DUCKTAIL waddles back again.
Dave Bittner: Hello, everyone. And welcome to the CyberWire's "Research Saturday." I'm Dave Bittner. And this is our weekly conversation with researchers and analysts tracking down the threats and vulnerabilities, solving some of the hard problems of protecting ourselves in a rapidly evolving cyberspace. Thanks for joining us.
Mohammad Kazem Hassan Nejad: So in the past year, I've been investigating and tracking this financially motivated cybercrime operation that's based in Vietnam.
Dave Bittner: That's Mohammad Kazem Hassan Nejad from WithSecure's intelligence unit. The research we're discussing today is titled "DUCKTAIL Returns: Underneath the Ruffled Feathers."
Mohammad Kazem Hassan Nejad: And we initially got notice of this operation through a sample that we received from our threat hunters that run our managed detection and response service.
Dave Bittner: Well, let's go through it together here. From a high level, who are these people targeting?
Mohammad Kazem Hassan Nejad: So the operation targets individuals and businesses that operate on Meta or Facebook's business and ads platform. And that's basically a platform that a company would use to run and manage Facebook pages and ad campaigns across Meta's different platforms, such as Facebook and Instagram.
Dave Bittner: Well, let's go through it together here. How would someone find themselves falling victim to this?
Mohammad Kazem Hassan Nejad: So the threat actor primarily targets those that are in the digital marketing and advertisement vertical, as those are folks that make - most likely make use of Facebook's business and ads platform. The threat actor first scouts for these victims and targets them through mediums such as LinkedIn and WhatsApp by sending them attachments that supposedly contain things such as business and advertisement proposals for different brands such as L'Oreal. And even recently, we've been seeing the threat actor using lures that contain the Christmas theme as Christmas is approaching.
Dave Bittner: That's interesting. So someone gets one of these attachments, but what's in the attachment there? What kind of malware is contained within?
Mohammad Kazem Hassan Nejad: Yeah, so the attachment actually contains an information-stealer malware that is disguised, like I mentioned, as a project plan or a business proposal. And once the victim executes the information-stealer malware, the malware then proceeds to exfiltrate information from the victim's machine and Facebook account if the victim has logged on to their Facebook account on their device and also automatically attempt to add the attacker's email address as an administrator with finance editor role into any business that the victim might have access to.
Dave Bittner: Well, let's talk about the Facebook aspect of this. Can you give us a little bit of the background here? What are people typically doing on Facebook - the businesses, and what exactly are these bad guys targeting? What are the capabilities they're after within Facebook itself?
Mohammad Kazem Hassan Nejad: Sure. So basically, one of the biggest revenues and profits for Meta and Facebook is the ads revenue. And that's where Meta makes a lot - or most of their money from. And a lot of companies use Facebook and Meta's advertisement platform and business platform to reach the user base that Meta provides. And they're - the advertisement agencies and digital marketing folk will use this platform to run ad campaigns for, let's say, a specific product that they might be launching soon. And in there - and these assets are basically controlled through a business account that is linked to the company. And the business account will have basically personal Facebook accounts that will, like, manage certain assets in that - or for that business. And with the business account, there will be a payment method that will be linked to it that's used for running these ad campaigns. And what the threat actor is basically after by hijacking these Facebook business accounts, by adding themselves as a administrator with finance editor role, is to get access to this business' payment methods to then leverage it in order to run fraudulent ads.
Dave Bittner: So what kind of ads would they be running? What sort of things are they after here? Are they selling ads to someone else? are they running things for themselves?
Mohammad Kazem Hassan Nejad: Well, the evidence strongly suggests that the goal of the operation is to gain access to the business accounts and use the hijacked business' advertising credits and payment methods to run fraudulent ads. But because this sort of information is not really visible to us, we've only been able to see some of the advertisements that have been run through hijacked or compromised business accounts through our incident response cases. And in those cases, they were mainly fraudulent ads that seemed - that seem legitimate. But what we believe the business model basically behind this operation is to probably provide advertisements for a much lower rate than what Meta would offer.
