EtterSilent: a popular, versatile maldoc builder.
Dave Bittner: Hello everyone, and welcome to the CyberWire's Research Saturday. I'm Dave Bittner, and this our weekly conversation with researchers and analysts tracking down threats and vulnerabilities, solving some of the hard problems of protecting ourselves in a rapidly evolving cyberspace. Thanks for joining us.
Brandon Hoffman: What prompted the creation of this report is that the popularity of specific tools or services in the cybercriminal underground, when they gain a certain amount of popularity, we think it becomes important to share. And this one is particularly interesting because it was used by so many different types of attack tactics and techniques. You know, we thought it was interesting.
Dave Bittner: That's Brandon Hoffman. He's Chief Information Security Officer at Intel 471. The research we're discussing today is titled "EtterSilent: the underground's new favorite maldoc builder."
Dave Bittner: Well, I mean, let's start off with some descriptive stuff here – when we're talking about a maldoc builder, what exactly is that?
Brandon Hoffman: So, what that is, is essentially a service or a tool from another cybercriminal that will create a malicious Word document or document typically for the Microsoft Office suite. So, when you think about an attack where they say, hey, somebody emails you an attachment for an Office document or an Excel, and you open it up, and that then downloads some other malware, that's a malicious doc. And so a lot of cybercriminals don't have the capability to build them themselves, so they hire or buy this piece of software that will build this malicious document for them.
Dave Bittner: Gotcha. Well, let's go through EtterSilent itself. What are the capabilities that it has?
Brandon Hoffman: Yeah, so, EtterSilent is interesting in a couple of different ways. The first thing that makes it interesting is that it uses two different ways – the most document has two different options. One is it exploits a vulnerability, a CVE in Microsoft Office. Now, it's quite an older one, but still one that does exist if it hasn't been patched out there. And the other one uses the other more common method, which is a malicious macro. So that is interesting. It's also interesting because it disguises itself as if it's coming from DocuSign. And I'm sure most people are familiar with DocuSign, but it's supposed to, you know, it provides a level of trust. It's one of the ways that it can kind of set the victim at ease that this something legitimate.
Dave Bittner: Mm-hmm. And you have some examples here in the research. Can you describe to us, what does the DocuSign document look like and how does it trick people into doing things that they'd be better off not doing?
Brandon Hoffman: Yeah, so it comes through, it looks like DocuSign. It has the DocuSign logo on it. It says it's encrypted by the DocuSign Protect Service. And then, of course, at the bottom, it says why I cannot open this document. That's generally used, if you think about, like, the macro version, a lot of times IT security departments will disable macros globally. And if they do, that's great. But if they provide the users the opportunity to re-enable macros to do something, you know, this tells them how – it kind of walks them through how to enable the content, which would be, in this case, malicious content. So, a very smart, very slick way to trick the users into opening macros and letting this malicious code run on their system.
Dave Bittner: And so, once they click through, they enable the macros, what happens next?
Brandon Hoffman: Yeah, so, what happens next is essentially a payload would get downloaded. So that would be the next stage of attack, you know, depending on how it's used together with another piece of malware. So it could be that EtterSilent is used to download a payload for Trickbot or potentially – there's other banking Trojans and others that are available that were part of the campaign, things like Qbot, Gozi or otherwise known as Ursnif, even BazarLoader. And BazarLoader is quite interesting because BazarLoader has been seen in the wild to be paired up with some of the more popular ransomware attacks.
Brandon Hoffman: So, if you think about the attack chain – and I'm not sure if you wanted me to explain this all right now – but somebody would drop this malicious document, a user would open it, the code would run, it would download something like BazarLoader. BazarLoader then allows another threat actor to then potentially load a third element, which could be potentially something like ransomware, directly into the system.
Dave Bittner: Right, right. One of the things that you go into in the research here is bulletproof hosting. Can you describe to us what you're seeing there?
