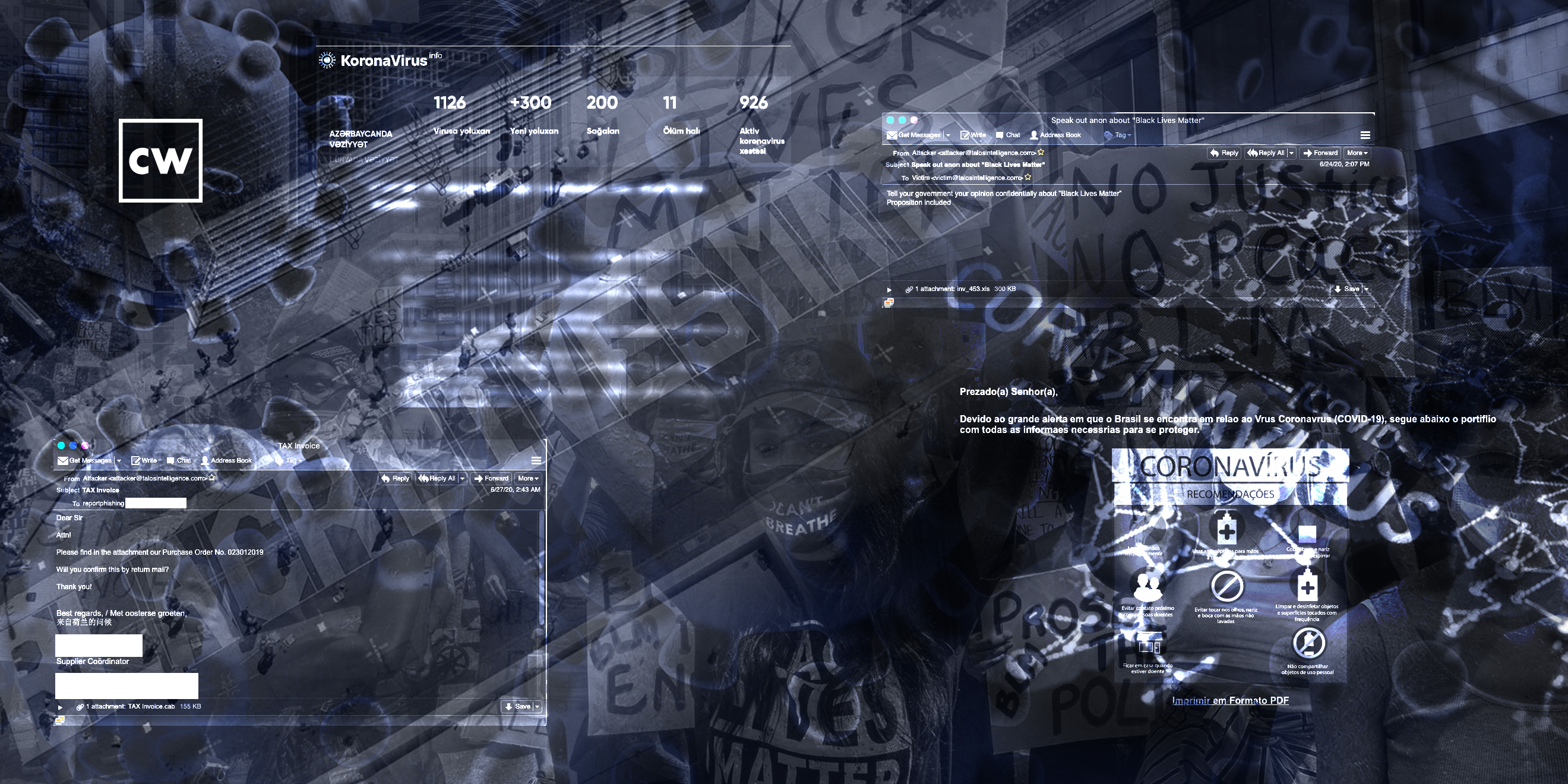
Using global events as lures.
Dave Bittner: Hello everyone, and welcome to the CyberWire's Research Saturday. I'm Dave Bittner, and this is our weekly conversation with researchers and analysts tracking down threats and vulnerabilities, solving some of the hard problems of protecting ourselves in a rapidly evolving cyberspace. Thanks for joining us.
Craig Williams: Well, I think what really prompted us to take this on is the fact that we see certain patterns repeated in this business over and over and over again.