Dave Bittner: So are they trying to be stealthy at all here? Once they get access to someone's Facebook business account, are they trying to fly under the radar, or are they trying to, you know, burn through as much as they can, as quickly as - can until their access is cut off?
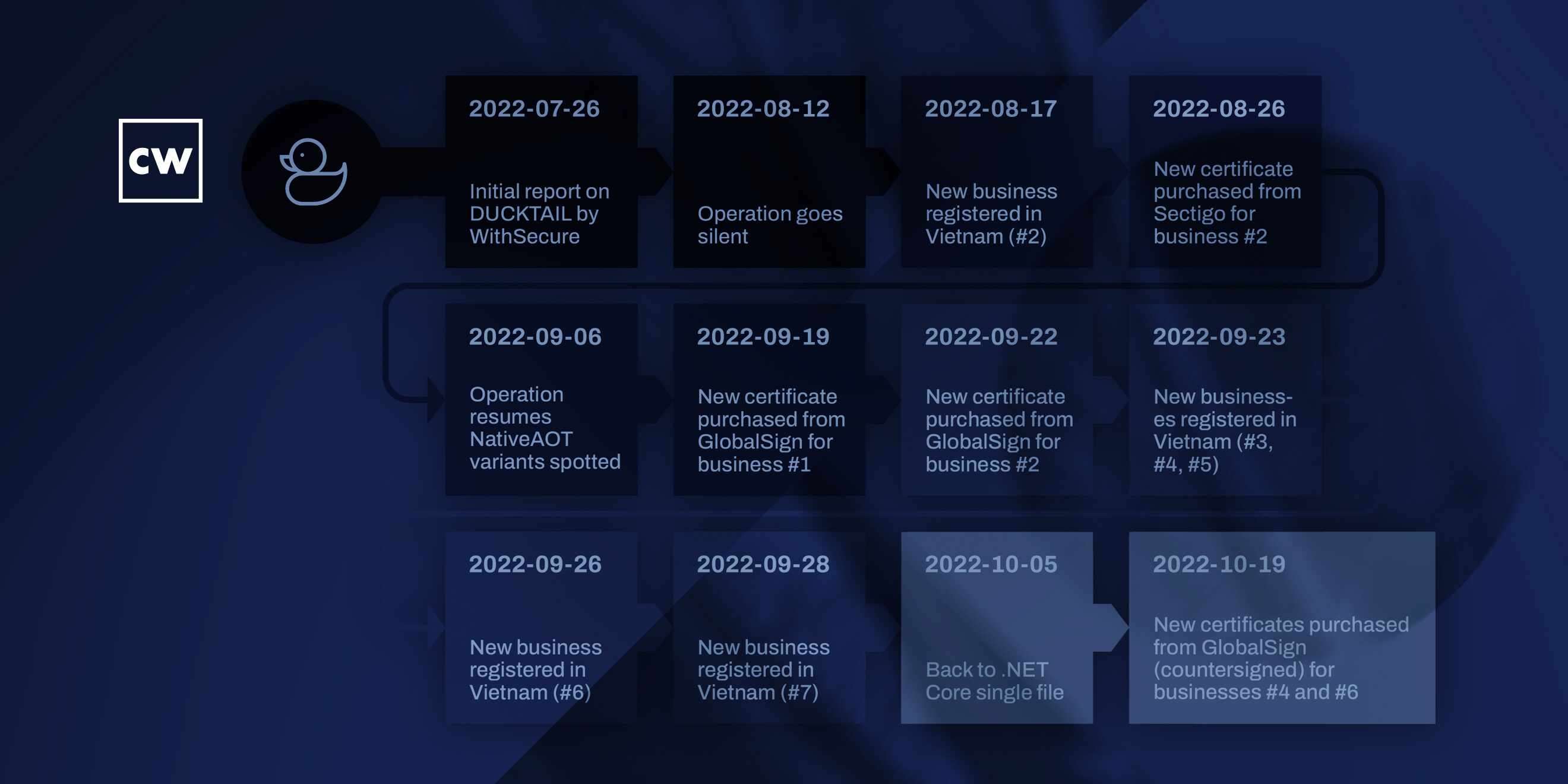
Mohammad Kazem Hassan Nejad: Yeah, absolutely. I mean, the whole operation - so the operation consists of - the attack lifecycle basically consists of multiple stages that cross multiple platforms. So starting from the - how the victims are basically targeted. So usually with malware, you see malware being delivered through malicious spam campaigns. So a lot of victims might get a malicious attachment. But with this basically campaign, the threat actor directly targets those that they believe have access or make use of Meta's business and ads platform. So right off the bat, they're specifically targeting individuals that they believe might have access to fly under the radar. And then the malware - or the information stealer malware actually makes use of different techniques in order to bypass different detection mechanisms. For instance, the - since mid-2021, the time that we believe the campaign had started, the threat actor has been making use of certificates to sign their malware with extended validation. And in order to do this, they actually need to set up or have a business that they can register a certificate for through a certificate authority. And that's a very rigorous process in order to get an extended validation cert.
Mohammad Kazem Hassan Nejad: So there's a lot of, like, resource development that goes in there. And what having a signed malware basically does with extended validation, we believe this will bypass Microsoft SmartScreen. So these attachments, as they look like business proposals, the icon will look like a PDF or a spreadsheet. And obviously, if you double-click on it, as it's an executable, if it's an unknown or unverified sample, then the SmartScreen would prompt and that would tell the victim that - it would raise suspicion that this is probably not a PDF file because it's saying that it wants to execute something. Then in order to bypass this, they're making use of the extended validation certificate and they - in the latest variants, we've seen them also launch dummy files to make it look, like, legitimate.
