Fake job ads and how to spot them.
Dave Bittner: Hello, everyone. And welcome to the CyberWire's "Research Saturday." I'm Dave Bittner. And this is our weekly conversation with researchers and analysts tracking down the threats and vulnerabilities, solving some of the hard problems of protecting ourselves in a rapidly evolving cyberspace. Thanks for joining us.
Ashley Taylor: So we at work received a notice from a victim of one of these scams asking our HR department a few details about a job offer. And our HR department, unfortunately, had to inform them that the job didn't exist.
Dave Bittner: That's Ashley Taylor. The research we're discussing today is titled "Doppelgangers: Finding Job Scammers Who Steal Brand Identities." It's been published as part of Ashley Taylor's work as a graduate student at the SANS Technology Institute.
Ashley Taylor: The victim thought that they were going to be starting the job. They had already signed all of their paperwork. They had gone through interviews, everything to think that this job was legitimate. But it was just scammers impersonating the company and stealing all their information.
Dave Bittner: Wow. You know, we're going to dig into all the details here. But before we do, I have to ask - for someone to have gone that far down the path, what do you suppose the scammers were actually looking to get out of them?
Ashley Taylor: So far, we've talked to multiple victims. And most of the time, it's at least personally identifiable information. They go as far as having them fill out their I-9 information to get set up as employees. They also have done things like send them checks or ask them to go to fake websites to, quote, "purchase the equipment that they would be reimbursed for later." And when they go to those fake websites, they hand over their credit card information as well.
Dave Bittner: All right. Well, let's back up a little bit and actually dig into the stuff that that you and your colleagues are tracking here. We're talking about hiring frauds. Can you take us through step by step? What exactly are the bad folks doing?
Ashley Taylor: Sure. What they're doing is they were able to get the information about one of our recruiters. They got his email information, pictures on LinkedIn, as he's - needs to have out there because he's a recruiter. And they then set up fake profiles under his accounts and would put out fake job advertisements on ZipRecruiter, which we didn't use, and LinkedIn, which we used but was a separate profile that we weren't keeping track of. So they would create these fake job scams. And people would reach out to them and they would set up the interviews on - RingCentral is very common - take them through a whole interview process, and then at the end say, you're hired; now give us all your information (laughter).
Dave Bittner: Wow. Well, part of what you outline here in your report are ways that organizations can try to mitigate this sort of thing. Can we dig into that? I mean, you know, you mentioned that these things were set up on LinkedIn, which was a platform that you are all on. But still, you know, how do you keep track of all of LinkedIn? Can we go through some of the methods, the tools that are available?
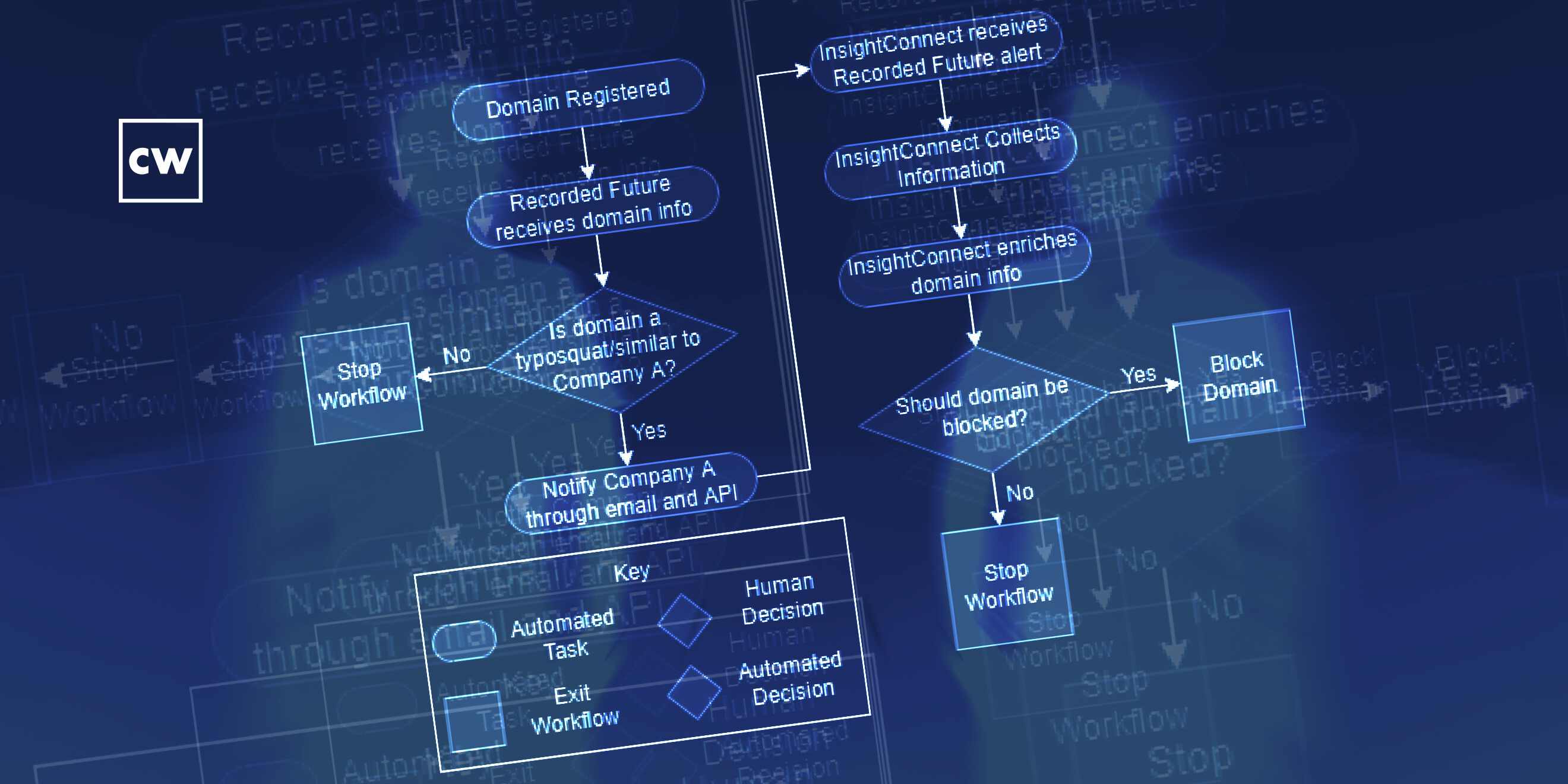
