A snapshot of the ransomware threat landscape.
Dave Bittner: Hello everyone, and welcome to the CyberWire Research Saturday. I'm Dave Bittner, and this is our weekly conversation with researchers and analysts tracking down threats and vulnerabilities, solving some of the hard problems of protecting ourselves in a rapidly evolving cyberspace. Thanks for joining us.
Jen Miller-Osborn: The incredible change and ramp up that we've seen over that time, we thought it was a good time to kind of revisit that and get a state of the, you know, what does the ransomware threat landscape look like now?
Dave Bittner: That's Jen Miller-Osborn. She's Deputy Director of Threat Intelligence with Palo Alto Networks Unit 42. The research we're discussing today is their latest Ransomware Threat Report.
Dave Bittner: Well, I mean, before we dig into some of the details of the report here, I think it's worth taking a little look back at the history. I mean, my recollection is that ransomware, like a lot of things, started out small and and sort of, you know, low dollar amounts, a lot like spam. You know, it was a nuisance for a lot of folks. But first of all, is that perception correct on the origin story of it, and how is it developed since then?
Jen Miller-Osborn: Mm-hmm. That's definitely how it started. And it also started out typically targeting individuals. So the payout was significantly smaller and there wasn't a lot of attention paid to it, especially from a business sort of perspective. But then, as will happen, criminals will look for bigger paydays. So they started recognizing, hey, if we go after businesses, we can get way more money. You know, then it's not one person, it's hundreds of people, potentially all of their customers. So then we started seeing a shift into going after businesses. And it's really just continued in that vein over the years with the attackers both becoming better at their targeting, better at their development of ransomware, and also just continuing to advance the tactics they take to get paid.
Jen Miller-Osborn: So, one of the new things we've seen going on, especially over the last year or so, is what we're calling "double extortion," where ransomware attackers have recognized that the traditional guidance was to have good backups. If you had good backups, then you'd be fine. And attacker's have recognized that, so now they've – some of the groups have started going into these networks before they actually execute the ransomware and looking for valuable information. You know, IP, anything related to sales data, customer data, things that would be very, very damaging for the organization to lose. And then they're exfiltrating that information first, and then encrypting all of the systems.
Jen Miller-Osborn: So that way when they go back to the organization, they can say – if the organization says, whatever, you know, we have good backups, goodbye – they have the additional leverage of well, that's fine that you can restore from there, but how valuable is this data to you? And a lot of the attackers that are doing that are also posting that information that this organization's been compromised to a website somewhere on the dark web so that there's also that kind of public disclosure, hey, you know, we have this organization and their data, we're going to release it if we aren't paid by X time. So just – yep, they continue finding new and inventive ways to make money.
Dave Bittner: Well, one of the things is the report tracks here is the increase in the amount of money that they're making and the amount of money they're demanding. What did you uncover there?
Jen Miller-Osborn: They're going after, in many cases, larger organizations or organizations that can't afford the downtime. One of the worst things we've seen is the continued focus on healthcare sector attacks, because, you know, when you're holding a hospital hostage, they have quite a bit of urgency to have their systems up and running. But they're also just going after both bigger organizations and more money because they know they can demand it. And you'll also see the amounts have gone up with the groups where they're doing this double extortion kind of thing because they really have two different things they can monetize, plus the perceived public pressure of losing all of that data if they don't pay by a certain time. And that data is for some of the groups there to say they're going to publish publicly, and that –there are organizations that wouldn't be able to recover from that.
Dave Bittner: You know, for many years, the popular wisdom was, "don't pay the ransom." You know, that that's certainly what the FBI's message was. And I suppose the notion was, you know, if we pay the ransom, then we're supporting this ecosystem and incentivizing them to continue their efforts here. Is that still the case? I mean, is it – I guess what I'm getting at is does the message of don't pay the ransom align with what's actually happening on the street?
Jen Miller-Osborn: I don't think organizations ever want to pay the ransom. You know, it's a use case or a business case per organization for what they can withstand or what they can take to be and still be able to recover from. So, while, you know, no one's ever going to encourage paying the ransom because that does further encourage the attackers, you know, it can be a business decision where that's the only way they're going to be able to remain a business or how are they doing that logic, and it's kind of hard not to feel at least some level of sympathy.
Dave Bittner: Yeah, one of the things that you track here in the research is the availability of these tools and, you know, how there are more readily available ransomware-as-a-service subscription-based models. Can you share some of the details on that side of things?
Jen Miller-Osborn: Sure, so that's where – it's called an affiliate model, and it's where the attackers who own the ransomware itself are kind of the base. They let others rent it out to then conduct their own attacks. You see this as well with a lot of other types of malware, like botnets and things like that. And it's just another way the attackers have figured out to make more money and in some cases make more money easily because they're setting up the structure for it and the software and then these other people are paying them to do actual attacks. It's just it's another it's just another step in attackers figuring out every possible way they can to monetize ransomware attacks.
