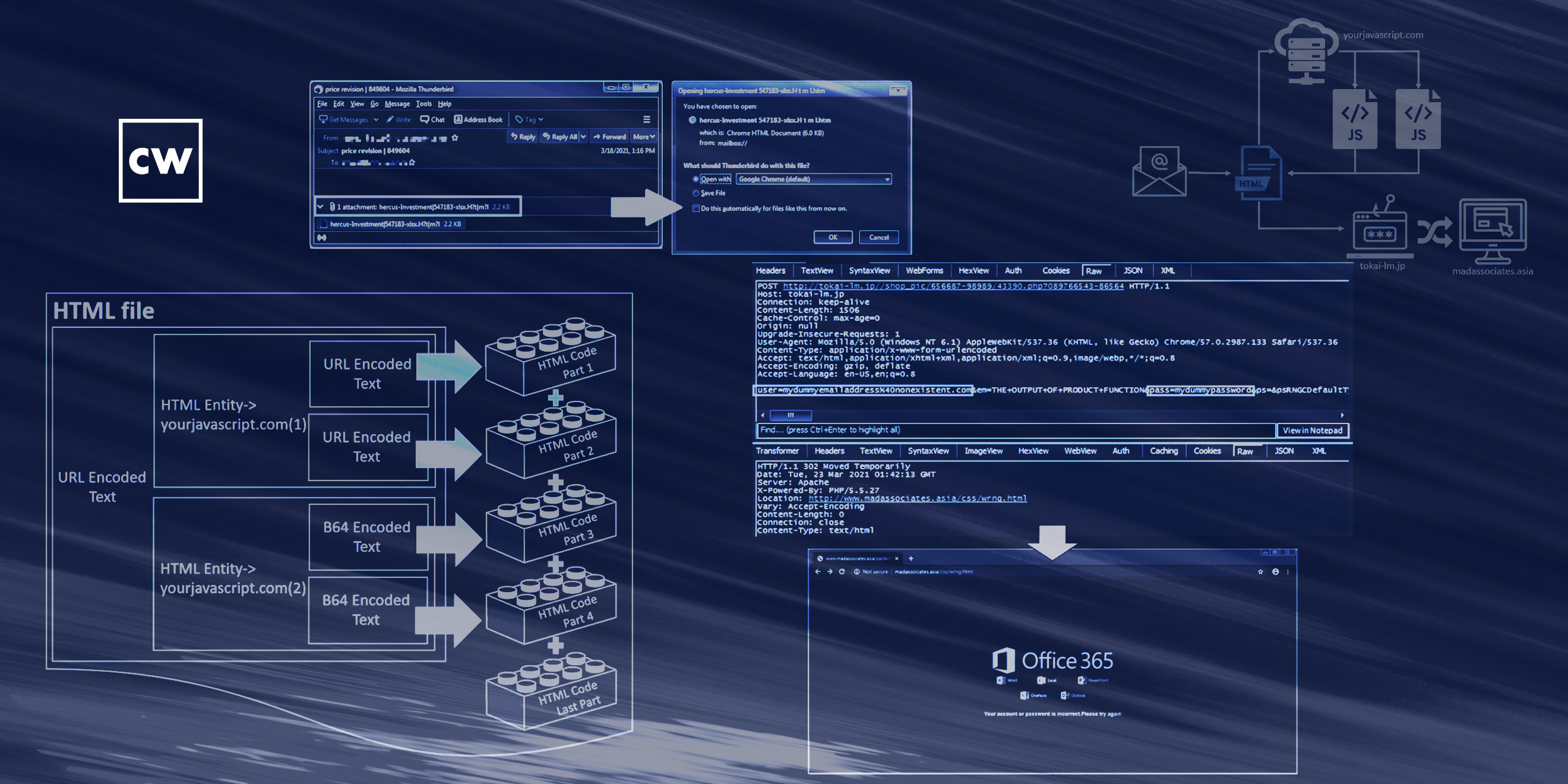
Bad building blocks: a new and unusual phishing campaign.
Guest Karl Sigler of Trustwave's SpiderLabs joins Dave Bittner to talk about their research: "Hidden Phishing at Free JavaScript Site". The research describes an interesting phishing campaign SpiderLabs encountered recently. In this campaign, the email subject pertains to a price revision, followed by some numbers. There is no email body, but there is an attachment about an ”investment.” The attachment’s convoluted filename contains characters the file-naming convention doesn’t allow, notably the vertical stroke, “|.” Even though "xlsx" is in the filename, double-clicking the attachment will prompt the user to open it with the default web browser. Thus, the file indeed appears to be an HTML document. Of course, it’s malicious.
The research can be found here:



