Over-the-air 0-day vulnerabilities.
Dave Bittner: Hello everyone, and welcome to the CyberWire's "Research Saturday." I'm Dave Bittner, and this is our weekly conversation with researchers and analysts, tracking down the threats and vulnerabilities, solving some of the hard problems of protecting ourselves in a rapidly evolving cyberspace. Thanks for joining us.
Roya Gordon: So we started looking into it because the IEEE - they came out with an amended standard. The standard - whole bunch of numbers. It's, like, 802.15.4z - and it was said to kind of increase security of these devices.
Dave Bittner: That's Roya Gordon, security research evangelist at Nozomi Networks. The research we're discussing today is titled "UWB Real Time Locating Systems: How Secure Radio Communications May Fail in Practice."
Roya Gordon: So, you know, obviously, whenever there's new standards, we take a look at it. And we noticed that there's a little loophole in it where it kind of covers part of the technology or the data transmissions with these devices, but not the other part. And then digging into it further, we realized, wow, a threat actor could launch a man-in-the-middle attack and really manipulate the information and the data and the location of things via these devices. So that's kind of how it all started.
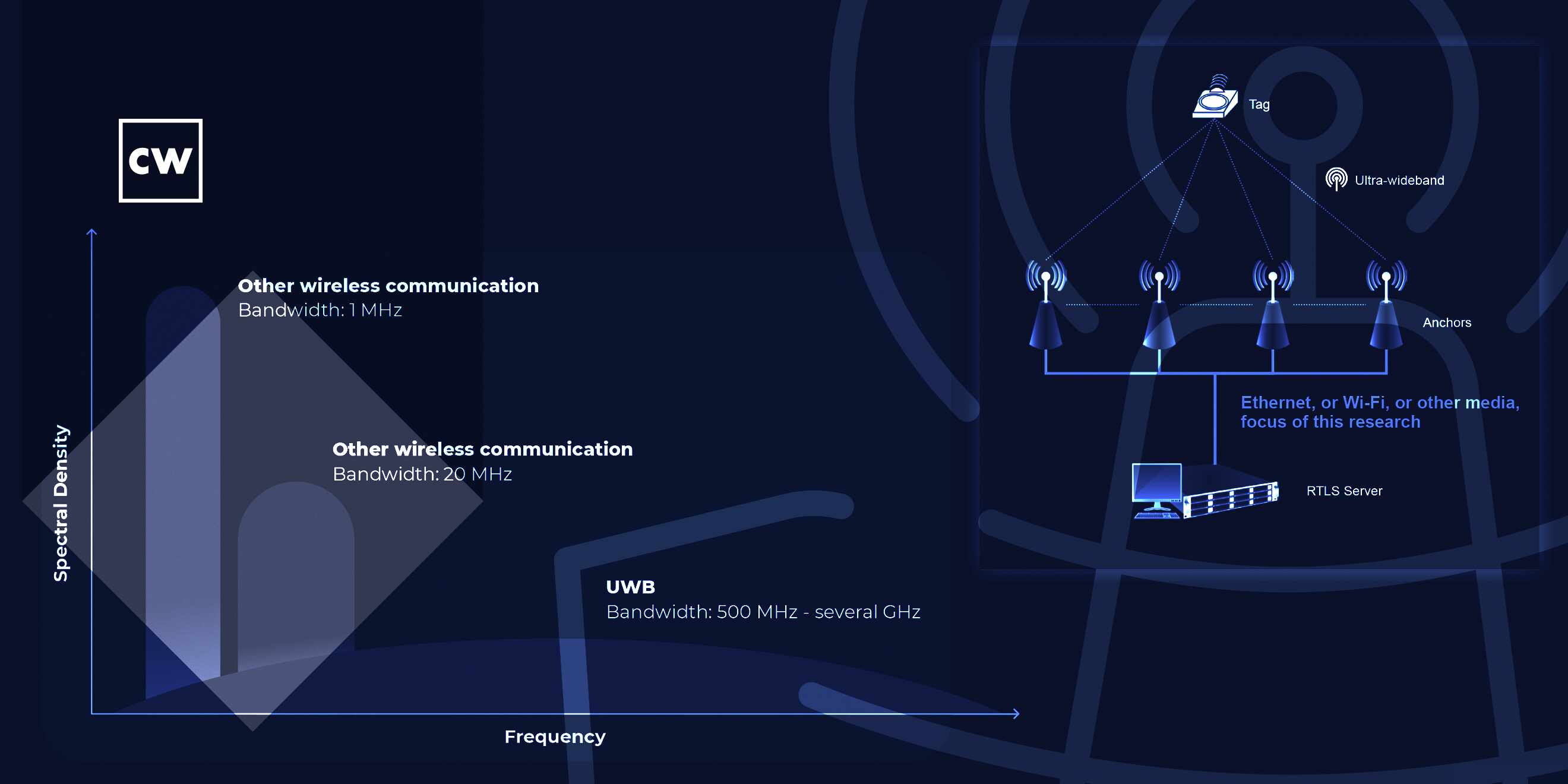
Dave Bittner: Well, at the core of this, when we're talking about these devices - this is ultra-wideband devices - that's UWB - and real-time locating systems - RTLS. What are these devices, and typically how do they get used?
