An increase in bypassing bot management?
Dave Bittner: Hello everyone, and welcome to the CyberWire's "Research Saturday". I'm Dave Bittner, and this is our weekly conversation with researchers and analysts tracking down the threats and vulnerabilities, solving some of the hard problems of protecting ourselves in a rapidly evolving cyberspace. Thanks for joining us.
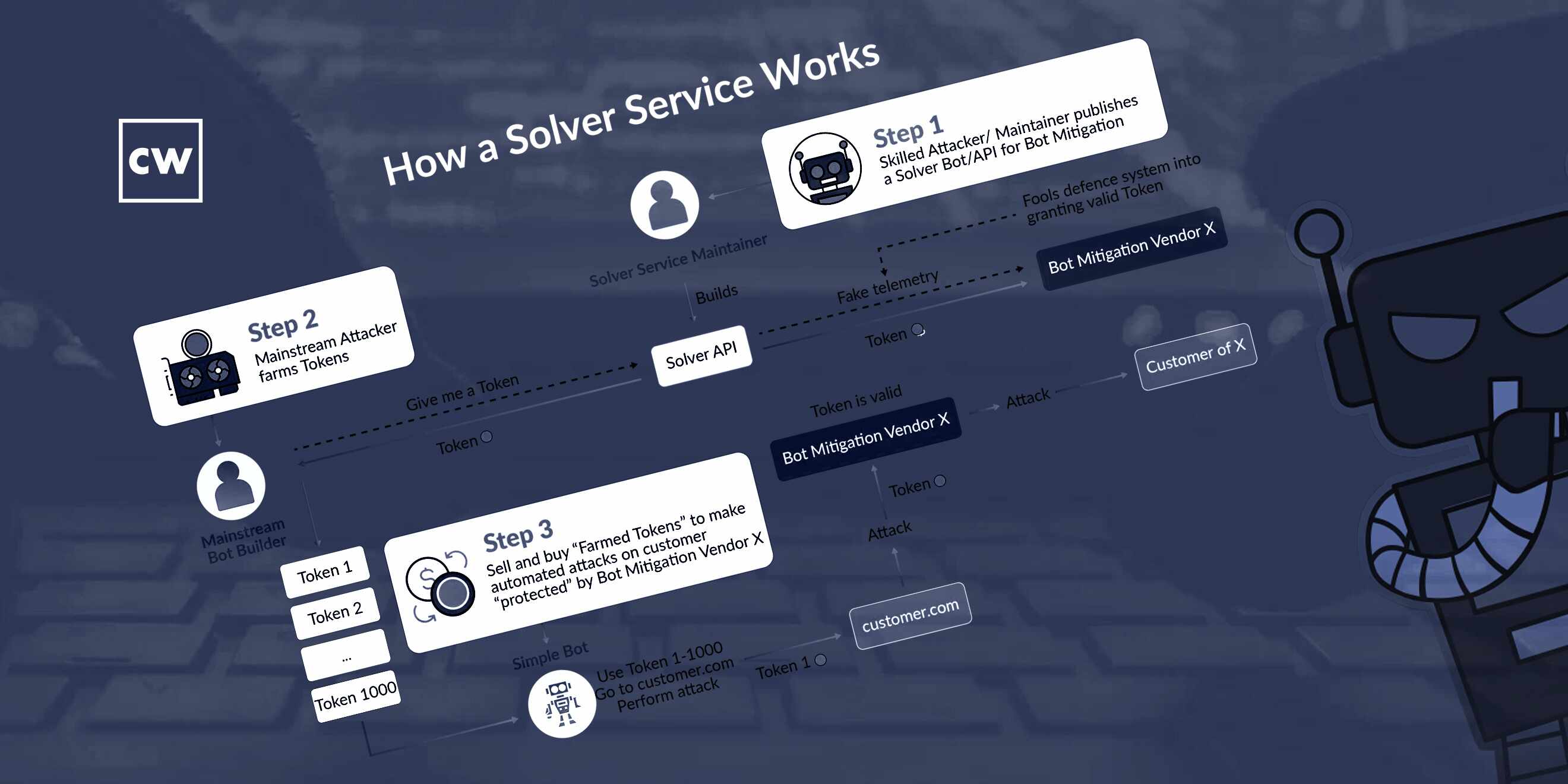
Sam Crowther: We actually uncovered this, you know, ecosystem of - that, you know, did not really exist a few years ago, and it's just been getting stronger and stronger. And that's this system of Solver bots, of Solver APIs that are being built and distributed to actually target specific anti-bot vendors and bypass them completely.
Dave Bittner: That's Sam Crowther. He's founder of anti-bot company Kasada. The research we're discussing today is titled "The New Way Fraudsters Bypass Bot Management."
Dave Bittner: Now, just to be clear, we're using the term Solver bot here, as in to solve a problem? Is that - I mean, is that where the phrase comes from?
Sam Crowther: Yeah. So, I mean, Solver, it being a generic term, I guess the succinct description of them is basically - their goal is to get a valid cookie to someone, you know, to abuse, right? That's essentially what they do. So I think where Solver comes into it is these anti-bot vendors have JavaScript challenges which need solving. And these, you know, adversaries have built tools to solve the challenges and return the valid responses in order to be classified as a human and, you know, let people abuse the back-end system.
Dave Bittner: Well, let's walk through this together. I mean, can we start off with just a description of how bot mitigation typically works?
Sam Crowther: Yes. So bot mitigation comes in two components. One is the client side, and then one is the network in session or the back-end side. So on the client side, a key part of any of this detection is understanding what's happening within the browser, right? Does this browser look real? Is it moving its mouse? Does it look like it has a human behind it? So that upfront, you know, detection component means that, you know, traditionally, botters have to be very, very sophisticated and skilled, you know, in order to be correctly classified as human.
Sam Crowther: The server side, or the back-end side is where it's looking at, you know, pattern analysis within sessions. OK, this session's human. What's it doing? How many login attempts is it making and things like that? Now, this has sort of evolved in sophistication, you know, over the last five or 10 years to the point where, you know, there is some very sophisticated client-side defenses and some awesome machine learning models on the back end. But, you know, inevitably, that's just changed the way these folk attack.
Dave Bittner: Well, let's dig into the attacks then. I mean, how are they coming at this?
Sam Crowther: So what they've realized is that, as the anti-bot vendors get better and better, it pushes the skill floor, essentially, like the minimum skillset required up in order to beat them. So there's a small group of people who, all of a sudden, have a very valuable skill, which they can sell en masse. And so what they've started doing is reverse engineering these JavaScript challenges - right? - And actually creating automated tools that, you know, reverse engineer them fully automatically, look at the data that they're expecting to be collected from the browser, feed legitimate data straight back to their APIs, and then obtain legitimate sessions.
Sam Crowther: And so they're doing this in a way that's actually got no browser whatsoever. And because, you know, some of these vendors are so ubiquitous, it means that the client base for them is absolutely huge. Like, we tracked the revenue of one of the big Solver API vendors, and they're making probably $150,000 a month selling this service. And all they need to do is maintain their little decoder to correctly interpret the JavaScript and send the correct information to the anti-bot vendor.
Dave Bittner: Wait. How sophisticated of an effort are we talking about here?
Sam Crowther: So this definitely depends on the specific vendor, as some are definitely less sophisticated than others. And look. I would say none of the adversaries are, you know, Ph.D.s or anything like that. A lot of them are just people who are interested in bots, who understand the way browsers work, and have realized this is a good way to make some cash. All right. So they're very smart individuals, but it's not like they, you know, these sophisticated crime rings or anything. Like, usually, it's just, you know, one or two people who realize they've got a valuable skill.
Dave Bittner: Can you take us through an example of one of the sessions that you all have tracked here?
Sam Crowther: Yeah. So what we've seen for some of these Solver APIs is actually where they're used in fraud. So let's say a fraud group wants to, you know, wash a million credit cards, which is some activity we've seen through a payment provider. What they'll do, instead of building something themselves, they approach one of these Solvers and they say, OK, I want to buy a million sessions. And I want an SLA that all of them will work. And if any don't work, you replace them. So they'll take those million sessions and then they will load them into their bot in order to go and actually, you know, commit the act of fraud that they wanted to, you know, I guess they set out to. And so this has become more and more common - right? - where these fraudsters have realized they can just pay a little bit of money and outsource one of the most difficult parts of any sort of fraud operation, which is beating security systems.