Dave Bittner: That's Craig Williams. He's the Head of Talos Outreach at Cisco. The research we're discussing today is titled, "Adversarial use of current events as lures."
Craig Williams: You know, I mean, at this point, I think I can even say it rounds up to I've been doing this twenty years, and we see different and new malware campaigns every week. Right? There's always someone doing something new, tweaking something, finding a new way to do it. But in doing so, there are certain patterns that are always habitually followed.
Craig Williams: And really, when you look at it, probably the most effective one is bad guys trying to find a way to use current events as lures. And I know that sounds really open-ended, and people think, well, how could that possibly help me? And that's kind of the reason we wrote this blog, was to not only highlight what we're seeing, but to help people understand what could be used in the future. So, you know, if we sit back right now and take a high-level look over the next six months, you know, we see a lot of social issues at play. We see an election coming up. We see the typical holiday shopping season. And then after that, we start seeing tax season in the US. Right? I would expect malware campaigns to target each and every one of those in order, and, you know, potentially a couple of them overlapping.
Dave Bittner: Right. Yeah, it's interesting to me that one of the things you highlight here is that there are the ones that sort of run on the calendar, the tried-and-true every holiday season we're going to have stuff. Every tax season, we're going to have stuff. But then in addition to that, you know, we've got things like COVID-19. We've got things like Black Lives Matter. These things that are top of mind and also emotional hot points for a lot of people.
Craig Williams: Absolutely. And you touched right on the thing that they're trying to exploit, right? They want you to hear this topic, they want you to read this topic, see it, and your emotion kicks in. When people are thinking with emotion, they don't necessarily have the same thought that, say, an email would go through, right? And so, by putting in these emotionally charged topics, they're trying to find someone who's going to impulsively click on it and potentially get exploited without really thinking it through, like, hey, would Steve really send me a link on this Black Friday sale for patio cushions, for example?
Dave Bittner: (Laughs)
Craig Williams: Let's assume Steve feels strongly about patio cushions.
Dave Bittner: Yeah. Yeah.
Craig Williams: You know, but anything like that, anything that might be coming up, they will try. And the reality is one percent work. So, ninety-nine percent of people are going to see these and see right through them, right? They're going to see the email with misspellings. They're going to see, oh, it's a Word doc, I know not to open that, or it's a PDF. They're looking for that one percent that will. So, for every single one you see, think about the people that you know in your life that are the least technical. And think about them at their worst possible moment. Maybe they just saw a piece of news that was incredibly inflammatory. Maybe they just had a relative or someone they care deeply about get diagnosed with COVID-19. Right? All of these scenarios are going to influence the way that they click and the speed that they click. And that's really, unfortunately, what the bad guys prey upon.
Dave Bittner: Yeah, you know, it's also interesting to me how it sort of short-circuits, the rational thinking part of people's brains, as you say, and tricks them into acting in a way that they probably wouldn't if they were in a better state of mind.
Craig Williams: Right, and, you know, unfortunately, we see this over and over again. There are regional specific versions. You know, we see a lot of stuff in Asia that's very specific to Asia. It's even been localized in the right languages that would make sense to the people in the regions. It's got, you know, social context that are specific to the region. And so, you know, it's a business now. It's not someone trying to get lucky. It's not someone saying, I'm going to really nail that one person. No – they know they're getting one percent. But the thing is, to send out, you know, two-hundred-thousand emails has a cost that approaches zero.
Dave Bittner: Yeah, and again, you know, to contrast that against some of the other things that we've seen – and I know you and your team track –things like some of these ransomware campaigns we've seen that that have become highly targeted, or some of these business email compromise campaigns that are really specific in who they're after – we still have these sort of, you know, spray-and-pray campaigns that are just running these massive numbers games.
Craig Williams: Absolutely. And unfortunately, you know, they're remarkably effective. And I think probably one of the biggest problems we see with this is the fact that we have so many people who were rushed to work from home who end up with these systems that aren't adequately protected, right? So now you have someone on the corporate network with potentially a laptop from their home, right? And let's say it's a law firm or a bank – we hear a lot of reports about those having to make do because of the shortage of computers, especially at the beginning of the pandemic. You know, they're on these computers that are the same ones that potentially are already compromised, that other people in the household use, connecting to corporate networks. And what we're seeing is ransomware just becoming much more pervasive.
Craig Williams: Now, this is – this is going to sound like good news, but it's not...