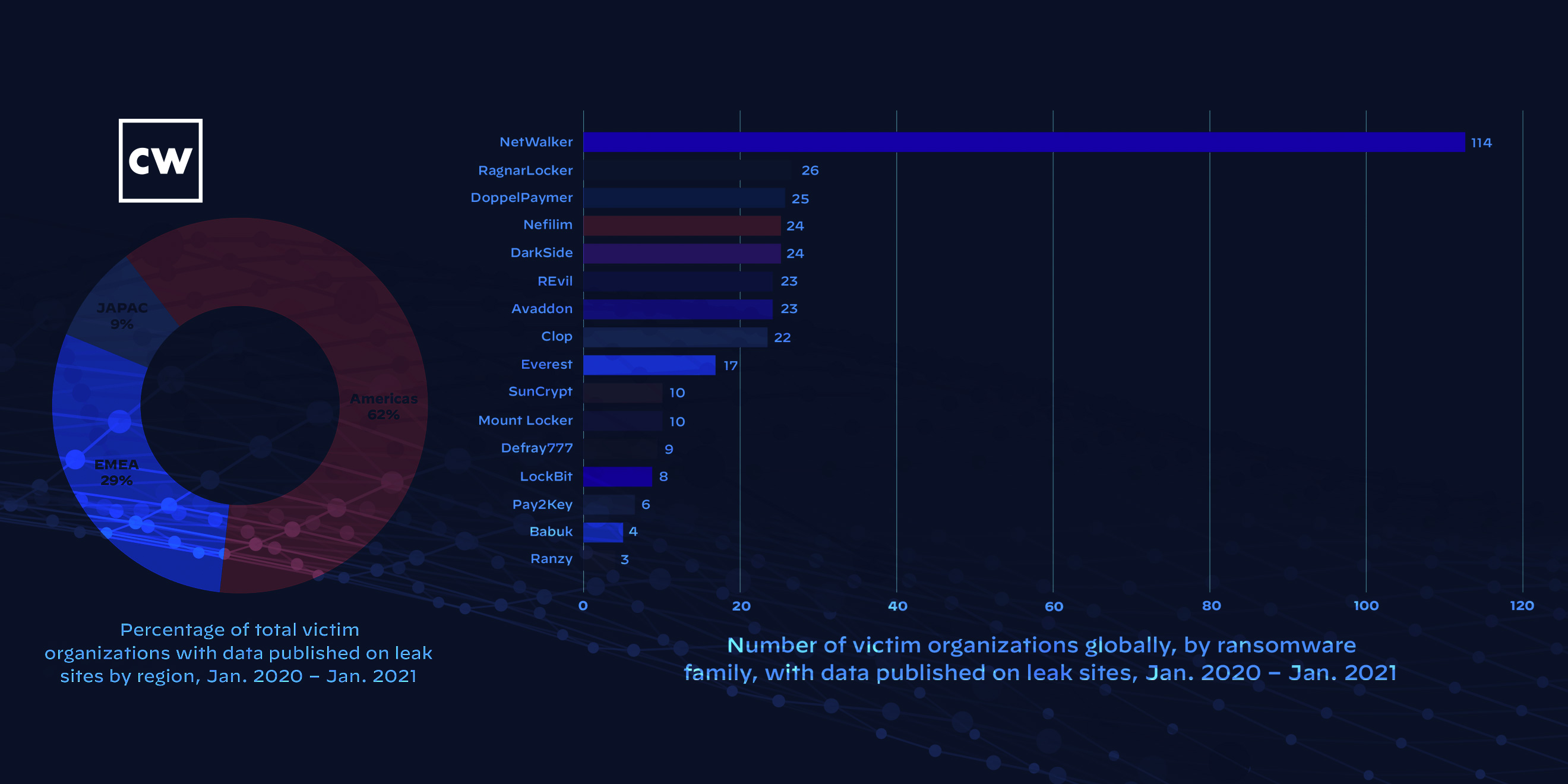
Dave Bittner: You know, one of the things that really struck me when I was looking through the research here, when you're highlighting this rise of double extortion was the activity from the Netwalker gang, and how much more activity you saw from them than some of these other groups who are leaking information online.
Jen Miller-Osborn: Yep. And that was one of the things that they really like to do, and I think that's it's worth noting that that also got them quite a bit of attention from law enforcement. So there was that international law enforcement effort to disrupt that particular ransomware family.
