Ezuri: Regenerating a different kind of target.
Dave Bittner: Hello everyone, and welcome to the CyberWire Research Saturday. I'm Dave Bittner, and this is our weekly conversation with researchers and analysts tracking down threats and vulnerabilities, solving some of the hard problems of protecting ourselves in a rapidly evolving cyberspace. Thanks for joining us.
Tom Hegel: We came across an interesting loader that was targeting Linux operating systems, and taking a dive into that particular loader and kind of opened the door to kind of an interesting set of events that we haven't quite seen very often.
Dave Bittner: Joining me are Fernando Martinez and Tom Hegel from AT&T Alien Labs. We're discussing malware using the new Ezuri memory loader.
Tom Hegel: The characteristics of that voter were pretty unique.
Dave Bittner: That's Tom Hegel.
Tom Hegel: And then linking it back to certain adversary group really made it stand out as a next-step evolution in that adversary group. So it kind of really captured our attention at that point.
Dave Bittner: Well, let's dig into some of the details here. Let's go through it step-by-step here. I mean, we've got this loader and it's using the Go language tool, which is acting as a packer. Can you give us a little of the technical background on that? For folks who aren't familiar with it, perhaps aren't UNIX folks, what is the Go language and how does that relate to what we found here?
Fernando Martinez: So language is another scripting language that anybody can use.
Dave Bittner: That's Fernando Martinez,
Fernando Martinez: Same as Python, C, or any other. It's just a little bit more complex at the time of decrypting something. But at the time of the scripting, it's supposed to make it easier for you. And so it is a little bit newer than other scripting languages and not so used by the community, but for attackers or somebody developing code, it is useful for them if do not want to have an easy way of decrypting – if they don't want the security researchers to have an easy way of decrypting that code, it is way more efficient because all the libraries are combined together and most of the times many libraries that they don't need are compiled all together and making the research harder for identifying what libraries are inside and what has a malicious purpose or a good purpose.
Dave Bittner: Well, let's go through it together, I mean, walk us through the details of what you found in this loader.
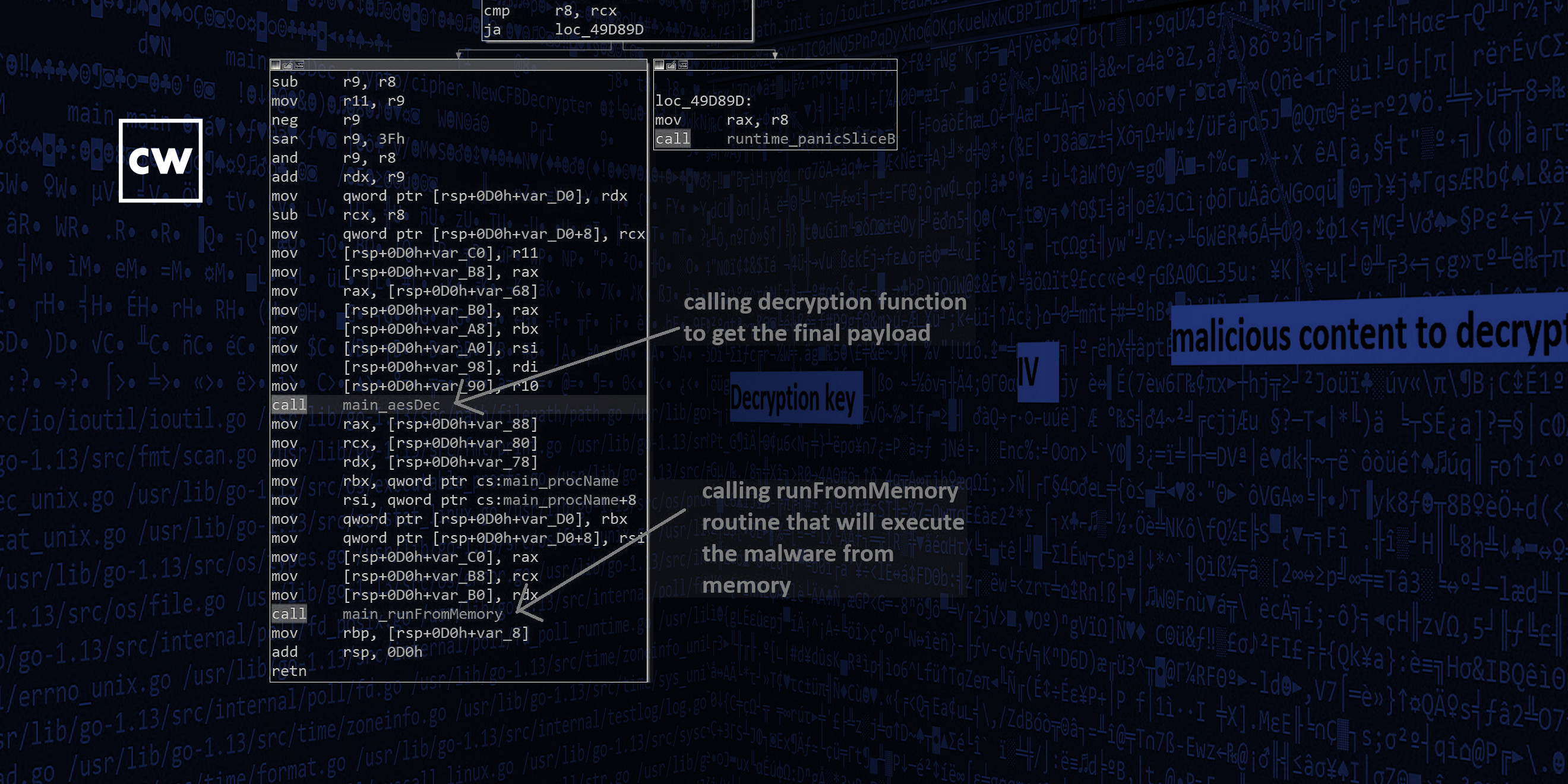
Fernando Martinez: So, this loader, what it does is hides an encrypted payload, and its purposes – so the only thing that you see is that that program has been written in Golang and that it has something encrypted. You don't know the purpose if it's good or bad. And then whenever it's decrypting the payload, it just runs the payload in memory, so it's hidden from the analyst and the antivirus in the system or anything. And it does a really good job at staying hidden from those security tools.
Dave Bittner: Let's talk about Ezuri itself. So this is code that had been posted on GitHub?
Fernando Martinez: Yeah. Looking into the code that we had available, we identified some strains that led us to a GitHub user called "guitmz," who appears to be an offensive researcher. And we identify that this tool was first released on GitHub around 2019, and the full code was there and probably just for good purposes it was posted on GitHub. But it wasn't until recently, until 2020, when it was started to be noticed in the malicious or the attackers' community, and it started being used by some attackers like TeamTNT. But the ability of having that code in GitHub allows the offensive community and the defensive community to have a look at it and know what it does and identify how to protect against it.
Dave Bittner: And I suppose it is worth noting that the actual name Ezuri has kind of an amusing origin.
Fernando Martinez: That was really fun to find because, look – well, the first thing you do is definitely do a Google search for it. And all of a sudden you identify that you get more drawings than malware-related results. And it came from the Magic the Gathering game, which is a card game with magical creatures. And so that card from the Magic the Gathering, the Ezuri card has the capability of regenerating another target elf, talking about the magical creature. Funny here is that the creator of Ezuri identified this malware as something that can regenerate and/or target ELF, referring to the program or executable in Linux.
Dave Bittner: Right. So a bit of clever wordplay there, I suppose, from whoever came up with this.
Fernando Martinez: Yeah, it's definitely a funny story to tell after all the research.
Dave Bittner: Now, an interesting detail here is that everything happens in-memory, so we're not we're not writing anything to disk, which makes it harder to detect, yes?
Fernando Martinez: Yes, that's true. As soon as any files touches the drive, it is easier to see it in the logs or see afterwards whenever you're doing an investigation. But if it only runs in memory, it is harder to identify those logs or traces that it leaves behind. And you just have to catch it when it's running or it's going to be harder afterwards.
Dave Bittner: Now, in part of your research here, you've identified some malware authors who've been using this. Can you can you take us through that part? Who's out there using this?
Tom Hegel: Yeah. TeamTNT has been the actor that really caught our attention. They are an opportunistic group that really kind of came to rise, I would say, mid 2020, after some reports from ourselves and Trend Micro and Cato Security, we started to see this adversary attack cloud instances such as AWS and then container systems such as Docker, Kubernetes, and so forth. But Ezuri really became used by multiple actors, kind of all generally right now on an opportunistic level. And TeamTNT really kind of sticks out just because of their success and scale of targeting. But at this point, there are definitely others out there that are at this rate nameless that are definitely using the toolset.
Dave Bittner: And how would you find yourself with this on your system? What sort of methods are they using to get people to execute the code?
Tom Hegel: Yeah, in this case, what we're seeing are vulnerable cloud and container-type systems that are not properly secured through best practices, such as vulnerable to exploits that should have been patched and incorrectly secured credentials and services overall for those systems. Once they're on there, they begin to execute the loader. And then at that point, it really kicks off the defense-evasion techniques to then load up their ultimate intentions right now, which tends to be isolated around cryptojacking and credential theft for the systems themselves. But ultimately, it comes down to really doing the best practices for these systems, since they're public-facing often, updating, properly configured, and locked down overall.
Dave Bittner: Now, according to your research here, this is particularly effective at avoiding antivirus detection. Can you explain that part of it for me?
Fernando Martinez: Sure, yeah. So, whenever the payload is packed and encrypted, as Ezuri is doing, they have the capability of hiding all those techniques and purposes of the payload. So, whenever we looked into by VirusTotal to see how it was identified by several antivirus, we identified that if that payload was encrypted with Ezuri, only three out of sixty or seventy antivirus identified it as malicious. Whereas whenever the payload was not encrypted, almost all of the antivirus identified as malicious – at least it was around fifty or sixty.
Tom Hegel: Yeah, and one interesting note there is the loader really kind of helps on multiple levels because it has the payload that's encrypted and it's all written in Go, so the delivery process is rather difficult to detect right now, because Go and the actual malicious payload is encrypted. And then you have the execution side, which is where you would hope to catch it if you didn't catch on the delivery side. And the execution really follows it through the memory-only approach. So you have to be doing memory scanning rather than looking at pure AV or files on the system themselves for AV detection. So there's quite a few steps of defense evasion that you really kind of have to be on top of to catch this type of stuff.
Dave Bittner: Well, I mean, let's dig into that, what are your recommendations here for people to best protect themselves?
Tom Hegel: Yeah, I'll kind of start there. I think one of the biggest things is really following the best practices to ensure that things that are public-facing are following updates and secure compartmentalization through, you know, things aren't executed unless you're authorized. Things are properly secured through credentials and so forth. Having a publicly accessible service, you want to make sure that nothing could be executed as well. And that's just the basics to avoid the really common stuff. Then it gets into, you know, if you had to operate in, like, a zero-trust-type approach or you have to kind of consider your environment constantly compromised and be able to hunt and detect this type of stuff while it's already in your network. So there's definitely multiple levels. But I think the biggest bang for your buck here is really, again, making sure that you have the basic best practices for public infrastructure in the cloud and container-type systems.
Dave Bittner: In your estimation, how would you rate this in terms of sophistication?
Tom Hegel: Yeah, on my side, I would say sophistication is rather – I would say a medium sophistication. It's not extreme. There's definitely a lot more sophisticated stuff out there. The persistence of this group is eye opening. While these type of approaches are not uncommon, seeing the persistence of this group and their constant evolve – their constant toolset evolve, such as Ezuri or targeting AWS credentials. I would say the group themselves tends to be a little bit more sophisticated and we could start to see them evolve over time. I think there's a lot more interesting stuff coming from TeamTNT overall. But the approach overall, I'd say a medium sophistication. There's definitely easier ways to do things that still work, but there's definitely the same time, a lot more capable that's – that are a little bit more technically difficult.
Dave Bittner: And what do we know about TeamTNT? Do we have any background information, any guess of who they are?
Tom Hegel: No guess at this point. They're a crimeware-type group, so their attribution is going to be difficult. In many groups such as these, there's many individuals operating in a near-business-like capacity, so they tend to be spread remotely to many different locations. So, no attribution at this point being that their overall mission tends to be financially motivated and opportunistic in nature. There hasn't been any clear links to certain objectives or anything like that outside of those. So attribution at this point, not quite possible, at least from our perspective, but it is definitely possible to continue to link their activities just based off of what they're doing themselves. They're not afraid to put their name on things and say this is TeamTNT, which is pretty common with a lot of crimeware-type groups, trying to build a reputation and so forth, but yeah.
Tom Hegel: I think one thing that's really interesting on TeamTNT itself is, again, their evolution to continually take steps to advance their capabilities. The one thing that really catches my attention is them recently going after AWS credentials in scenarios after using Ezuri to get into environments. Targeting AWS credentials in an opportunistic fashion isn't too surprising. However, that really, in my opinion, opens the door for them to kind of take it to the next level of completely compromising organizations for intellectual property theft or access for espionage or things like that. So, you know, complete network and cloud container compromises rather than just cryptojacking. A little bit more complex, but I think that this group is starting to walk down that path.
Fernando Martinez: I just wanted to add that I think I forgot to mention the Ezuri loader was a created in 2019, but it wasn't until almost 2020 when he was posted on a black hat forum called A Veil of Code (ph), that it was made more public, and afterwards, a few weeks after, we started seeing it on TeamTNT and other attackers also.
Dave Bittner: Our thanks to Fernando Martinez and Tom Hegel from AT&T Alien Labs for joining us. We'll have a link to the research in the show notes.
Dave Bittner: The CyberWire Research Saturday is proudly produced in Maryland out of the startup studios of DataTribe, where they're co-building the next generation of cybersecurity teams and technologies. Our amazing CyberWire team is Elliott Peltzman, Puru Prakash, Kelsea Bond, Tim Nodar, Joe Carrigan, Carole Theriault, Ben Yelin, Nick Veliky, Gina Johnson, Bennett Moe, Chris Russell, John Petrik, Jennifer Eiben, Rick Howard, Peter Kilpe, and I'm Dave Bittner. Thanks for listening.