Roya Gordon: So these devices - they're used everywhere. We may not see it all the time, but they're used in different industries, in smart cities, in buildings. One of our main use cases - and we did a demo on this at BlackCat - was in a manufacturing plant. Now, the reason why RTLS is used is because personnel need to be tracked, equipment that's moving around need to be tracked. You know, there's different hazardous areas in those environments. So there needs to be a way to track people to make sure that they're safe. So it is kind of used as a safety thing.
Roya Gordon: Now, ultra-wideband - that radio frequency protocol is preferred because it can transmit via barriers. So, you know, Wi-Fi and all these other types - if you - if there's some type of barrier, if it's not line-of-sight, then you're not going to get the best location or precision. But with UWB, it can transmit through equipment, through walls. So in a big plant where there's all this stuff going on, it's kind of the ideal protocol to use.
Roya Gordon: So the real-time locating system - it's comprised of three main components. You have the tag that's attached to a person or an item. So again, that's going to be the tracking. You have anchors that are placed throughout various parts of the facility, and then you have the server. The anchors - they transmit all of this data back into the server. So that's the system, and then the ultra-wideband is the protocol, the radio frequency that's being used.
Dave Bittner: So just for my own understanding here, I mean, is it basically that the tag - the transmitter that's on someone or something, that's sending out some kind of ping, and then the anchors receive that ping and then report back to the server as to where they're, I guess, triangulating where that tag is?
Roya Gordon: Absolutely. Yep. That's exactly what goes on.
Dave Bittner: OK. So let's dig in to the security elements here. I mean, what security is claimed to be in these systems, and then how did you all go about exploring whether that was actually the case?
Roya Gordon: Yeah, so pretty much the amendment - it secures the transmission of data between the tag and the anchor. So, you know, everyone can say, OK, that's good recovered. But when that data is transmitted to a server, that's when everything is just vulnerable. That's where a man-in-the-middle attack can be launched. And that's where that, regardless of whether the data between the tag and the anchor is secure or not, you get to see everything as it's being transmitted to the server. So once we realized where the loophole was, we decided to purchase the equipment and do the testing ourselves.
Roya Gordon: So we have our lab in Mendrisio, Switzerland, and that's where we do all of our security research. We have demos there - everything you can think of. So we purchased some devices, and we started testing it out ourselves on our own production line demo. And this is where it got really interesting at BlackCat because we were able to create a geofencing zone around this demo and have a person wearing the tag go close to the production line, look at the system, see that there's notifications. So we didn't just do, like, a research on it. We actually tested it out. And we were able to launch a man-in-the-middle attack and manipulate the tags and everything like that. And I do want to use some of the three examples that we used in our presentation that could kind of help piece this all together.
Dave Bittner: Yeah.
Roya Gordon: So the first one is contact tracing for COVID-19. You know, that was a huge thing. And, you know, in any kind of work environment, maybe it's important to track which employees are COVID-positive, that are in contact with others. An alert is generated. You know, we understand that concept. But when we launched the attack - so did what the attacker would do - it was able to manipulate the alerting so you could be in contact with someone who is COVID-positive, and you won't get alerted. Or you could be in contact with someone that doesn't have COVID, but then an alert is generated saying that you've been in contact with this. And the question is, you know, why would a threat actor want to do this? Why do they care about who has COVID and who doesn't? If you're able to kind of fabricate a percentage of the workforce having COVID and needing to call out, you know, that's a lack of resources to be able to run a facility in a productive type of way.
Dave Bittner: Right.