Dave Bittner: Yeah, well, let's run through some of the other details here. I mean, when we're looking at the various sectors who've been hit hardest by ransomware attacks. Can you share with us, I mean, who's getting hit worse?
Jen Miller-Osborn: Unfortunately, healthcare has been hit quite heavily, which is one thing that we really don't like to see. But that's definitely been an area that's been a focus. What we've seen by far is manufacturing quite a bit. And then, you know, we're seeing kind of legal services, construction, high tech – it kind of runs the gamut from there. But if you look at this chart from a perspective of potential amount of money that could be made by ransoming these various organizations, you can see a lot of the focus is on organizations that potentially have larger resources and maybe more difficulty in recovering if they lose their data.
Dave Bittner: Yeah, on the defensive side of things, I mean, I suppose it's worth noting that these exfiltrations, I mean, in some cases, they're grabbing multiple hundreds of gigabytes of information. And it strikes me as interesting that the organization's attention wasn't drawn to that – you know, in terms of shoring up your defenses, it seems like being on the lookout for that is something people really should focus on these days.
Jen Miller-Osborn: Yes. For any for any number of reasons, large amounts of data leaving your network should probably be noted.
Dave Bittner: (Laughs)
Jen Miller-Osborn: And also the fact that ransomware has continued to grow and spread at the rate it has just highlights that it really hasn't been taken seriously. You know, it kind of remained this nuisance, like we were discussing earlier, where people really didn't recognize the threat that they were facing. And I think that's changing now. That's definitely one of the reasons we wanted to do an updated ransomware paper now to call the organizations' attention to this, that this is a massive problem. They are making incredible amounts of money on it and we really need to globally be more effective in our defense.
Dave Bittner: Are those nuisance operators still out there, I mean, are there groups out there who are still going after individuals?
Jen Miller-Osborn: You still see people going after individuals, but very, very little. That tends to be more of the variations of the old Nigerian prince kind of scheme. And we track that quite a bit. We have grouped all of that activity under "Silver Terrier" for us. So they definitely continue to be active and to evolve their methods of making money. But for the most part, there are still other smaller ransomware families out there. And that's one of the things – one of the goals with publishing this paper and getting this data out there is by drawing attention to it, you'll get more organizations to improve their protections to further price out some of these other ransomware families. And that's one of the key ways and one of the only things we can really do to stop this outside of law enforcement efforts. That, in conjunction with people recognizing this problem and doing better and better defenses will start to price out a lot of these different hackers because they aren't going to be able to continue to evolve at the same kind of speed.
Dave Bittner: Now, one of the things that you track in your research that I found interesting was just the increase in incident response costs. That the you know, what it takes for an organization to react when when this happens to them – the price of that has increased significantly as well.
Jen Miller-Osborn: Yep, the price of that has increased. And there are any number of reasons around that demand of the complications that can be involved in trying to go through one of these cases. And a lot of times, the incident response can be just as expensive, if not more so, than the ransom was, which is another reason that organizations really need to pay attention that this is a legitimate problem and that you could potentially be out a lot of money one way or the other. So, you really want to really want to get ahead of that scenario and try and keep this from happening.
Dave Bittner: Well, let's go through some of the ransomware variants that you all track in the report here. Can you take us through some of the top ones and kind of what their M.O. is, how they do the business they do?
Jen Miller-Osborn: Sure. So one of the ones that really stood out to us is Ryuk. That, in particular for their targeting of healthcare, which is unfortunate, but it did result in CISA and the FBI and the Department of Health and Human Services jointly issuing warnings for healthcare organizations, specifically about being aware and defending against Ryuk, because they were focusing so much on healthcare. Which, yeah, there's just a special place for people that that's where they've decided they're going to make money. Like, you can literally pick any other kind of organization, but healthcare is going to be the one you're going to target? Like, yeah, you deserve all of the law enforcement attention that you get.
Dave Bittner: Sure, yeah.
Jen Miller-Osborn: And then you already mentioned Netwalker, which is the one that we really saw taking advantage of the double extortion technique. And again, that also got significant attention, at least this time from law enforcement and works to disrupt that. So at least those two are, I think, good highlights of the fact that there's more awareness being put on ransomware attacks and more focus on making sure people are informed defenses are in place. Law enforcement is really focusing on the people carrying out these attacks to go after that and disrupt it. And that's kind of unprecedented, really, especially for a lot of the cyber things where we've treated this over the years that it's being recognized now. And there's that the focus that it's big, big global problem is. Good, and I think it's very necessary it needed to happen now.
Dave Bittner: Mm-hmm. Yeah, I think that is interesting. You know, the pressure is on from law enforcement on an international level where these folks aren't just operating with impunity, you know, they have to be looking over their shoulders.