Mohammad Kazem Hassan Nejad: For example, if it's a - it looks like a spreadsheet, it will actually launch a dummy spreadsheet file just to make it look like it's actually legitimate. And then once they manage to get access to the Facebook business account, that point onwards - there's two ways, actually, like, they can do it through a hands-on attack because not all victims might have a high-level access to the business account to be - to add the threat actor's email address as an administrator. So they will rely on a hands-on approach where they will impersonate the victim to achieve their post-compromise activities.
Dave Bittner: Well, let's go through some of the actual capabilities of the malware. In your research, you list what it's capable of here. Can we go through that together?
Mohammad Kazem Hassan Nejad: Sure. Absolutely. So basically, once the malware is launched, it will start looking through the device for all the cookies that someone has in their browser. And if it finds an authenticated Facebook session - so once you log into Facebook and you press that - the remember me, it actually has an authenticated session as a cookie that's stored on the device. And it will use that in order to basically steal information from the victim's personal account, Facebook personal account, and also look whether the personal account has any businesses linked to it. And if it does, then it will use the victim's access to that business to add themselves into the business account. And whether or not it's successful, it exfiltrates all the information that it steals from the victim's machine, including all the browser cookies and the personal account information and business account information, and exfiltrates all of this to the threat actor's command-and-control channel, which since late 2021, has been Telegram.
Dave Bittner: Yeah, that's an interesting aspect on its own there - right? - that they're using Telegram for C&C?
Mohammad Kazem Hassan Nejad: Yeah, absolutely. Actually, the threat actor initially set up their own infrastructure and had their own domains linked to the operation, but then in late 2021, we actually saw the shift to using Telegram. And this, first of all, leaves a lot less fingerprints because they no longer have an infrastructure that they need to manage and that gets linked to the operation. And obviously, Telegram makes it easy, through their API, to set up a command-and-control server where you can directly communicate, you can send commands and then receive information as, like, an archive file. So it makes it quite easy to manage, basically, for the threat actor. So - but the downside of that is that we can actually observe and monitor and track the activity that we see in the command-and-control channel because they have to provide an API key that the malware will use in order to communicate with the command-and-control channel in the first place.
