TLS is here to stay.
Dave Bittner: [00:00:03] Hello everyone, and welcome to the CyberWire's Research Saturday, presented by Juniper Networks. I'm Dave Bittner, and this is our weekly conversation with researchers and analysts tracking down threats and vulnerabilities, solving some of the hard problems of protecting ourselves in a rapidly evolving cyberspace. Thanks for joining us.
Dave Bittner: [00:00:25] And now a quick word about our sponsor, Juniper Networks. NSS Labs gave Juniper its highest rating of "Recommended" in its 2019 Data Center Security Gateway Test. To get your copy of the NSS Labs report, visit juniper.net/SecureDC, or connect with Juniper on Twitter or Facebook. That's juniper.net/SecureDC. And we thank Juniper for making it possible to bring you Research Saturday.
Dave Bittner: [00:00:55] Thanks also to our sponsor, Enveil, whose revolutionary ZeroReveal solution closes the last gap in data security: protecting data in use. It's the industry's first and only scalable commercial solution enabling data to remain encrypted throughout the entire processing lifecycle. Imagine being able to analyze, search, and perform calculations on sensitive data, all without ever decrypting anything – all without the risks of theft or inadvertent exposure. What was once only theoretical is now possible with Enveil. Learn more at enveil.com.
Chester Wisniewski: [00:01:34] It's one of these well-known secrets, if you will. If you talk to anybody in the business that researches malware, we've all seen bots that communicate back to their command-and-control using encryption.
Dave Bittner: [00:01:45] That's Chester with New Scheme. He's a principal research scientist at SophosLabs. The research we're discussing today is titled, "Nearly a quarter of malware now communicates using TLS."
Chester Wisniewski: [00:01:57] We've seen stolen certificates. We've seen, you know, malware that's signed with certificates. We've seen all this stuff, but nobody had really quantified it. And so we thought, well, we all anecdotally know it's a problem, but how big of a problem is it? And, you know, maybe we should take a look with all the data we have in our labs.
Dave Bittner: [00:02:14] Well, the research that you published here starts off with a really nice overview of some of the basics here. I'd love to go through that together, because I know there are a lot of people who might be a little fuzzy on some of this stuff. Can you take us through some of the backstory here when it comes to TLS and sort of the foundational elements of that?
Chester Wisniewski: [00:02:33] Sure. I mean, of course, TLS – we're using the correct modern terminology, but I think a lot of people still think of TLS as being the good old SSL that represented their padlock on Netscape Navigator back in the 1990s.
Dave Bittner: [00:02:45] Right.
Chester Wisniewski: [00:02:46] So, the current terminology is TLS. SSL is now discontinued. And you know, it's public-private key cryptography that's used to protect most of what we do via email and the web these days on the Internet. Actually, I think that might be an interesting side project to look at how much of the how much email is currently being transmitted using TLS for, you know, for the good stuff to be protected. But I think I think Google may have done some research on that.
Dave Bittner: [00:03:09] Hmm.
Chester Wisniewski: [00:03:09] But, you know, the idea here is, of course, to provide encryption while in transit, right? So, this is different than the kind of encryption you might use to protect a file on disk or protect the SSD in your laptop in case it gets stolen. This encryption is just while things are being transmitted from, typically, a web server to a client. And we're just seeing that the criminals are starting to adopt this for their own transport to protect their communications.
Dave Bittner: [00:03:34] And I suppose there are two sides to this story. The good part is that this data is encrypted, but that can make things harder to examine as well.
Chester Wisniewski: [00:03:43] Yeah, ironically, if your information is being stolen by criminals, at least only one criminal will be able to see the information that they're stealing from you, unlike if they do it unencrypted, and you're at, you know, Wi-Fi at the Starbucks or something. But obviously, the challenge really for enterprises – or even home users, for that matter – is you need to be able to man-in-the-middle that traffic in order to inspect it to find out whether it's malicious or not. And I think most people in their minds connect privacy and security as being compatible or together. And this is one of those cases where they're actually incompatible, right? I have to actually break into that secure connection to look at the content to know whether it's safe for you to consume that content. Yet by doing so, in a way, I'm affecting your privacy.
Dave Bittner: [00:04:26] And at the enterprise level, there are tools available to do just that.
Chester Wisniewski: [00:04:30] Absolutely. Most modern firewalls have the ability to, you know, man-in-the-middle that traffic – in essence, they decrypt the traffic before it goes out to the criminals, take a look at what's inside of it, and if it's OK, let it pass with a new encrypted connection to the criminal or to whatever. Obviously, hopefully not the criminals – maybe it's you going to log into your Twitter or your Facebook or your bank. But I think one of the adoption challenges for enterprises has been, to do that – because you're gonna get into this protected connection – you have to deploy certificates. You have to deploy a private certificate authority certificate to all of the computers that are behind that firewall. And doing that in a large environment is quite a cumbersome activity.
