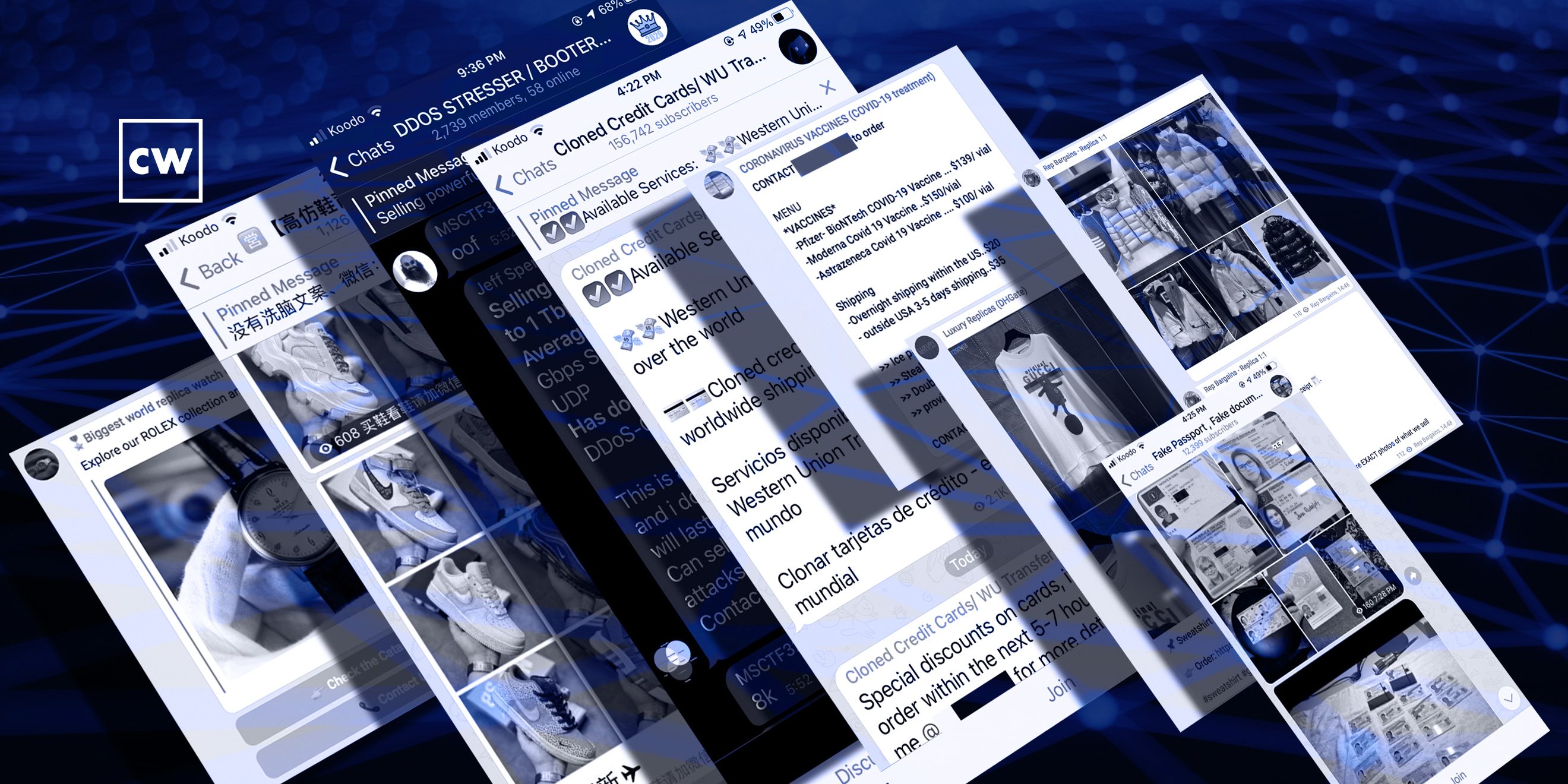
Dealing illicit goods on encrypted chat apps.