Dave Bittner: And so what's the cat and mouse here? I mean, in terms of, you know, the folks whose websites are falling victim to this, what's to be done there?
Sam Crowther: Look. This is a responsibility of the anti-bot vendors, right? That's where the game is. There is, you know, very clear difference in folk and their ability to iterate and prevent this sort of behavior. And, you know, understanding that this is even a problem is the first step to being able to solve it. But, you know, it shouldn't fall on the customer. This is absolutely the responsibility of the individual providing the service. And look. What we're starting to see is it's, you know, it's evolved from the anti-bot vendors, but it's starting to move also into some of the anti-fraud vendors as well. And, you know, if that trend is to continue, it won't be long before, you know, someone can buy an off-the-shelf solution to beat most e-commerce website security products.
Dave Bittner: How do I know if I have a problem here?
Sam Crowther: Look. This is one of the interesting and also scary parts of this - right? - is their whole business model is getting sessions that look good and that are valid. And so look. Usually, the best way to figure out if there's a problem is actually look at your own web traffic data. All right? If you look at, say, login requests or checkouts over the last two months, what pattern does it follow? Does a follow day-night cycles? Does it look like human activity? Does it spike up and down, you know, sort of sporadically? Those are actually the best indicators that something like this is going on, because unfortunately, you can no longer rely on the data and reporting from a vendor when this sort of threat is very, very real.
Dave Bittner: So what sort of questions should I be asking my vendor? I mean, if, you know, if I'm engaged with someone who is selling me services to protect me against bots, how do I make sure that they've got the latest, greatest stuff out there to keep me safe?
Sam Crowther: I think this is very much a dialogue around, you know, how aware of the problem are people and understanding their strategies to address it, right? I mean, it's going to be different for everyone. But making sure that they can actually articulate this is what we actively do to combat this type of activity is very important because, you know, what we see is people sort of hand wave, oh, we have machine learning, we have this, we have that. And the reality is none of that really matters if someone can send the data that's expected to the machine learning model, right? ML is only as good as the data it gets. So it's very important that any vendor in this space has a very active strategy to, you know, almost dismember this type of solving activity.
Dave Bittner: Can you walk us through some of the technical aspects here? I mean, what specifically are the Solver services doing under the hood?
Sam Crowther: Yeah. So what they're typically doing is decompiling the JavaScript that gets delivered to the client, transforming it into a, you know, a format that they can easily interact with it in, and then looking at what sort of data attributes it's expecting from the client. It will then rebuild essentially the entirety of a virtual browser to make sure all the data is legitimate and then package that up and send it to the client. So it's a relatively streamlined process, which means it's very cost-efficient for a lot of the folk building and selling them.
Sam Crowther: And where would someone go to buy this sort of thing?
Sam Crowther: You head to discord, head to various hacking servers. Honestly, it's actually very, very accessible. It's not like it's on the dark web. You know, it is something anyone really who wants to get access to it can.
Dave Bittner: Do you suspect that, you know, we're in a cat-and-mouse game for the foreseeable future here?
Sam Crowther: Absolutely. Like, what they're doing is not illegal, which is unfortunate. They are actively bypassing security systems, yet they're not the ones committing the crime. And so I think they leverage that in their justification, I guess, of what they're doing.
Dave Bittner: Our thanks to Sam Crowther from Kasada for joining us. The research is titled "The New Way Fraudsters Bypass Bot Management." We'll have a link in the show notes.
Dave Bittner: The CyberWire podcast is proudly produced in Maryland out of the startup studios of DataTribe, where they're co-building the next generation of cybersecurity teams and technologies. Our amazing CyberWire team is Rachel Gelfand, Liz Irvin, Elliott Peltzman, Tre Hester, Brandon Karpf, Eliana White, Puru Prakash, Justin Sabie, Tim Nodar, Joe Carrigan, Carole Theriault, Ben Yelin, Nick Veliky, Gina Johnson, Bennett Moe, Chris Russell, John Petrik, Jennifer Eiben, Rick Howard, Peter Kilpe. And I'm Dave Bittner. Thanks for listening. We'll see you back here next week.