Dave Bittner: [00:05:12] And the availability of those certificates, I mean, that it's not a difficult thing to do these days.
Chester Wisniewski: [00:05:18] Yeah. You actually make a certificate on your own. You don't need to actually purchase one. In fact, you can't purchase one. The companies like Verisign are not allowed to issue one that everybody in the world would trust. So you actually make an untrusted one of your own and then you tell all your computers to trust it. And it's telling all the computers to trust it that's the challenging part.
Dave Bittner: [00:05:39] Now, one of the things that you track here in your publication is this shift that you've seen with more functions from the malware being orchestrated on the command-and-control server side. Can you give us some insights there?
Chester Wisniewski: [00:05:53] Yeah. The initial infection is often called a downloader or even – you can think of it as maybe a little bit of a stub. Meaning the malware that comes down your computer doesn't even know what it's going to do until the criminals kind of know who's been infected, if you will. So, the idea is they might want to turn you into a DDoS bot. They might want to turn you into – they might want to ransom you. Maybe they want to use you to send some spam. They're not really sure until they determine who you are.
Chester Wisniewski: [00:06:18] Now, we don't really know why necessarily criminals decide to use one malware one place, or one malware in another. But I did some research that I presented at RSA Conference a couple years back that talked about this. And we had found that things like maybe you've got a banking Trojan that's targeting a German bank. Well, you probably don't want to install that on machines in Singapore. You probably only want to install it on computers in Germany. So, that's in essence what's happening. It's like you get infected with a little piece of code that just calls home and goes, what do I do? And then the malware controller decides, OK, I want you to load up this banking Trojan, I want you to load up this ransom code.
Dave Bittner: [00:06:54] And so, is the notion here that the less traffic that's being sent back and forth, the more under the radar these actors can stay?
Chester Wisniewski: [00:07:02] Well, the less traffic that's out there, that certainly is the case. In this case, I don't think they're doing it for stealth reasons. I think they're doing it to maximize their profit. You know, the malware ecosystem has broken down into a lot of specialization over the last fifteen years, and because of that specialization, there's people that specialize just in infecting people's computers initially, and then seem to sell them on to other criminals to do criminal activity that's more specialized and focused, like, you know, banking malware and ransomware, as examples.
Chester Wisniewski: [00:07:30] Many of your listeners may have heard of Emotet, which has probably been the biggest email malware threat we've seen in the last couple of years. And Emotet is one of those. You know, once you get infected with Emotet, it might then install Trickbot or it might install Dridex. It's going to install something based on some other criminal paying them for your head. And they may pay them based on your geographic location, they may pay them based on – maybe you're on a Mac instead of a PC and they need to deploy different malware. Those types of things happen in these attacks so that the criminals can sort of maximize the profit per victim.