Roya Gordon: So that was kind of how it started. But then we took it a level up to say, OK, how can this be a real problem that impacts safety? Because we know manufacturing plants, mostly industrial controls - mostly industrial facilities, safety is a big issue. So we were able to show that if a worker is conducting maintenance on a piece of machinery that's supposed to be down, maybe the threat actor goes in, manipulates the tag, shows that the worker has left that hazardous area, and that could prompt the machinery to automatically restart while someone is in close proximity, while doing active maintenance. So now it becomes a safety issue where someone could be harmed - their life in danger. And that was also another use case that we were able to demonstrate.
Dave Bittner: Yeah, and one of the things you highlighted was that these systems often get used in hospitals with patients. I could imagine some real safety issues there, as well.
Roya Gordon: So, yes, using it in hospitals or just anywhere where you're locating people or assets, it could be used to misplace where critical patients are, critical equipment that you need to - you need for surgery. Anything that could have a tag associated with, the threat actor can go in and either misplace things or it can actually track items that, you know, a threat actor wants to steal. This could be used for reconnaissance. Maybe they just want to know what's going on in a hospital so that they can launch a broader attack afterwards.
Roya Gordon: So this being used in hospitals - especially with the COVID-19 because there's a lot of that testing going on. So if there are systems that aren't properly tracking or keeping track of who has COVID and who doesn't, especially in a hospital, you know, that's kind of a big deal. I know that for medical procedures, there's mandatory COVID testing before you can even get operated on. So, yeah, it's a pretty big deal. We focused on those three use cases - the contact tracing, locating and targeting people and assets and then the geofencing.
Dave Bittner: So the white paper goes into a lot of the technical detail here. And, dare I say, there is a lot of math in there that is over my head. But I'm glad you and your colleagues have a deep understanding of this stuff. And for folks who are interested, it's all there. But just looking at the bigger picture of this sort of thing, of being able to go in and do this - you know, have a man-in-the-middle attack on a system like this - why is this something that we should be concerned about? Are - do you think there are real-world cases here where bad actors could take advantage of this?
Roya Gordon: Absolutely, Dave. So I mentioned that we started off just kind of buying a smaller RTLS, you know, just to do this research. But now we're taking it a level up, right? Airports use this, right? It's different brands, different models. But now we're looking at, what are the broader implications of a threat actor intercepting location data in airports? Or we looked at some brands - and I don't want to call anyone out, but we looked at some brands, we looked at where they're deployed. And we're talking about, you know, airplanes. We're talking about military. So it started off really small, with just us noticing a loophole in a standard. And now it's getting really big to, OK, if the standard isn't really covering or securing all parts of the system, then what else can we do? So we're hoping within the next year to kind of highlight this as a bigger and broader problem.
Roya Gordon: And then there actually has been, like, bigger companies that's reached out to us because of this research, because they're like, OK, well, how do we help secure this for our end users? So - and that's why I'm happy that we're able to be on this podcast to talk about the impact of this research. But, yeah, it is a pretty big deal. If you look at it from contact tracing or moving tags around, it's like, OK, whatever, who cares? But if, you know, there are missing critical assets or, you know, think of pipelines, think of nuclear facilities. You know, if you're not able to track where people are and where things are, I mean, the event could be catastrophic.
Dave Bittner: Right, right.
Roya Gordon: And we don't know the rhyme or reason why threat actors do these things. But they do it for fun. They do it to cause damage, you know, depending on the threat actor. Especially if they're a nation-state, you know, they're trying to take things down. They're trying to cause harm. So regardless of what their motive is, they shouldn't be able to have access to this type of system.
Dave Bittner: And, I mean, this is the kind of system that you need to have confidence in because, as you say, there's - there are safety issues here.
Roya Gordon: Yeah. And even though geofencing - it's not - RTLS, they're not the only systems that use geofencing. But just as an example, I have an Oculus. And I don't know if you have one too, but when you put that thing on, you have to create a geofencing zone or area that you stay within, so as you're in this VR world, you know if you get too close to something, OK, that's going to be outside of this geofencing area. If you step outside, that could be some stairs. You could walk into a sharp object.
Dave Bittner: Right, right. Run into a wall.
Roya Gordon: (Laughter) Exactly. So, you know, I'm trying to make it relatable to the everyday person. But if you look at it like that, it's like, OK, we know the importance of creating geofencing zones, and now taking that and putting that in a dangerous environment where things can be manipulated, yeah, it is kind of a big deal.
Dave Bittner: So as you were looking at this and examining the different brands, you know - again, we don't have to call anybody out or name any names - but was there a spectrum of attention to this? Were different brands, you know, taking a different level of care here? Can - if I'm someone shopping around for this, is it possible for me to invest in a system that is more secure than one of the competitors?
