45] Indeed.
Dave Bittner: [00:16:46] Yeah.
Robert Heaton: [00:16:47] It's always just a trade-off with these things, I feel, between the amount of effort you're willing to put in to get a particular kind of reward. And that's particularly difficult here, because the rewards are so vague and amorphous and difficult to evaluate. Like, if you were willing to use disposable email addresses for everything and maybe you used Tor for everything as well, then your life will be harder, but you'll also be tracked less across the Internet. So it's whether that's a worthwhile trade-off for you.
Dave Bittner: [00:17:20] That's Robert Heaton. He's a software engineer with Stripe. The research we discuss today is titled "Wacom drawing tablets track the name of every application that you open." We'll have a link in the show notes.
Dave Bittner: [00:17:35] Thanks to Juniper Networks for sponsoring our show. You can learn more at juniper.net/security, or connect with them on Twitter or Facebook.
Dave Bittner: [00:17:43] And thanks to Enveil for their sponsorship. You can find out how they're closing the last gap in data security at enveil.com.
Dave Bittner: [00:17:51] Funding for this CyberWire podcast is made possible by RSA Conference, where the world talks security. Through global events and year-round content, RSAC connects you to cybersecurity leaders and cutting-edge ideas for a safer, more secure future. Learn more at rsaconference.com.
Dave Bittner: [00:18:10] The CyberWire Research Saturday is proudly produced in Maryland out of the startup studios of DataTribe, where they're co-building the next generation of cybersecurity teams and technologies. Our amazing CyberWire team is Elliott Peltzman, Puru Prakash, Stefan Vaziri, Kelsea Bond, Tim Nodar, Joe Carrigan, Carole Theriault, Ben Yelin, Nick Veliky, Bennett Moe, Chris Russell, John Petrik, Jennifer Eiben, Peter Kilpe, and I'm Dave Bittner. Thanks for listening.