Dave Bittner: (Laughs)
Craig Williams: ...You know, we're also seeing, like, the business effectiveness of the actual ransomware campaigns evolving and becoming significantly more stable and more savvy in the way that they deal with victims. I mean, it's tempting to say "customers," because they actually offer levels of support. You know, if you look on Twitter now, you can see example after example of these chat rooms that are posted where it's a very transactional business service that's provided. And I even saw one the other day that had tips – like, security tips – from the malware authors.
Dave Bittner: Right.
Craig Williams: And so, that's how evolved this business has become. It's self-sustaining. It's gone past gang or loose criminal activity into a small business – a small, illegal business that takes advantage of other businesses – but this is now a professional entity with actual support staff behind it, with developers behind it, with hackers behind it. This isn't a one-person operation anymore.
Dave Bittner: Right, right. It's not that old smash-and-grab of breaking of a shop window and running off with as much as you can. Well, let's go through some of the case studies that you all highlight in your research here. You've got a number of examples that you look at. Can you take us through some of them?
Craig Williams: Yeah. So, you know, actually, I'm not even sure if this one made the write-up, but it was one that popped into my head just from a ransomware perspective – and that was the one that we published, I believe, shortly after this. I don't think it's a reference to it, but WastedLocker – it's one of the big-game-hunting pieces of ransomware we saw. And the reason this one jumped out at me, we were discussing it yesterday on one of our team calls. So, this is a fairly sophisticated and successful piece of malware, but the actual interaction done on the victim's machine is done manually.
Dave Bittner: Hmm.
Craig Williams: Right? And so what I mean by that is if you have, you know, endpoint defenses installed and you actually have someone auditing the machine, you can see typos in the command line, and you can see them go back, edit, and correct those typos. It means that they basically have a team that are, I guess, working almost in shift-like work, waiting for the business day to end in the region that they have victims in, and then slowly but surely it will become that victims turn, and a – let's call it a "support person" will go to that system and manually start spreading the malware, putting in the footholds for future compromise, putting in the ransomware, ensuring it gets to the right places on the network. You know, it's gone from, let's try and have a piece of ransomware that just hits everything, to let's have someone sit down with this network and ensure that this ransomware gets into the most valuable places. And presumably, let's also take the time and figure out what we think is a reasonable amount to pay for these machines.
Dave Bittner: Hmm. Now, are there still parts of the process that are automated? – of, you know, getting that initial foothold, determining whether a machine is liable to be breached here?
Craig Williams: There could be some of it. Obviously, we saw the command-line stuff being run and that jumped out at us.
Dave Bittner: Yeah.
Craig Williams: Now, the interesting part about this, and this is why I wanted to make sure we talked about it, is that this is something that you can easily check on your systems. You know, if you go to the WastedLocker blog on your system, you can actually type in – you know, obviously pick one of the benign commands, like maybe the ping sweep – but you can actually pick out some of the commands that the authors were running to recon the network and see if your defenses pick it up, see if your client-based logging picks it up, see if your prevention systems pick it up. And it's surprising, some of the stuff that gets by some systems, especially if they don't have the right defenses in place, which is what we're seeing in a lot of places.
Craig Williams: And so that's kind of why I wanted to bring this up, right? I mean, we're obviously seeing people using all kinds of lures and we're seeing them tuned to emotionally charged events. But we're also seeing ransomware now that is so sophisticated that while they could deploy it automatically with some success, instead they will go in manually by hand and ensure that it gets into the right places, into the most damaging places, into things like domain controllers, into the data center. And they're doing this by hand. So, it's pretty sophisticated and pretty nefarious stuff, unfortunately.
Dave Bittner: So, what are mitigations for this? Are we looking – what sort of specific things should we be on the lookout for?
Craig Williams: Well, there's a couple of things you can do, right? The first one and the one that we always mention – and I know this is right up there with saying "patch everything"...
Dave Bittner: (Laughs)
Craig Williams: ...Is, you know, make sure you have backups. And the most important part of that is make sure you have backups that are not accessible to the machines that are going to get compromised – have off-site if you need to, or have a segment that only turns on for a specific window – something like that. But more importantly, make sure that it scales. Make sure that you can restore an entire building, make sure you can restore an entire department. That's what a lot of people miss, unfortunately.
