Iran-linked Lyceum Group adds a new weapon to its arsenal.
Dave Bittner: Hello, everyone. And welcome to the CyberWire's "Research Saturday." I'm Dave Bittner, and this is our weekly conversation with researchers and analysts tracking down the threats and vulnerabilities, solving some of the hard problems of protecting ourselves in a rapidly evolving cyberspace. Thanks for joining us.
Deepen Desai: What the team noticed as part of the tracking activity was a new .NET-based malware - right? - and the DNS backdoor component that we'll shortly talk about being used for espionage.
Dave Bittner: That's Deepen Desai. He's chief information security officer and VP of Security Research and Operations at Zscaler. The research we're discussing today is titled "Lyceum .NET DNS Backdoor."
Dave Bittner: Well, let's walk through it together. Let's start at the beginning here. I mean, how does someone find themselves victim of this? How do they find their way in?
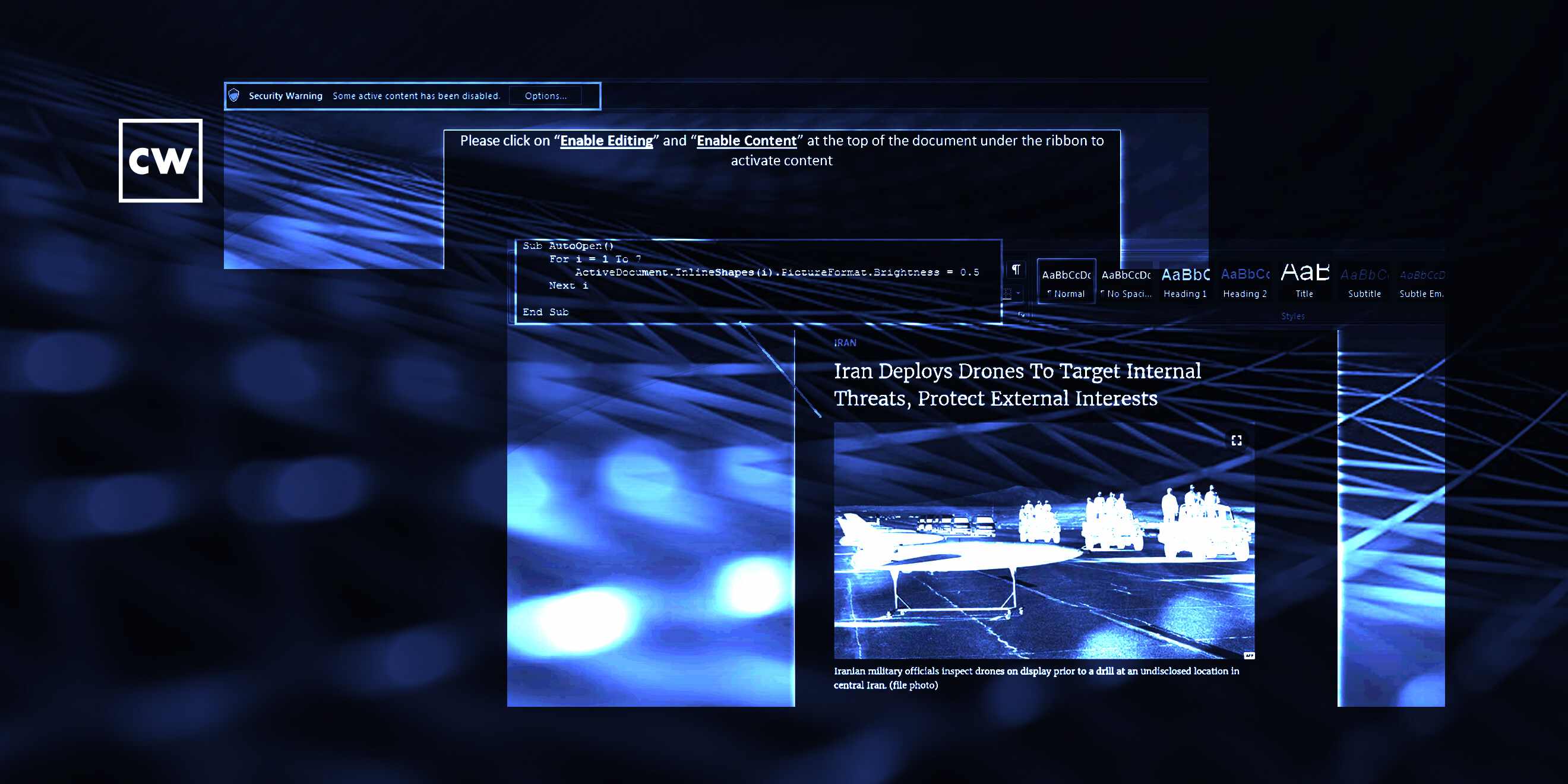
Deepen Desai: Right. So in this case, I mean, the group - the campaign that the team discovered was where the Lyceum threat actor was leveraging the military affairs as a team. Specifically, they were talking about Iran deploys drones to target internal threats and protect external interests. And that was the team of the lure that was being used to get the victim to click on a link and get the infection chain started. There was a newly registered domain that they were leveraging. As soon as the user clicks on that, provided that they fall for the team, a dropper disguised as a .PDF gets downloaded which further downloads the backdoor, which is the .NET DNS backdoor.
Dave Bittner: So just to be clear here, I mean, it starts off with a phishing email with a - you say sort of a subject-based lure. And then we try to get them to click through and then ultimately deploying that dropper.
Deepen Desai: Exactly. And we also saw another variant of the chain where, instead of .PDF, there was an actual macro document. But, again, it starts with a phishing email containing a link talking about Iran drones. And so it could be that. We also noticed another vendor talk about Russia-Ukraine team being leveraged early this year by the Lyceum Group as well. So it starts with that. A link leads to the dropper payload, which could be a .PDF or a macro document. And that's what leads to the final backdoor payload, which is responsible for the espionage activity.
Dave Bittner: So let's talk about that backdoor payload. What exactly goes into that? What is it capable of?