Dave Bittner: Yeah, that's interesting. So what are your recommendations, then, for people to best protect themselves against this?
Mohammad Kazem Hassan Nejad: It's quite lucrative and difficult to actually protect against these sort of attacks. And there's no single solution because the attack lifecycle spans across multiple platforms. So first off, in order to avoid these spear phishing attempts, it's vital to raise awareness on this form of spear phishing attacks among users that have access to Facebook or Meta business accounts. And as the malware utilizes an information-stealer malware that's designed for the Window - for Windows machines, it's vital for victims to run either EDR or EPP solutions to prevent and detect the malware in the earlier stages of the attack lifecycle. And obviously, it's also vital to - for a victim or for a user to have basic hygiene and protection in place on their personal and managed devices. And that's something that's quite - that makes this quite difficult to protect against because for Facebook business accounts, basically a victim actually has their personal account associated to it. So they're going to have logged onto their personal accounts from both personal devices and managed devices, and that means that they need to basically have basic hygiene in place and protection in place across all different devices that they might log into their Facebook account through. And lastly, on the Facebook platform itself, it's important to follow Meta's recommended security practices.
Dave Bittner: I would imagine, too, that, you know, a lot of Facebook business users, you'll have multiple people who have access to that business account, and because there may be multiple people, that may make it harder to know if there's someone there who doesn't belong.
Mohammad Kazem Hassan Nejad: Yeah, absolutely, and this is one of the difficulties with these sort of attacks. But I believe that there are notifications, for example, that are sent out, and there are some security features in place on the - on Meta's platform, and that's why it's recommended to follow what Meta recommends on their platform to avoid the sort of compromises from taking place on the platform itself. But like I mentioned, there are also basically things that someone can do before that to prevent these sort of attacks, and that comes from protecting their devices and following basic hygiene, as well as ensuring that they're aware of these form of attacks so they don't click or download a suspicious or malicious attachment in the first place.
Dave Bittner: You pointed out that the evidence indicates that this is a Vietnamese threat actor. Are they going after anyone in particular? Is there a geographic area that they're targeting? Or are they just general opportunists?
Mohammad Kazem Hassan Nejad: Not really. Yeah, they're basically general opportunists, as we see them primarily target companies that work in the advertisement and digital marketing vertical, but we don't see a specific geographical region that they're targeting. But some of their attachments are quite targeted. For example, they will have the country name appended to it. So that means that the threat actor is well aware of their victims before targeting them, where they're located and what their role is, and they use these in order to craft the malware name and whatnot to make it look more innocent, basically, to the victim.
Dave Bittner: Our thanks to Mohammad Kazem Hassan Nejad from WithSecure for joining us. The research is titled "DUCKTAIL Returns - Underneath the Ruffled Feathers." We'll have a link in the show notes.
Dave Bittner: The CyberWire's "Research Saturday" podcast is a production of N2K Networks, proudly produced in Maryland out of the startup studios of DataTribe, where they're co-building the next generation of cybersecurity teams and technologies. Our amazing CyberWire team is Elliott Peltzman, Tre Hester, Brandon Karpf, Eliana White, Puru Prakash, Liz Irvin, Rachel Gelfand, Tim Nodar, Joe Carrigan, Carole Theriault, Maria Varmazis, Ben Yelin, Nick Veliky, Milly Lardy, Gina Johnson, Bennett Moe, Catherine Murphy, Janene Daly, Jim Hoscheit, Chris Russell, John Petrik, Jennifer Eiben, Rick Howard, Peter Kilpe, Simone Petrella, and I'm Dave Bittner. Thanks for listening. We'll see you back here next week.