Craig Williams: I think the second major one is to make sure you're practicing defense-in-depth. Make sure you have segmentation in place where you can. Make sure you're patching everything you can patch. You know, make sure that if you have anything that is known vulnerable, that it is segmented to the absolute maximum amount. Make sure that there is some mitigation in place if it is exposed to other machines. That could be an intrusion prevention system. That could be, you know, a firewall with a very stringent access list, right? Obviously, the more layers, the better.
Craig Williams: And then down on the endpoints themselves, make sure you have some things to try and keep malware off of there, right? Make sure you have the browsers deployed as strictly and tightly as possible. Make sure that you're not allowing people to use shared passwords across all kinds of machines. Rotate your administrator passwords. Minimize the number of people with administrator credentials. Have endpoint security on the device. You know, there's a ton of stuff you can do. And, you know, if you're a business, you should speak to your vendor and find out if you've got enough layers. You're never going to have something that's a hundred-percent hacker-proof, but you can at least make it very difficult for them to cause a large amount of damage. And if you can limit any potential impact to a small number of machines, obviously that's going to be very advantageous and make your recovery process so much easier.
Dave Bittner: What about from the user's point of view of, you know, user-awareness training, of trying to make them less susceptible to respond to these, you know, emotionally charged things that are coming at them?
Craig Williams: I view that kind of like the Holy Grail. (Laughs) You know, it's one of those things that obviously would be great if it worked, should work. But we're kind of in, you know, an emotional cat-and-mouse game of people learning best practices and then adversaries trying to find a way to have people ignore those best practices. And, you know, we're in unprecedented times. We don't have a global pandemic all the time. We don't have severe civil rights issues come to the surface so suddenly and so severely all the time. We don't have people who haven't been outside in, you know, in a major way in potentially weeks or have taken a vacation in weeks, right? People are on edge now, more so than ever before. So, it's easy to say prepare people and teach them, but I think the reality is, right now, no one is operating at their best. Right? People are going to make mistakes. You need to have your network security posture with that in mind. You need to plan on the users clicking on things they shouldn't. The question you should ask yourself is, when the user does do something wrong, what's the worst thing that could happen? What's our playbook for mitigating that? Think it through. Think about what if it's a keylogger? What if it's something that exfiltrating the password hashes in memory? What if it's a piece of ransomware that tries to spread laterally? You know, and so think through those scenarios and have plays for all of those possibilities.
Dave Bittner: Is it possible you could have some sort of analysis tool that's looking at your incoming email, looking for some of these keywords and at the very least putting some kind of a flag on them, that's saying, hey, we've noticed that they're talking about something that, you know, might get your dander up, so just be mindful of that.
Craig Williams: Yeah, I'm pretty sure that's possible. You know, I know we do that a lot with things like COVID-19, right? And several other phrases. We do flag stuff. I think you can even have it put into a separate folder as suspicious, you know, because a lot of the time those types of emails should be sent from specific accounts or maybe to specific people, right? Obviously, you probably shouldn't be getting all your political newsletters at work. So, there's a lot of stuff like that that can also happen, right? I mean, it's a pretty easy decision for the security office to say, hey, you know what? I don't know that anyone should be reading politically charged emails at work, especially if we know they're being used in a malware campaign.
Dave Bittner: Yeah. But if we're co-mingling our computers, you know, our home networks and all that kind of stuff.
Craig Williams: Right, right. Well, and it's a whole 'nother problem with COVID-19, right? You're going to have a significant amount of official emails from your office, probably about COVID-19, and about what the company policy is, how to safely enter and exit offices. So, it's a really complicated situation, and I don't think – and we may never see anything like it again. Which is why I think it's so important that people really take a long, hard look at defense-in-depth and what they've done at every layer. Because mistakes will happen, right? We're humans. They're going to happen. So figure out, if mistakes are made at each layer, what are the other gates that will stop an adversary?
Dave Bittner: Our thanks to Craig Williams from Cisco Talos for joining us. The research is titled, "Adversarial use of current events as lures." We'll have a link in the show notes.
Dave Bittner: The CyberWire Research Saturday is proudly produced in Maryland out of the startup studios of DataTribe, where they're co-building the next generation of cybersecurity teams and technologies. Our amazing CyberWire team is Elliott Peltzman, Puru Prakash, Stefan Vaziri, Kelsea Bond, Tim Nodar, Joe Carrigan, Carole Theriault, Ben Yelin, Nick Veliky, Gina Johnson, Bennett Moe, Chris Russell, John Petrik, Jennifer Eiben, Rick Howard, Peter Kilpe, and I'm Dave Bittner. Thanks for listening.