Ashley Taylor: Sure. Fortunately, I started off trying to get information from LinkedIn, but as you can imagine, they're not very open with people just searching for open job requirements. So we really started looking at how the attackers are setting these up, and we found out that they are registering typosquat or similar domains to our company and using that to email victims to send them their paperwork that they need to fill out. And as we were looking at that, we realized we had purchased a product called Recorded Future that would let us know any time a typosquat or a similar domain was registered on our behalf. After we started digging into it, we saw even more clues, such as - they would register a certificate. They would set up an email server on these domains. And the domains were always something like courier-dash-ourcompany.com or very similar to that. So after looking at it, we were able to find these, you know, indicators that then allowed us to create some additional alerting.
Dave Bittner: And it's worth mentioning, Recorded Future is an organization. They sell threat intelligence platform, among other things. So that was a way for you to get some insights here. And there are plenty of other companies who do this sort of thing, but this is the one that you all happen to already be engaged with.
Ashley Taylor: Yes, there are a few open source out there I didn't dig into, such as - SearchStream will let you know any time a certificate is registered on websites you're monitoring, and with dnstwist, you can look for typosquat websites. So there's definitely some future growth in making this more of an open-source solution. But what we had available was Recorded Future, so it's what we went with (laughter).
Dave Bittner: And so once you engage with this and you're using this tool, how does that work into your internal workflow?
Ashley Taylor: So with Recorded Future, we were able to get the alerts, but for a while, we were doing them manually, and that took time. It took on average 20 minutes to look up the site, look at all the indicators, figure out what was happening and decide to block them or to notify our HR and recruiting teams that yet another domain had been set up. So we ended up utilizing our SOAR platform, which happened to be Rapid7's SOAR platform, InsightConnect. And we were able to use the Recorded Future API to grab those alerts down and then start processing them with our SOAR platform. And it would look at things like, has the certificate been registered? If not, it wouldn't continue with the workflow 'cause there's not a lot we can do to get those websites taken down. But the minute that a certificate is registered, then it would continue in the workflow.
Ashley Taylor: And it goes through a series of steps that allows us to take a lot of that manual work we were doing and just automate it and present us with an executive summary that we could really easily just scan through and decide to lock those typosquat-similar domains, then notify our recruiting teams and HR teams about the websites if we felt we needed to. Sometimes we would also, if it's a register that can take down those domains, we would request those. So we went from it taking days, weeks, months until we were properly notified and - to get those domains offline, to - the latest one took us 15 minutes.