Dave Bittner: [00:08:01] Hmm. Well, the research that you've published here, you go through some of the recent malware campaigns and sort of break down and track who's using TLS here. Share with us what you found.
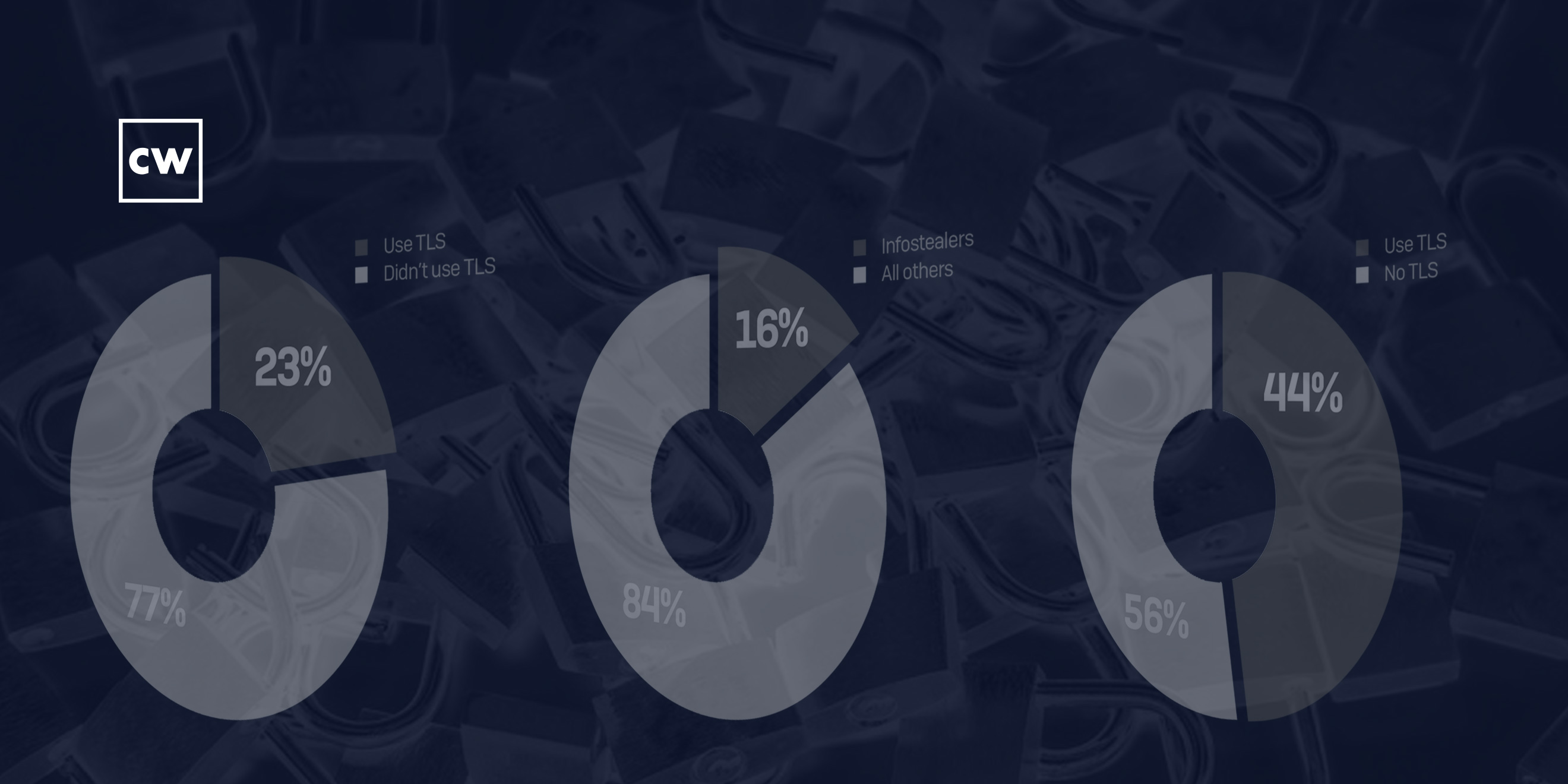
Chester Wisniewski: [00:08:14] We took a handful of families that we thought were representative, because it's – obviously with the quantity of malware we deal with in the lab, it's impossible for us to, you know, go through every sample and get an exact number. So we thought we would take a couple of these sample families and go through them and analyze them. So we took ones that are known infostealers and then just other ones that are just common Trojans that we see. So we looked at IcedID, we looked at Dridex, and we looked at Trickbot. And those are three very common malware families that we're seeing in the wild right now. And then we analyzed six months worth of their samples in our dataset to see how frequently they were using TLS.
Dave Bittner: [00:08:52] Well, let's go through them one at a time together. Why don't we start with Trickbot.
Chester Wisniewski: [00:08:55] Right, so, Trickbot, you know, most commonly right now, I think the way people are seeing it pop up on their computers is when it deploys a secondary payload again, like we were just talking about. So, Trickbot itself is an information stealer, and that, you know, is not necessarily limited to what it can steal. I mean, it can steal information from your browser, or, you know, maybe looking to steal information from your browser that's related to banking. One of its other characteristics that we've seen is that it also can deploy ransomware for other crooks. So it's sort of like taking two bites of the apple when it gets you as a victim.
Chester Wisniewski: [00:09:30] And so, obviously, what we were curious about is, you know, does it use encryption? And of course, it does occasionally use encryption, and what's kind of interesting about it – the criminals are quite smart, Rather than having to implement their own encryption, let's say, they actually use the built-in CryptoAPI inside of Windows to do their encryption. So, I guess that sort of to ensure that they don't screw up the encryption.
Dave Bittner: [00:09:55] (Laughs) So they're relying on someone else's expertise of cryptography there.
Chester Wisniewski: [00:09:59] Yeah. Yeah, exactly. And you know, like I said, they're kind of part of this malware supply chain. With Trickbot, we often see that the victim initially gets hit with an attack, which is one of these ones that comes in via email that says, you know, you have an invoice or DHL has a package waiting or, you know, these types of messages. And then they – Trickbot is probably paying the Emotet group to install their malware. And then after Trickbot's on there, occasionally we'll see Trickbot then install some ransomware as well.
Dave Bittner: [00:10:26] Hmm. Well, let's take a look at IcedID. What did you see here?
Chester Wisniewski: [00:10:30] Yeah. So, the IcedID one, you know, they also – none of them always used to TLS, but in this case they did use TLS. It was kind of interesting to us that they were using the RC4 cipher. So RC4 is a very old cipher and it's not terribly difficult to break, depending on how it's implemented. And that was interesting to see. And it does have the ability to send stuff unencrypted. Some of the – you know, a lot of these seem to be able to do both encrypted and unencrypted information transmission.