Roya Gordon: So here's the thing. When the standard - the amendment to this IEEE standard came out, it still - it kind of put the responsibility of securing these devices up to the vendor. And, you know, so it didn't really secure protocols. It didn't really secure in the broader sense. But it kind of said, hey, if you're the vendor and you're developing this, you need to make sure it's secure. But there was really no way - there was no guidance on how to secure this, right? And I get it. We trust vendors. But a lot of the times, they're focused on the quality of the product. And if they're doing updates, it's like implementing new features. And that's why we have security research teams, right? Because maybe they don't have the capacity to try to find vulnerabilities in their own product.
Roya Gordon: But it kind of creates this gap where now, if there's no standard, there's no know-how, there's no policy kind of guiding these vendors into how to secure this communication, no one's going to do it, or no one even knows that it's a problem. The team - we scrubbed the internet. We tried to find - is there any research out there talking about this? And there wasn't. So that's why we focused on this because it's a loophole that no one's paying attention to, and it's wide open for threat actors. And we actually released mitigations. So we tied this into our white paper. There's links there. But we're just like, hey, here's a mitigation that we created on GitHub. Here are additional recommendations. But at the end of the day, it's up to the vendor to kind of bake that into their product. And hopefully, again, as this gets more publicity - we've already been working with some vendors that are interested in learning how we figured this out and what to do. But yeah, there's not a lot of research or guidance for how to secure these.
Dave Bittner: So before we go, in the time we have left, beyond publishing the white paper on this, you all did a presentation on this. And my understanding is it was very well received.
Roya Gordon: Yes, it was. So I'm so happy that my company allows me to bring my creativity into these presentations. So I have this idea. I know how to do the Rubik's Cube, by the way. And it's just kind of this fun thing I know how to do. But do I do anything with it? No, I just - I bring my cube on a flight. I, you know, tinker around with it. And I was like, you know what? Why don't we figure out a way to tie this into the presentation somehow? So they were game.
Roya Gordon: And what we did - we started off the presentation. I gave the introduction about, you know, the importance of these systems and, you know, where they're used and the loopholes we found in the amendment. So while I'm doing that, I'm playing with the cube. I'm mixing it up. And then I say that the challenge for all of this security to be put on the vendor can be puzzling and challenging. And I'm holding up the cube while I'm saying that. And then, you know, we continue throughout the conversation. I'm just kind of messing around with the cube. I don't think people really know what I'm doing. But as I close out the presentation, you know, I'm starting - people are starting to see that I'm piecing it together, and it's, like, almost solved.
Dave Bittner: (Laughter).
Roya Gordon: And then at the end, I'm like, you know, yeah, this can be challenging and puzzling. And then I do this one last move, and I'm like, but it can be done. And I hold up the cube that's completed. And I didn't think a lot of people caught that. But afterwards people - they were like, wait, we really liked how you tied that together. So to me...
Dave Bittner: Nice.
Roya Gordon: ...That was the funnest part, being able to just take, like, a cool trick that I've been doing for years and kind of helping tie it together into an important message to such a technical audience.
Dave Bittner: Yeah, we should get you together with Jen Easterly from CISA and have a race.
Roya Gordon: No. I've seen her do it, like, blindfolded, behind her back. There's no competition there.
Dave Bittner: (Laughter) OK, fair enough.
Roya Gordon: It takes me, like, 2 1/2 minutes. I can't compete
Dave Bittner: I see. OK. All right, well, that's better than me. I can't do it at all.
(LAUGHTER)
Dave Bittner: All right. Well, Roya Gordon, thanks for joining us.
Roya Gordon: Thanks, Dave.
Dave Bittner: Our thanks to Roya Gordon from Nozomi Networks for joining us. The research is titled "UWB Real Time Locating Systems - How Secure Radio Communications May Fail in Practice." We'll have a link in the show notes.
Dave Bittner: The CyberWire podcast is proudly produced in Maryland out of the startup studios of DataTribe, where they're co-building the next generation of cybersecurity teams and technologies. Our amazing CyberWire team is Rachel Gelfand, Liz Irvin, Elliott Peltzman, Tre Hester, Brandon Karpf, Eliana White, Puru Prakash, Justin Sabie, Tim Nodar, Joe Carrigan, Carole Theriault, Ben Yelin, Nick Veliky Gina Johnson, Bennett Moe, Chris Russell, John Petrik, Jennifer Eiben, Rick Howard, Peter Kilpe, and I'm Dave Bittner. Thanks for listening. We'll see you back here next week.