Dave Bittner: Hello everyone, and welcome to the CyberWire's Research Saturday. I'm Dave Bittner, and this our weekly conversation with researchers and analysts tracking down threats and vulnerabilities, solving some of the hard problems of protecting ourselves in a rapidly evolving cyberspace. Thanks for joining us.
Daniel Kats: Originally, we were just looking at Telegram like everyone else. We were bored and looking through it, and we started seeing a lot of channels crop up that were focused on selling replicas of high-end luxury goods. And this gave us the question of, what other stuff is out there?
Dave Bittner: That's Daniel Kats. He's a senior principal research engineer at NortonLifeLock. The research we're discussing today is titled , "Encrypted Chat Apps Doubling as Illegal Marketplaces."
Dave Bittner: Well, describe to folks who may not be intimately familiar with Telegram, who might not be a daily users – and I'll admit I put myself in that category – how are things sort of organized within Telegram that these things would bubble up to the surface and be viewable by people?
Daniel Kats: Exactly. So when you think of Telegram, you may be thinking, oh, you maybe use iMessage or WhatsApp or Signal, which are kind of peer-to-peer encrypted chat apps. But Telegram is this much richer ecosystem that you have to think of as a combination of that and then something kind of close to Twitter, like a social network. So it has these channels which are publicly viewable that are about a given topic. Now, they're not so easy to find a lot of the time, but if you know what you're looking for or if you're given a link to the channel, you can join it, and the channel will allow people to post about a specific topic, like, for example, politics or let's say protests that are being organized in some countries. A lot of the time, Telegram is being used for quite legitimate and good purposes, just people being people on the Internet. But occasionally you have some Telegram channels being devoted to, for example, counterfeit luxury goods.
Dave Bittner: Hmm. Well, let's go through some of the things that you all found here. And you just mentioned counterfeit goods. What's going on with that?
Daniel Kats: So, we found a few things. We found people selling what we might call replica or counterfeit luxury goods for a heavily discounted prices. So, for example, you can buy a Moncler jacket, which might be a thousand dollars, for two hundred dollars. But of course, it's not a real Moncler jacket. And you can buy counterfeit watches, you can buy counterfeit sweaters. But we also found a number of other things.
Dave Bittner: What other things did you discover?
Daniel Kats: So, we found some personal information for sale. So you can imagine the sort of thing – SIN numbers, addresses, dates of birth, email addresses, that kind of thing. These come from data breaches a lot of the time. We found stolen credit cards for sale. We found some people who are offering services like making fake IDs, and even people offering to launch a distributed denial-of-service attacks for a fee.
Dave Bittner: Now, you also found some items that were related to COVID-19.
Daniel Kats: That's right. We also found some people – in the early days of the pandemic, especially, when vaccines were a little bit harder to get – we found people selling a variety of COVID-19 vaccines. So, these were marketed towards people in the US, but also China, India, Malaysia, Russia, who were maybe looking for, let's say, a Pfizer vaccine when it was really tough to get.
Dave Bittner: Now, one of the things that caught my attention here in your research was folks who are selling fake documents, you know, things like passports, personal information, those sorts of things.
Daniel Kats: Yeah, this one of the things that – one powerful aspect of Telegram is that they actually enable bots. And these bots can do a number of very powerful things like enable escrow services. So, you can use these bots in order to basically create an entire e-commerce store, including services and reviews, so you can start selling your illegal passports or your counterfeit documents. And then other people, when they get their passport, they can review you, five stars, saying, "great illegal document, would buy again," and pay you anonymously in cryptocurrency. And this not really something that you can get on the other chat applications.
Dave Bittner: Now, because of the way Telegram is structured, you know, as it is built to be secured, does that mean that the folks who run Telegram themselves, do they – is it harder for them to have a view on this activity?