Deepen Desai: Right. So what was interesting about this one was when we looked at the payload - so it hit our cloud sandbox. It was detonated. We convicted it as malicious. But when the team started analyzing it, we noticed that majority of the code was picked up from the open-source tool dig.net. Dig.net is a open-source tool which is a partial implementation of the Linux dig command. It's not complete implementation. It's a partial implementation. But it does DNS-resolving functions. Dig is the domain information groper tool that's part of the BIND software suite. But coming back to the point, majority of the code base was this open-source tool, and they customized it as part of this backdoor to then leverage it to perform DNS hijacking as well as DNS-based C&C activity.
Dave Bittner: So I suppose - I don't know. If we're being generous, we could say they're working smarter, not harder - if we're not being generous, maybe a little laziness on their part.
Deepen Desai: Yeah. This is definitely smarter - right? - because it's a open-source tool. You know, code base is - majority of it is similar to what the open-source tool out there is doing. The other smart part over here is leveraging DNS as a channel. So for those of you that don't know, DNS hijacking is where they're able to manipulate the DNS response queries using an attacker control DNS server, right? So, simple example - from a machine where this backdoor is already running, if a user - or when the malware seems to be going to apple.com, it's actually not going to apple.com but to an attacker control infrastructure. So in the logs, it may appear that the request is going to apple.com or the query is for apple.com, but it's being manipulated using the attacker control DNS server.
Deepen Desai: And the second aspect, Dave, if I may add, is where, using that same channel - now they're using the DNS text records for command and control activity as well. So what that means is the threat actor - in this case, the Lyceum group guys - are able to send commands to the infected machine to perform things such as upload files, download files or any other commands. And the command goes through their DNS channel as well - so using the text records. And then the e-records are used for exfiltration, which is the response to those commands. So the attacker may execute a command like, show me all the files that exist in certain directory. The output of that will again go to the DNS channel e-records, where it's all encoded, and then sent through the DNS channel.