Brandon Hoffman: Yeah, so, bulletproof hosting is something that I feel like a lot of people know about. I'm not sure it always gets the attention that it's due, but bulletproof hosting, just at high-level glimpse, is essentially like the AWS of the cybercrime underground. So, imagine you're an attacker, you need some infrastructure to host all this malicious code, to send the attacks from machines. And essentially, that's what bulletproof posting is, is you spin up machines in this other cybercriminal's infrastructure, and that's where you launch your attacks. That's where you place command-and-control servers. That might be where your spam campaign comes out of from a mail exchange perspective.
Brandon Hoffman: And what's interesting about that is because we've observed it paired up with some of these more popular malware campaigns, a lot of those malware campaigns also use bulletproof hosting. So what that means is that it provides the defenders an opportunity to block this from even getting to their users. So, when you think about how do I defend against something like this? – sure, having macros disabled, sure, having Microsoft Office patched, and having some type of spam filter mail protection in place is good – but also, another level even earlier, is simply blocking traffic from bulletproof-hosted infrastructure.
Brandon Hoffman: That would also provide another layer where, if for some reason you didn't do that, and it still got through to the user, if the callback to download the next stage, the next malware family, that might be hosted by bulletproof infrastructure as well. So that would allow that callback to not happen. That would block that callback. So, it essentially – it provides another opportunity for the defenders to disrupt this attack chain.
Dave Bittner: Mm-hmm. And I suppose, I mean, there's little reason not to block these bulletproof hosting providers, right? I mean, I would hazard to say virtually no legitimate traffic comes out of them. Is that fair?
Brandon Hoffman: It's fair. You know, and truthfully, that's probably a little bit of a longer chat. It does get a little bit tricky sometimes because the bulletproof hosters themselves, of course, smart people. And sometimes they will get, you know, infrastructure from a legitimate provider – let's say they get something from Google Cloud or something from Amazon. Now, typically, those things get shut down very quickly because those those infrastructure providers are looking for that type of abuse of their services. But in certain cases, you know, if there is an overlap there, you might be doing a canopy block of all bulletproof hosted infrastructure, there may come a time where you may accidentally block an IP net block that is legitimate. Will that disrupt a business service? You know, there always exist the possibility that that would happen. But I would say in this case, the juice is worth the squeeze.
