It was only a matter of time.
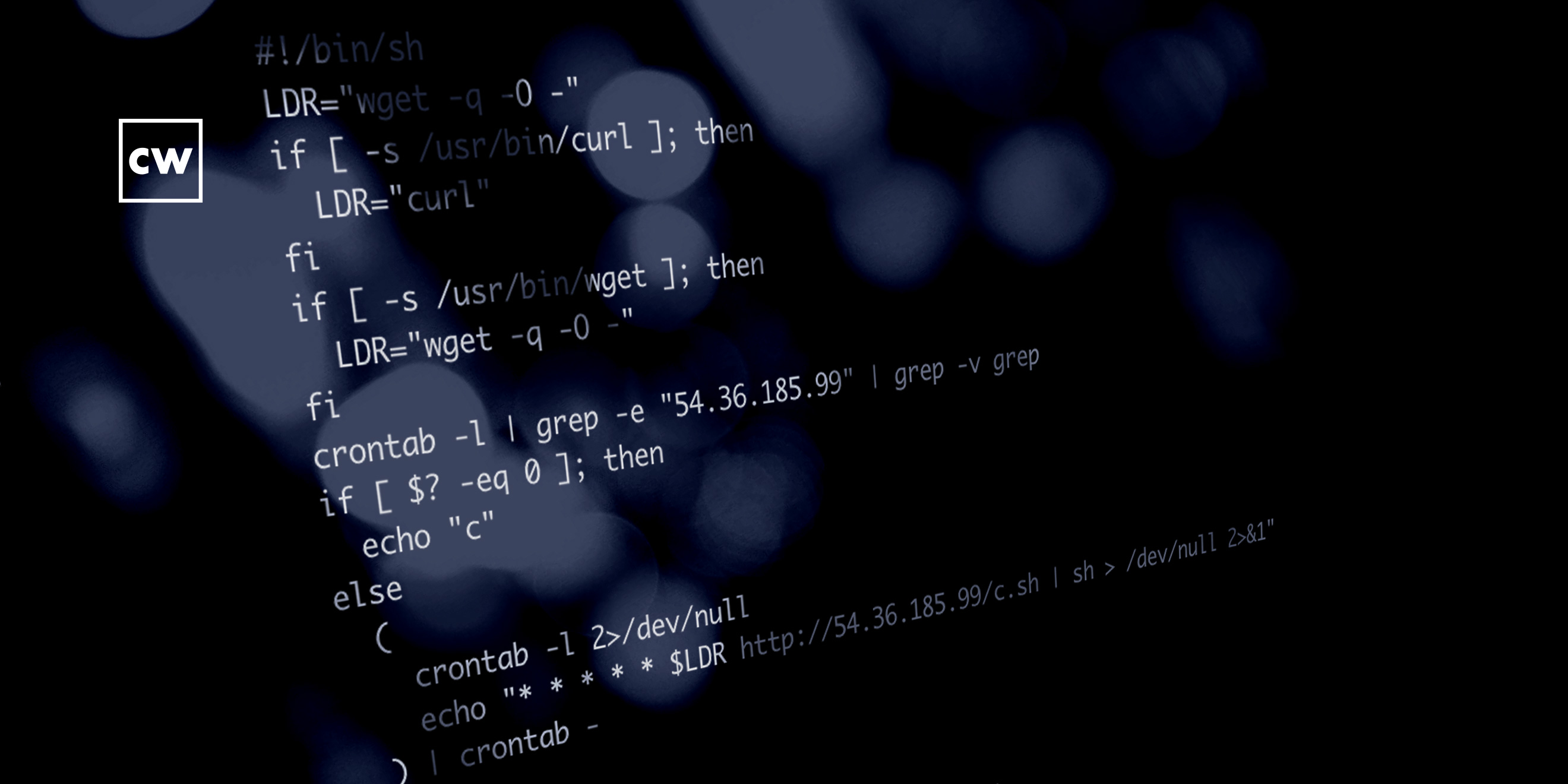
On April 29, 2020, the Salt management framework, authored by the IT automation company SaltStack, received a patch concerning two CVEs; CVE-2020-11651, an authentication bypass vulnerability, and CVE-2020-11652, a directory-traversal vulnerability.
On April 30, 2020, researchers at F-Secure disclosed their vulnerability findings to the public, with an urgent warning for Salt users - patch now. Before the weekend was out, criminals were deploying malware and targeting vulnerable Salt installations, successfully affecting operations at Ghost, DigiCert, and LineageOS. The malware is a cryptominer, but there is an additional component, a Remote Access Tool written in Go called nspps. Researchers at Akamai have also observed in-the-wild attacks on Salt vulnerabilities.
Joining us on this week's Research Saturday is Larry Cashdollar, Senior Security Response Engineer at Akamai, to discuss this issue.
The research can be found here:



