Social engineering: MINEBRIDGE RAT embedded to look like job résumés.
Dave Bittner: Hello everyone, and welcome to the CyberWire Research Saturday. I'm Dave Bittner, and this is our weekly conversation with researchers and analysts tracking down threats and vulnerabilities, solving some of the hard problems of protecting ourselves in a rapidly evolving cyberspace. Thanks for joining us.
Deepen Desai: We came across these resumes or resume decoys which were embedded with command to download the MINEBRIDGE remote access Trojan
Dave Bittner: That's Deepen Desai. He's CISO and VP of Security Research and Operations at Zscaler. The research we're discussing today is titled, "Return of the MINEBRIDGE RAT with New TTPs and Social Engineering Lures."
Deepen Desai: Now, we have been tracking this malware family for the past couple of years, and what was interesting in this case was, you know, it was leveraging the resume theme, which was also related to a couple other campaigns that we saw. And some of the TTPs – tactics, techniques, and procedures – that the threat actor used in this campaign matched what we saw early last year as well.
Dave Bittner: Well, let's dig into the research together here. You start off with some threat attribution. Who do you think is likely behind this?
Deepen Desai: So based on some of the techniques that we saw here, we are attributing this with a moderate confidence to Threat Actor 505, which is a financially motivated threat group that has been active since at least 2014. And now, attribution is, you know, it's a difficult game because, you know, it's very easy to see overlap in infrastructures across different threat actors as well. But based on some other things that we observed, we feel like it's TA505.
Dave Bittner: Hmm. Well, let's walk through the attack flow together. How does someone find themselves falling victim to this?
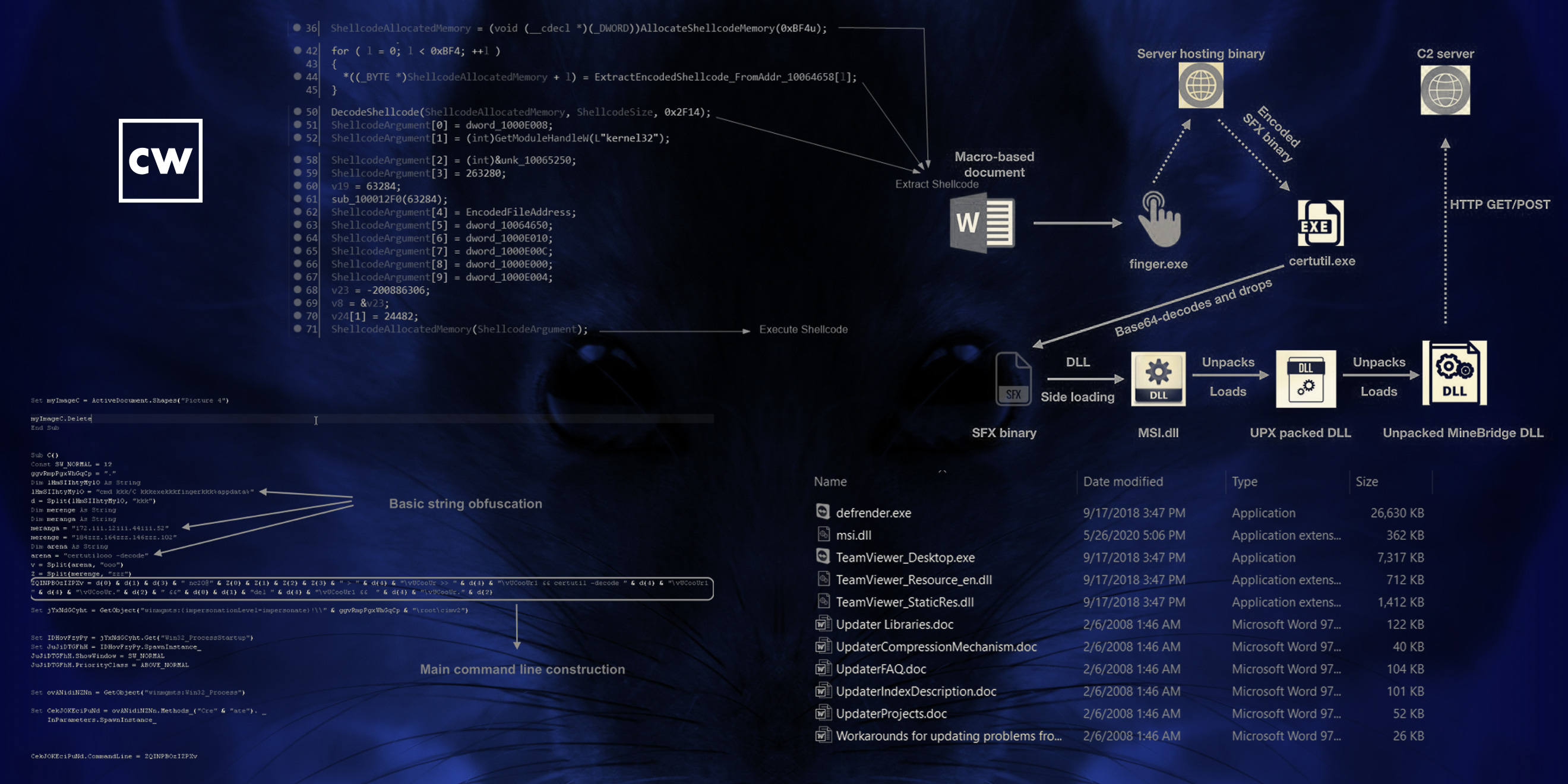
Deepen Desai: So if you look at the attack chain, and it starts with a job resume document, so it's a macro document that will prompt the victim to enable content, which is to run the macro. If the victim falls for that, it will pop a PDF and show the actual, I would say, decoy profile of someone who was trying to apply for the job. But in the back end, what happens is the macro code will leverage Windows finger.exe. It's a legitimate program to download malicious content from the attacker controlled infrastructure. Now, that file that gets downloaded, a stage-one payload, is an SFX binary. It's named, again, after a Windows program called "certutil.exe," which is then responsible for dropping a package. That is actually a legitimate TeamViewer installer package. The only caveat over there is the package also includes a DLL, which is this MINEBRIDGE RAT.
Deepen Desai: And the reason why the attacker chose to do this was they're leveraging a vulnerable version of TeamViewer application. So the vulnerability in that older TeamViewer application was it was prone to DLL side-loading attack, right? And using that vulnerability, the adversary is able to load MINEBRIDGE DLL on the victim's machine. And after that, it's all the C&C activity, the attacker has full control of the system and is able to download arbitrary files, steal information, and even launch further attacks.
Dave Bittner: Hmm. So, it's interesting to me, you know, there's several things going on here, several layers, but also, you know, being able to take advantage of a known vulnerability in TeamViewer. There's a certain degree of cleverness there, I suppose. And additionally, I guess there's a chance that TeamViewer wouldn't draw undue attention to itself.
Deepen Desai: Yeah, I mean, this thing was patched by TeamViewer, then your version of TeamViewer already patches as well. It's an old vulnerability, but yes, this is a very clever tactic. They're trying to bury, using two to three different things that we observed. The first one was they were leveraging Windows operating system legitimate application names, like, if you notice there, there's a misspelled "defender.exe" as well for one of the binaries that gets dropped. Certutil is another. And then usage of, you know, legitimate programs like TeamViewer and finger.exe. That absolutely makes it difficult for some of the endpoint security software to flag this.
Dave Bittner: Now, once it starts reaching out to the C&C controller, what's going on there? What are you tracking from that part of things?
Deepen Desai: So, once it does establish persistence on the victim machine, I mean, there are a bunch of commands that are embedded in this RAT. I mean, the attacker is capable of running arbitrary commands, downloading arbitrary payloads and installing are in the victim machine. They're also able to monitor and kill other processes that are running on the system, like, it could be a security software, could be anything that the attacker doesn't want on the victim machine. Overall, they're trying to monitor for information. And this is where, you know, the motivation eventually is to make profit out of the information that they're able to collect out of the – even having that network foothold and selling it to another group, resulting in a lot of financial benefits for the threat actor.
Dave Bittner: What about persistence? How do they go about trying to stay on a system?