Daniel Kats: It is harder. It all depends on how they look at app activity. So, we started out by looking at publicly available channels. So you don't need to break any kind of encryption, you can just join it and then you can look through the posts as a member. And in that case, it's not very hard for Telegram to be able to discover these posts. In some other cases, we actually joined some private groups by social engineering our way in. And in that case, you can't expect Telegram to be able to do that because, of course, it's end-to-end encrypted, and so only the people in the groups are supposed to be able to see the messages.
Dave Bittner: Can you walk us through that process? I mean, what's it like to social engineer your way into one of these groups?
Daniel Kats: So, what you do is you start interacting with a vendor, with a third party in one of these channels, and they can send you an individual message that invites you to these groups. So the more cautious vendors will screen people to make sure that they're not, well, doing exactly this sort of thing that we were doing, which is reporting on them, rather than trying to make a legitimate purchase.
Dave Bittner: Now, another thing that you found is you could buy services online, things like botnets.
Daniel Kats: Exactly. So, Telegram allows you to buy services online like botnets, like distributed denial-of-service. And you can rent them for however long you want – for an hourly fee, for a fee that goes by minute. And again, you can rate them five stars through that storefront mechanism, through the bots that I mentioned that people can program and that are widely available online. You can create an entire storefront and Telegram to enable you to do this. So you can even find, what are the most reputable botnet for my purposes, in terms of who who actually delivers the botnet versus who just steals your money?
Dave Bittner: You know, that aspect of it I find fascinating – that there's this sort of reputational management built in. And I suppose, I mean, the platform is built to have this functionality for people doing legitimate businesses, and so the bad guys are just taking advantage of that?
Daniel Kats: Exactly. So and it's much more risky for the bad guys. I mean, if you think about it, let's say you go to a store and you buy a T-shirt and you pay for it, but then the T-shirt doesn't come – by "store," I mean online store – so what do you do as a law abiding citizen?
Dave Bittner: Yeah, well, I'll leave a bad review, I'll call my credit card company and cancel the order, and you can bet I'll let all my friends and family know.
Daniel Kats: Exactly. So you have all these avenues open to you for recourse. Now, if you're trying to commit a crime, and you're trying to rent a botnet let's say, you're not going to go to your credit card company and say, well, I purchased this botnet, but actually they just stole all my money. Right?
Dave Bittner: (Laughs) Right.
Daniel Kats: So you need a more robust ecosystem. There has to be some kind of trust mechanism. It's a very tricky thing to enable. But in Telegram, they do have these very sophisticated bots that people can program for all sorts of purposes, and this one of them. So one of the things that you can do is you can have an escrow, which – you pay money into the escrow, and then the service is rendered, and then the money from the escrow will go to the service provider, but if no service is rendered, then the money will just stay with the escrow. And there are even support channels and mechanisms for disputes. So this a quite sophisticated functioning business operation
Dave Bittner: Is there reputational management for the buyers as well? In other words, can the sellers tell, if you're coming to try to buy something, do you have any sort of reputational score yourself?
Daniel Kats: You know, we haven't seen anything like that, but this the sort of thing that we might expect to see. Like in, if you remember Silk Road, where people you used to buy drugs and other sorts of illegal commodities online, there were some implementations that had these kinds of reputations for the buyers as well as the sellers, because there's risk on both sides. We haven't seen it on Telegram, but it's still an evolving market, so as we see Telegram kind of pick up the this semi-legitimate traffic or illegitimate traffic, we might expect to see even more sophisticated tools for all that.
Dave Bittner: What is your sense in terms of Telegram's response to this sort of thing, does it seem as though they're making a good faith effort to get it off the platform? Or are they are they turning a blind eye? Do you have any insights into that?
Daniel Kats: My feeling is that Telegram doesn't want to think about the malicious uses to which people can put their platform.
Dave Bittner: Hmm.
Daniel Kats: I don't know if "blind eye" is exactly the right word, but we certainly found this, and we didn't work particularly hard to find the most egregious offenses. So I would say that they could definitely be doing better in order to police the platform. But of course, it's a very different problem from the way that Twitter and Facebook can approach these challenges.