Dave Bittner: Mm-hmm. What does this say in terms of the overall commoditization of cybercrime, how these – you basically have these building blocks that people can use to do what they're setting out to do here?
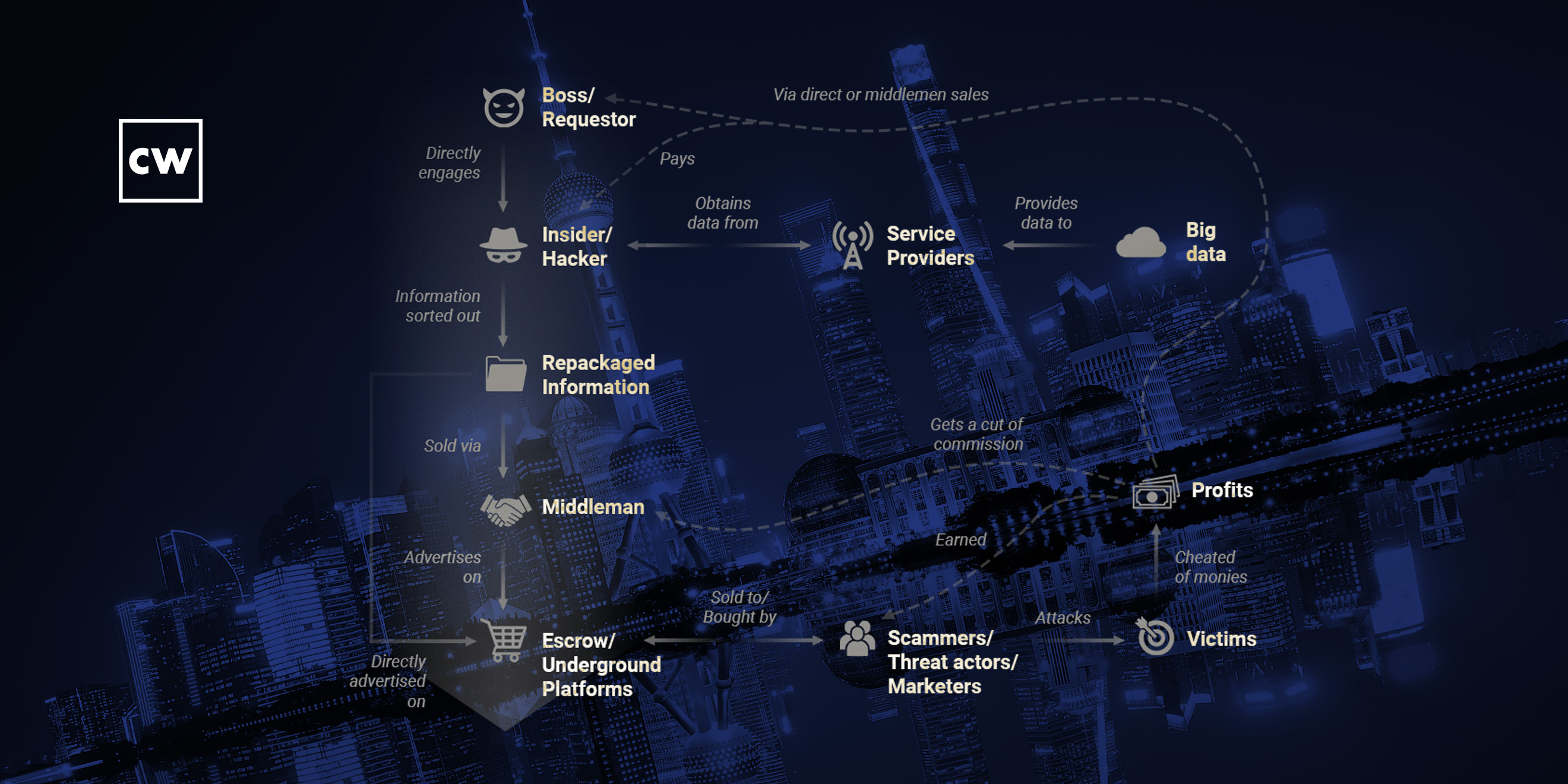
Brandon Hoffman: Yeah, I mean, it's a full marketplace. It's a full economy unto itself. It draws parallels directly to our own kind of obviously non-criminal standard economy where, you know, there's products and tools and services, there's service providers, there's suppliers. You know, they specialize in something specific. So if you're trying to create an attack against somebody, you know, and maybe your specialty is in cashing it out, monetizing an attack, but you don't have skills to write the malware or to gain the initial access, you can buy all these things from other providers. So, there's literally a full economy with service providers and product providers at every stage of an attack. Anything that you could think of. And I could describe that in more detail if you want me to.
Dave Bittner: Yeah, let's dig into it some. What are some of the things of note there?
Brandon Hoffman: Yeah. So certainly, for example, ransomware, you know, there's ransomware-as-a-service where you essentially, you know, you almost don't have to do much. You just have to provide a victim and somebody, you know, another ransomware – they call them ransomware gangs, although that's not exactly an appropriate term – they'll go and do the ransomware, they'll do the negotiation, they'll collect the money, and they'll charge a fee for that. And how would you get that victim for them? Well, you could go to an access broker, and an access broker is somebody who did the initial infection with something like maybe a maldoc, right? They have access to a machine, but they don't have any interest in doing a lateral movement or doing a ransomware attack. They simply get that initial access, then they sell that off.
Brandon Hoffman: Same thing can be said about credentials and identity. There's people who are great at running the malware that grabs credentials from people's browsers and other places, and they don't have any interest in using those credentials further in an attack. Rather, the way they're going to make their money is simply by selling the credentials to somebody who's going to then perpetrate an attack using a credential-based attack,
Dave Bittner: Going back to EtterSilent itself – what are your recommendations for folks to best protect themselves against this?
Brandon Hoffman: Yeah, I mean, there's a couple of different opportunities to best protect yourselves against it. First, of course, is if you can globally disable macros at a policy level and have no exceptions to that. I know that's not really practical advice because there's a lot of departments that have to use macros. Certainly keeping things patched. You know, the CVE that gets exploited in the more expensive version, you know, is a 2017 vulnerability, so certainly that's something that should be handled. So those two things will protect you specifically against EtterSilent.