Deepen Desai: Yeah, so that's, again, the tactic that we talked about earlier about using Windows operating system filenames. So even for the persistence part, they actually create a LNK file with the name "Windows Logon.lnk," which is a LNK shortcut, and it's created in the startup directory. This is basically what will result in the executable file that the LNK file points to, which is the MINEBRIDGE RAT to execute every time the system restarts.
Dave Bittner: So, one of the things you highlight in your research here is that they've also implemented some sort of an alternative attack flow. What's going on there?
Deepen Desai: Yeah, so the first one, which was a unique one that we expanded in the blog, is where, you know, the MINEBRIDGE DLL was being loaded using this DLL sideloading technique via TeamViewer. The alternate attack flow that we saw, which actually is supported by the DLL as well as you could actually run it using the regsvr32.exe. So basically the adversary is able to register this as a service on the victim machine and get the MINEBRIDGE RAT installed in that manner as well.
Dave Bittner: Hmm. Well, what's your estimation of the sophistication of the folks who are behind this?
Deepen Desai: I think some of the techniques that we saw, in fact, the one that I'll specifically call out, the attackers' use of legitimate Windows binary finger.exe to download content from the server was was one of the very few ones – in fact, I would call it the first instance that we saw in the wild where a threat actor was using finger.exe in the attack chain. They also were, I mean, leveraging things like TeamViewer legitimate application and then sideloading technique to get the MINEBRIDGE installed was also pretty cool. So I would say it is a sophisticated attack. We've listed all the TTPs on the blog for anyone interested in finding out at each layer what was the tactic that the adversary used in order to establish persistence, in order to exfiltrate, or to perform C&C activity.
Dave Bittner: So what are your recommendations for folks to best protect themselves against this one?
Deepen Desai: Yeah, I mean, this team was very similar to another campaign that Google's security group also reported where, you know, several security researchers were being targeted. And a lot of the components of both of these campaigns still involve use of social engineering. So, the inherent trust that we place in certain, you know, contacts. One example that comes to mind over here is, you know, if you get reached out on LinkedIn by a person that is also connected to five other people that are on your contact list, I mean, chances are you will accept that connection and then you will also, you know, communicate with that person if they reach out. So they try to exploit that trust. And that's the starting point. Beyond that, you know, the campaign that, for example, Google highlighted involved further communication and dropping off, again, similar to resume files, profiles.
Deepen Desai: In this case as well, what you notice is the job resume files are being delivered to the victims and the victims are again being prompted to run the macro code and start the infection cycle. So, being vigilant towards any of these files that are coming from external sources, right? Not running arbitrary files on your system, and especially do not enable content, not run macro. That is never going to lead to any kind of secret message being decrypted for you. It will always lead to bad stuff on the computer.
Dave Bittner: Right. Right. Words to live by, right? You know, I think it's interesting that just sort of tracking TA505 is, as you and your colleagues have been doing here, that they've been around since at least 2014. I mean, you know, they've been around a while. And the fact that they're evolving, that they're changing their tactics, but still in the game, I think there's something noteworthy about that as well.
Deepen Desai: Yeah, absolutely. And overall, if you look at the, I mean, the threat landscape evolution, if you look at things like ransomware, if you look at some of the other infostealer campaigns as well, the adversaries are moving away from, you know, what I would call its spray-and-pray kind of approach, like a no shotgun approach. It's more targeted, more tactical. And the volume of emails or activity is considerably lower in each of these campaigns that we see.
Dave Bittner: Our thanks to Deepen Desai from Zscaler for joining us. The research is titled, "Return of the MINEBRIDGE RAT With New TTPs and Social Engineering Lures." We'll have a link in the show notes.
Dave Bittner: The CyberWire Research Saturday is proudly produced in Maryland out of the startup studios of DataTribe, where they're co-building the next generation of cybersecurity teams and technologies. Our amazing CyberWire team is Elliott Peltzman, Puru Prakash, Kelsea Bond, Tim Nodar, Joe Carrigan, Carole Theriault, Ben Yelin, Nick Veliky, Gina Johnson, Bennett Moe, Chris Russell, John Petrik, Jennifer Eiben, Rick Howard, Peter Kilpe, and I'm Dave Bittner. Thanks for listening.