Dave Bittner: Right, right. I mean, is this the old, I don't know, sort of famous game of whack-a-mole where, you know, if an account is shut down, it's easy for them to spin it up under a different name.
Daniel Kats: One hundred percent. And also part of Telegram's charm is it's meant to be used by dissidents and journalists and people who the government doesn't like to provide anonymity and be able to, you know, jump off and on the platform, and so that definitely plays into these problems. But there are definitely some things that Telegram could probably do that wouldn't be too hard, that would make it significantly harder to set up these kinds of businesses.
Dave Bittner: What should normal users concern be here? If you are someone who's using Telegram and it's one of the regular networks that you take part in, are there any things that you need to be on the lookout on to just make sure that you're operating in a safe way on the platform?
Daniel Kats: Well, I would guess that most users probably would know – if they're on Telegram – whether the offers that they're seeing in various channels are maybe a little bit too good to be true in terms of luxury counterfeit goods. But I think the real takeaway for most everyday people would be just the ubiquity of information being sold on Telegram. So, it was really startling to us that we saw SIN numbers, we saw stolen credit card information, we saw addresses, and it really just reinforced for us how easy it is to commit fraud online. So I feel like if there is one takeaway, it's probably that just be careful what you put online, because one data breach and it's out there, and then it's on Telegram, and then anyone can buy it in order to use that information to commit fraud or do something else nefarious with it.
Dave Bittner: Yeah, once it's out there, it's out there.
Daniel Kats: Exactly, exactly. And so you can imagine the sorts of things, and there's a big market on Telegram for being able to impersonate people to commit tax fraud, commit other types of fraud. So you really have to watch out to try to minimize your online footprint, especially if you're buying from maybe a vendor that you're not familiar with, because you don't know what their security is like. And so, down the line, one, two, three years later, if they have a data breach, they might be keeping all that information, which is then out there forever.
Dave Bittner: And I suppose I mean, it's important to emphasize that, as you mentioned, there are plenty of legitimate uses for Telegram. Just because these things are happening on the platform and certainly we want to look out for them, but that doesn't mean that it's, you know, not worth the effort or, you know, something that you should delete from your mobile device.
Daniel Kats: Exactly. Exactly. Telegram is great. Honestly, I use it, my friends use it. It's a wonderful app. And I think in some ways this a testament to how powerful Telegram is, that it has all these features which the bad guys are abusing, but at the same time, it speaks to this really full, powerful ecosystem that can enable you to do these wonderful things, like you can create games inside Telegram. You can create bots to do all sorts of things – all sorts of useful things. So, I wouldn't delete the Telegram. That's definitely not the takeaway from our research.
Dave Bittner: Fair enough.
Daniel Kats: It seems like everywhere we look, bad actors are adopting new technologies a lot faster than legitimate actors. And so, if we want to see what the future is going to look like three years, five years down the line, just look at what the bad guys are doing today. So I think as we look at these illegal marketplaces on Telegram, it can really paint a story of what is e-commerce going to look like three to five years from now. Maybe we will be buying things on chat apps, completely legitimate things through these kinds of bot storefronts. That will be extremely convenient.
Dave Bittner: Our thanks to Daniel Kats from NortonLifeLock for joining us. The research is titled, "Encrypted Chat Apps Doubling as Illegal Marketplaces." We'll have a link in the show notes.
Dave Bittner: The CyberWire podcast is proudly produced in Maryland out of the startup studios of DataTribe, where they're co-building the next generation of cybersecurity teams and technologies. Our amazing CyberWire team is Elliott Peltzman, Puru Prakash, Justin Sabie, Tim Nodar, Joe Carrigan, Carole Theriault, Ben Yelin, Nick Veliky, Gina Johnson, Bennett Moe, Chris Russell, John Petrik, Jennifer Eiben, Rick Howard, Peter Kilpe, and I'm Dave Bittner. Thanks for listening.