Dave Bittner: So that helps hide what they're up to here, I suppose. Is that - I mean, is that an efficient way to do things? Or is the stealthiness more important than the efficiency here?
Deepen Desai: It is more towards stealth more. Like, they're trying to evade detection - right? - using this channel. So it's more towards that than efficiency.
Dave Bittner: So what does it appear that they're after here?
Deepen Desai: So this group is known to, you know, maintain persistence in the victim environment, and the goal is cyber espionage. And they're looking for very specific information. And that specific information then gets relayed to the attacker. In this case, I mean, they were using military affairs teams. So it's reasonable to assume that some of the government sector organizations were being targeted. So in one of the cases, it was the Iranian drone team. In the other case, as I mentioned, it was the Russia-Ukraine team there. Some of the other regions' government sector was being targeted.
Dave Bittner: And how are they maintaining persistence on the machines that they're able to infect here?
Deepen Desai: Yeah. So they will - once the user falls for the phishing email - right? - and the link gets downloaded, in case of .PDF or the macro document, the malicious backdoor will get downloaded. And it will use the startup option to basically make sure every time the system reboots, the backdoor executes as part of it. So they're able to maintain persistence and stay under the radar because the only communication that's going out as a result of this backdoor, as I mentioned, is DNS protocols. On the network layer as well, you're not seeing some suspicious activity. It's all DNS queries.
Dave Bittner: So does that mean that they're successful in, you know, evading typical endpoint protection?
Deepen Desai: In many of the cases, yes, they are able to do that. It's not difficult to catch this, but it's how, you know, they keep evolving. Like, in this case, you saw them using an open-source tool and customizing it enough to carry out their operation. But that's the cat-and-mouse game - right? - that security industry on the endpoint side have to play when they evolve certain things. Endpoints at times fail. Many of the cases, endpoints do end up detecting it, you know, hours or days after.
Dave Bittner: So what are your recommendations here, I mean, for - in terms of folks best protecting themselves?
Deepen Desai: Yeah. In this case, I mean, the organizations - it's critical that you are inspecting. So there are two things. One is, you know, the phishing part, where user education is important. No. 2 part is where - when the user ends up clicking on any of these links, right? You need to have that consistent inspection happening, right? Whether the threat actor is using a TLS channel to download that initial dropper and the backdoor or something else, the goal is to inspect and prevent that initial payload from entering your endpoints or your environment.
Deepen Desai: The second important piece over here is assume that your controls fail at that first stage. You need to have, again, inspection for all ports and protocol in order to flag. So the, you know, C&C activity that we talked about as well - in this case, it's using DNS as a channel for both command and control activity as well as data exfiltration. So the point is have that post-infection activity getting detected and blocked. Have the data exfiltration channel getting detected and blocked as well.
Dave Bittner: How do you rank this threat group in terms of their sophistication?
Deepen Desai: So if you look at the payload, it was pretty basic. I mean, I wouldn't - and honestly, that has been the case with many other groups. But that's a tricky question, Dave, related to (inaudible) the group compared to the others.
Dave Bittner: Right, right - because it's not necessarily - I mean, sometimes simpler can be effective, right?
Deepen Desai: Yeah, yeah, exactly. Yeah, it was simple, but it was effective.
Dave Bittner: Our thanks to Deepen Desai from Zscaler for joining us. The research is titled "Lyceum .NET DNS Backdoor." We'll have a link in the show notes.
Dave Bittner: The CyberWire podcast is proudly produced in Maryland out of the startup studios of DataTribe, where they're co-building the next generation of cybersecurity teams and technologies. Our amazing CyberWire team is Rachel Gelfand, Liz Irvin, Elliott Peltzman, Tre Hester, Brandon Karpf, Eliana White, Puru Prakash, Justin Sabie, Tim Nodar, Joe Carrigan, Carole Theriault, Ben Yelin, Nick Veliky, Gina Johnson, Bennett Moe, Chris Russell, John Petrik, Jennifer Eiben, Rick Howard, Peter Kilpe and I'm Dave Bittner. Thanks for listening. We'll see you back here next week.