Jen Miller-Osborn: Yes. And that is exactly – yeah, that's exactly what should be happening. It's the success story of everyone working well together in the way you would always hope they do, so at least in that it's a good news story. And I expect that we'll continue with law enforcement, and, you know, once these relationships are built, these processes are built, it becomes easier and easier over time to do more cases like this. So the attackers should, you know, be aware that they're in the crosshairs.
Dave Bittner: Yeah, absolutely. In terms of where we find ourselves, if you're sort of tracing a curve, you know, the growth and the rise and hopefully eventually decline of ransomware, do you have any sense for where we are on that curve? Is this a problem that we're getting a handle on or is it to continue to grow in seriousness? Where do you suppose we are?
Jen Miller-Osborn: I think we're at the threshold, honestly, I think we are poised right now to be in a good position to really take action and make global change with regard to being able to stop these kind of attacks and get these people arrested. But I feel that if that isn't recognized now, that then we're really going to be on the back foot playing catch up, because these attackers continue to evolve, continue to find new ways to make larger and larger amounts of money, and they're not going to stop unless someone steps in to stop them. They have no reason to. You know, they're making tons of money without ever having to leave home...
Dave Bittner: (Laughs)
Jen Miller-Osborn: ...So you have to kind of take away that reward.
Dave Bittner: Right, right. Yeah, it leaves us some of us sitting here scratching our head wondering maybe, hey, this is a good line of work to get into. (Laughs)
Jen Miller-Osborn: Like, I could make millions of dollars that way. Hmm.
Dave Bittner: Right, right. Yeah. If it weren't illegal, immoral, and all those other things, you know, it'd be a great business to be in.
Jen Miller-Osborn: Yeah.
Dave Bittner: Well, the report concludes with some recommendations for folks to better protect themselves. Why don't you take us through some of those
Jen Miller-Osborn: So, some things that are very important for organizations to do is be aware of the way these hackers typically try to get initial access. A lot of times it's via phishing. So it's needing to have good cybersecurity protections in place. And these apply not just for ransomware, but these are really just things for attacks across the board. A good backup and recovery process, and that's something really organizations need for any number of reasons in addition to a potential ransomware attack. One of the key components for that is the backups need to be disconnected from the normal everyday network so that they can't also be encrypted if there's a ransomware outbreak. Definitely I've seen some cases that reported where the organizations did have backups, but unfortunately, they weren't properly kept segmented, so they also ended up being encrypted. And then, now you're back to square one, from that perspective.
Jen Miller-Osborn: And really for ransomware, things we're finding to be critical for any number of attacks is effective endpoint security. That's really where the first kind of really malicious behavior component that happens within a network related to ransomware that is detectable. So, if you can catch that there and stop it, then it's, you know, it's a non-issue, it's a non-starter. But it's when you aren't able to catch that on the endpoint where ransomware is able to be executed, then that's where now you're in a tough spot. And endpoint security is the same thing that would have detected the SolarWinds attack, that's the same thing that was an initial way of stopping all of that from happening. It's just – endpoint detection. Very, very, very important for a lot of different types of attacks.
Dave Bittner: Yeah, it's a really good point that, you know, this really is – I mean, it's a broad sort of thing. It's kind of a – I mean, I often like to compare it to public health, you know, washing your hands, it helps you not get sick from a lot of different things right now, not just not just catching a cold...
Jen Miller-Osborn: Exactly.
Dave Bittner: ...And so these there's there's good in all of these things. I mean, like backups – you know, it's great to have backups, but you got to make sure that those backups are good. You've got to practice your recovery processes and things like that. It's that old, I guess, sports analogy, practice like you play.
Jen Miller-Osborn: Yeah, that's very true. And that's definitely something that I think can get de-prioritized because, you know, it's not an everyday activity and things can keep jumping in front of it. But it really is critical. I agree that organizations – they've run the drill and they know what to do in those in those situations. They know who's responsible for it. They know the timeline for it. All of those things need to be – yeah, you need practice.
Dave Bittner: Our thanks to Palo Alto Networks' Jen Miller-Osborn for joining us. The research is Unit 42's Ransomware Threat Report. We'll have a link in the show notes.
Dave Bittner: The CyberWire Research Saturday is proudly produced in Maryland out of the startup studios of DataTribe, where they're co-building the next generation of cybersecurity teams and technologies, our amazing CyberWire team is Elliott Peltzman, Puru Prakash, Kelsea Bond, Tim Nodar, Joe Carrigan, Carole Theriault, Ben Yelin, Nick Veliky, Gina Johnson, Bennett Moe, Chris Russell, John Petrik, Jennifer Eiben, Rick Howard, Peter Kilpe, and I'm Dave Bittner. Thanks for listening.