Chester Wisniewski: [00:11:03] And that's not – you know, it's not clear what the purpose of that is. In case, maybe, they're in some environments where they can't make an encrypted connection back, or it might just be a fallback mechanism. You know, we talked about certificates a minute ago. You know, there's been many a famous website to forget to renew a certificate. I think even – I want to say Microsoft had an incident a couple of months ago where they forgot to renew a certificate. So, it's possible that criminals are like, well, maybe we – what if we forget to renew our certificate for, you know, we don't got to stop getting stolen data.
Dave Bittner: [00:11:29] (Laughs)
Chester Wisniewski: [00:11:30] So, you know, maybe it's a fallback mechanism. I'm not really sure why, if you bothered to go through the trouble of implementing cryptographic APIs, why you would have unencrypted capability. But a lot of them seem to do have both and only occasionally use the encryption.
Dave Bittner: [00:11:45] Oh, interesting. Interesting. And then the last one that you analyzed here is, I suppose, an oldie but a goodie, and that's Dridex.
Chester Wisniewski: [00:11:53] Yeah. Dridex is another one that these days most often gets onto your computer through the Emotet botnet. It is old, as you say. I think, you know, we first saw a Dridex back in 2011. And so, it's gotten around a bit. And that's another reason I think we see some of this variability where we go, hey, it looks like Dridex uses TLS, but we also have Dridex samples that don't use TLS. And like IcedID, it's also using the old RC4 encryption. The, you know, the variability in that I think is partly related to how old some of these malware families are, right? There's different people that have copied it and reused it, and, you know, maybe some of the old ones don't have this secure capability while newer copies of the malware do have the secure capability. And so that's why we only see, you know, a portion of the traffic using encryption.
Dave Bittner: [00:12:45] What are you tracking in terms of trending here? Are we seeing more and more of the use of TLS when it comes to these folks?
Chester Wisniewski: [00:12:53] Well, being that this is one of the few reports that have been out there, and it's the first report we've published from samples at SophosLabs, which means we have nothing to compare it to, it's all anecdotal. Certainly, anecdotally, it seems like we're seeing increasing use, especially amongst things that are stealing information. We know that a lot of companies are very carefully looking at data that's exfiltrated through their firewalls to try to remain compliant with regulations like GDPR and of course in the USA we have CCPA, so that means companies have a better chance of noticing those credit cards being stolen or those passwords being stolen or, you know, that kind of thing. So it's possible the criminals are using this for information stealers, sort of as the vanguard of the whole thing.
Chester Wisniewski: [00:13:34] In our research we saw that 44 percent of information stealers are using encryption, and that is, you know, a higher percentage than we see amongst the malware community as a whole, which is about 23 percent. So, it's almost twice as likely that an information stealer is going to use encryption than a regular good old-fashioned bot. So, that's probably indicative of the criminals trying to bypass corporate policies.
Dave Bittner: [00:13:58] So, what sort of recommendations do you have for people out there to contend with this stuff?
Chester Wisniewski: [00:14:03] Well, I think, you know, for everyday users at home, there's little that can be done other than to run good-quality endpoint protection on their computers that hopefully keeps track of a lot of these command-and-control servers and can block access to them. I mean, some of them do some TLS interception as well, so consumers would have to kind of survey the market a bit for that. But on the enterprise side, I think it's clear that we need to be inspecting encrypted traffic traversing our firewalls. And if you haven't taken on that project yet, you need to take it on. You know, there's different products out there that work differently depending on what brand of firewall or next-generation UTM or firewall that you have on your network. But most of them have this capability. And if you're using one that doesn't, it's probably time to shop around, because this is going to become increasingly important.
Dave Bittner: [00:14:54] That's Chester Wisniewski from SophosLabs. The research is titled, "Nearly a quarter of malware now communicates using TLS." We'll have a link in the show notes.
Dave Bittner: [00:15:04] Thanks to Juniper Networks for sponsoring our show. You can learn more at juniper.net/security, or connect with them on Twitter or Facebook.
Dave Bittner: [00:15:13] And thanks to Enveil for their sponsorship. You can find out how they're closing the last gap in data security at enveil.com.
Dave Bittner: [00:15:21] The CyberWire Research Saturday is proudly produced in Maryland out of the startup studios of DataTribe, where they're co-building the next generation of cybersecurity teams and technologies. Our amazing CyberWire team is Elliott Peltzman, Puru Prakash, Stefan Vaziri, Kelsea Bond, Tim Nodar, Joe Carrigan, Carole Theriault, Ben Yelin, Nick Veliky, Bennett Moe, Chris Russell, John Petrik, Jennifer Eiben, Peter Kilpe, and I'm Dave Bittner. Thanks for listening.