Brandon Hoffman: But then again, there's that opportunity to look at bulletproof hosting and disrupt that, block that infrastructure from having any communication with your systems or networks. There's a lot of indicators, IoCs, and other artifact information that we've developed, and I'm sure others have developed as well around this, where you could use that on an endpoint technology to block it from running should it even get to the user. Updating spam filtering and mail protection systems are a great thing. And then looking at the attack chain on a broader scale, there's a wealth of information around things like BokBot and Trickbot and all these other bankers and loaders, and just making sure that you're protections are up to date against those. So there are several opportunities to really disrupt this particular maldoc.
Dave Bittner: Yeah. How about, you know, educating your users themselves? I mean, obviously we have the thing with the macros here, but just being on the lookout for these sorts of things in general, do you think that's a useful effort itself?
Brandon Hoffman: You know, I don't know that there is a useful effort around creating awareness for this specific, you know, EtterSilent itself. Because it's – truthfully, in itself, it's nothing novel, meaning it's not a unique tactic that's being used. It's just kind of gained popularity for a variety of reasons. I would say that security awareness is always an important thing to do for any organization. Always make sure that, you know, what you're clicking on is from a legitimate source, take the time to review it. Of course, with the remote work kind of diaspora, that makes things more difficult. People are working later or they have their kids talking to them and they're distracted. And so security awareness is more important now than it ever has been because extra precaution is needed.
Dave Bittner: Why do you suppose that EtterSilent has risen in popularity here? What's so attractive about it?
Brandon Hoffman: Yeah, so what's so attractive about it is that it is cost effective. That's the first thing, depending on which method you choose. And the other reason is that the author of EtterSilent has gone through great pains to make sure that the obfuscation tactics and technique used in the maldoc itself is very robust. So, we do see that from time to time, but – for example, the version that uses the exploit, the vulnerability, that's quite expensive. It ranges about a hundred-and-thirty dollars plus for a single build, meaning a single campaign run for that build.
Brandon Hoffman: But on the other hand, conversely, the macro is only nine dollars. At start – it might , you know the prices fluctuate just like any other market as time goes on – but nine dollars for a unique malicious macro build is a very, very attractive price for many people. Because if you've got to imagine if they're running a campaign, in every campaign, they're going to, you know, let's say they have a hundred thousand targets and they break that into groups of ten thousand, you know, then they're going to run ten campaigns. They could run those ten campaigns for ninety dollars with a unique, malicious document in each one of those campaigns. That's a quite attractive price. And the obfuscation technique provides a good chance that it won't be detected, at least currently, by a lot of the endpoint solutions. So one of those defense mechanisms kind of falls away, which provides a greater opportunity for success from the attacker side.
Dave Bittner: Yeah, that's fascinating, I mean, I suppose it really speaks to the professionalism here that the folks behind developing this have put together, for lack of a better term, a quality product.
Brandon Hoffman: Yeah, it's funny that you say that because that's the term that we use a lot of times. We'll say, well, somebody built some quality software here. And unfortunately, that's the way you kind of have to look at it, is, you know, a lot of the guys who write this software are really, really good at what they do. And they're just doing it on the other side.
Dave Bittner: Our thanks to Brandon Hoffman from Intel 471 for joining us. The research is titled "EtterSilent: the underground's new favorite maldoc builder." We'll have a link in the show notes.
Dave Bittner: The CyberWire Research Saturday is proudly produced in Maryland out of the startup studios of DataTribe, where they're co-building the next generation of cybersecurity teams and technologies. Our amazing CyberWire team is Elliott Peltzman, Puru Prakash, Kelsea Bond, Tim Nodar, Joe Carrigan, Carole Theriault, Ben Yelin, Nick Veliky, Gina Johnson, Bennett Moe, Chris Russell, John Petrik, Jennifer Eiben, Rick Howard, Peter Kilpe, and I'm Dave Bittner. Thanks for listening.