Dave Bittner: Wow. So putting together some handy automation for yourselves to make life easier. You know, anytime you unleash automation on the world, there's an opportunity for things to go dreadfully wrong. So there was testing involved here. I mean, how did you go and make sure that before you - you know, you kick this into gear that you weren't going to accidentally do something you didn't want to do?
Ashley Taylor: Luckily, we were able to use ICON, InsightConnect, which allows you to rerun jobs it's already processed. That helped us a lot in testing. But our final test was - I went to a register (laughter), and I registered a domain that should get caught in the workflow. I set up an email server on it and gave it a certificate. And luckily, it was caught pretty instantaneous, which proved the workflow. And now I'm the proud owner of a nice internal stimulated (ph) phishing domain.
(LAUGHTER)
Dave Bittner: So you got that going for you.
Ashley Taylor: Yes.
Dave Bittner: Well, so what are your recommendations, then, for organizations who want to get on top of this? I mean, it strikes me that part of the challenge here is knowing that you have a problem.
Ashley Taylor: Right. So the first step in that is really looking at the type of typosquat domains that are being registered for your company. If you get a lot of the typosquat domains that are careers-yourcompany.com or jobs-yourcompany.com, it's probably worth identifying on all your recruiting websites and your LinkedIn profiles exactly where people need to go to get job information. We ended up actually put in a warning - after this was becoming a problem because we had multiple victims - that basically said any emails coming from these domains are not legitimate. It doesn't totally solve the problem. But, hopefully, people are doing a little bit of research about the companies that they're applying for. And since we put those warnings on our website, it's significantly dropped the rate in people reporting this type of attack. They're still registering domains, but, hopefully, victims are not falling for it anymore.
Dave Bittner: Yeah. I mean, that's an interesting side of all this as well, is that, you know, independent of anything that you all are doing, there are victims out here who are suffering the consequences of this.
Ashley Taylor: Right. And the FBI even just recently posted another article warning victims about these job scams of people impersonating legitimate companies and warning people about the scams. But unless you're paying attention to the news, it's hard to know. So this solution was just something that our company could do to try and get ahead of it and educate people before they fell victim. Because it's heartbreaking to tell people who think they have a job, maybe have left their job, are getting ready to move or whatever they need to do to start a new job and then be told the job never existed in the first place and you got scammed out of your money, and your identity is probably now stolen.
Dave Bittner: You know, I think an interesting aspect of this is this whole notion of being proactive or reactive. And it sounds to me like, you know, the tools that you all put into place here, this is really going out and being proactive about looking for this stuff before it happens.
Ashley Taylor: Right. That's part of where I was promoted in. We now have an entire security team dedicated to what we call posture management, which is really that proactive side of security, the training, the vulnerability management, coming up with solutions like this with automation, just to try and detect things earlier in the cycle so that our incident response and SOC teams can focus on what they do, which is less of the reactive stuff but a lot more of that threat hunting and intelligence.
Dave Bittner: Do you feel like the organization is in a good place now that you have an effective system up and running?
Ashley Taylor: Oh, absolutely. We've been able to use this workflow to create additional workflows, and we've also expanded on it since this paper to now we bring in screenshots of the websites to make it even easier to look at the type of information that's getting here. It's greatly reduced the amount of time it takes for our SOC team to analyze these types of detections. And it's freed us up to look at more creative solutions elsewhere that we could use our SOAR platform for.
Dave Bittner: That's Ashley Taylor. The research is titled "Doppelgangers: Finding Job Scammers Who Steal Brand Identities." We'll have a link in the show notes.
Dave Bittner: The CyberWire podcast is proudly produced in Maryland out of the startup studios of DataTribe, where they're co-building the next generation of cybersecurity teams and technologies. Our amazing CyberWire team is Rachel Gelfand, Liz Irvin, Elliott Peltzman, Tre Hester, Brandon Karpf, Eliana White, Puru Prakash, Justin Sabie, Tim Nodar, Joe Carrigan, Carole Theriault, Ben Yelin, Nick Veliky, Gina Johnson, Bennett Moe, Chris Russell, John Petrik, Jennifer Eiben, Rick Howard, Peter Kilpe, and I'm Dave Bittner. Thanks for listening. We'll see you back here next week.

