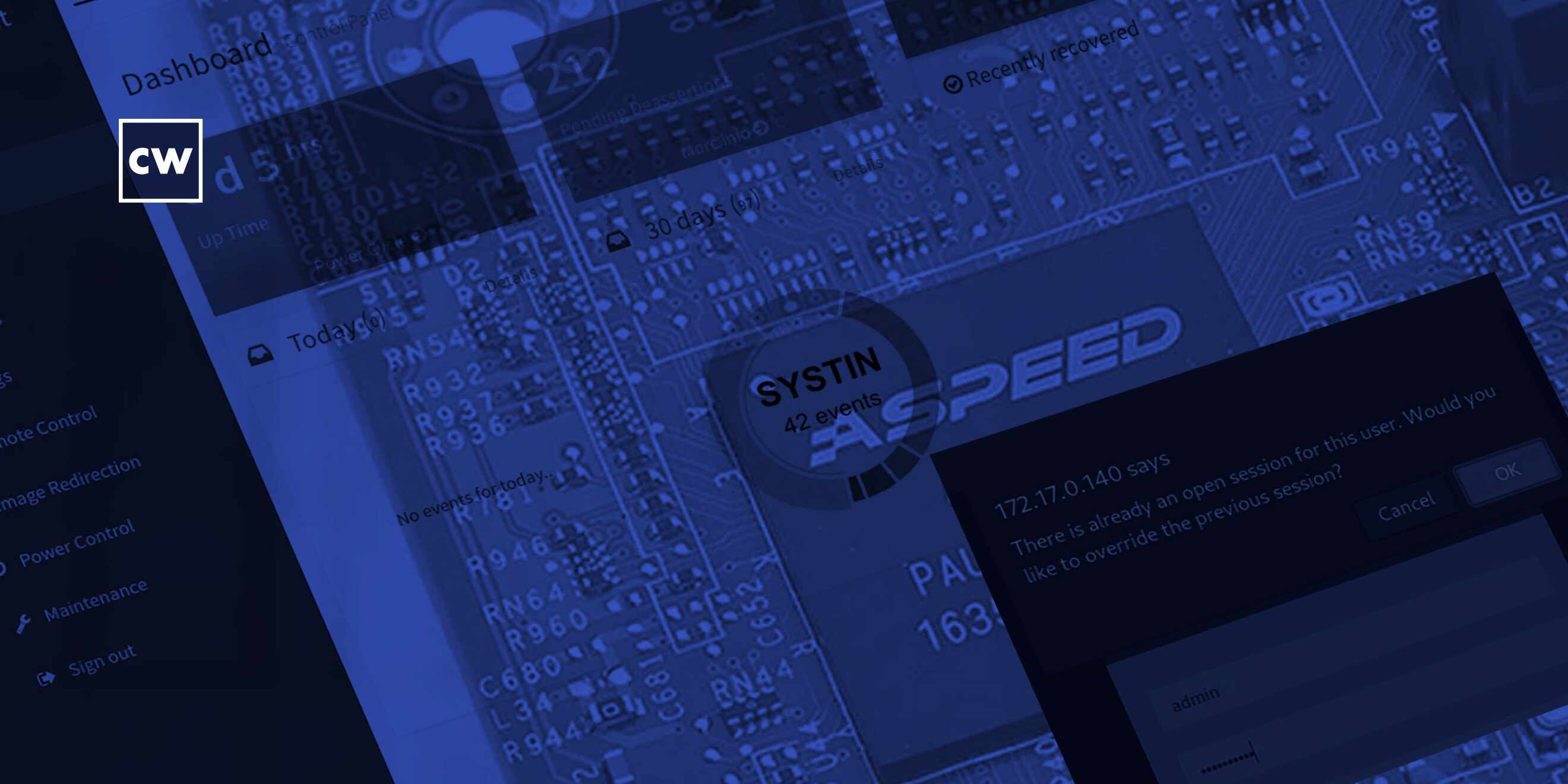
Flagging firmware vulnerabilities.
Dave Bittner: Hello, everyone, and welcome to the CyberWire's "Research Saturday." I'm Dave Bittner, and this is our weekly conversation with researchers and analysts tracking down the threats and vulnerabilities, solving some of the hard problems of protecting ourselves in a rapidly evolving cyberspace. Thanks for joining us.
Roya Gordon: So a baseboard management controller, also known as a BMC, it's used for remote monitoring and management of a computer.
Dave Bittner: That's Roya Gordon. She's an OT and IoT security research evangelist at Nozomi Networks. The research we're discussing today is titled "Vulnerabilities in BMC Firmware Affect OT and IoT Device Security."
Dave Bittner: And are there particular systems that they go in or are not included in?
Roya Gordon: So this was used in IT before, but now vendors are trying to expand this into IoT and OT devices. Of course, like any type of remote control of a device that's far away, you want to take advantage of that. It's very convenient. So now we're starting to see vendors create things called expansion cards that bridge the gap between physical devices and the internet. And that's kind of where our vulnerabilities come into play because anything that's OT, IoT and attached to the internet is vulnerable.
Dave Bittner: Well, let's dig in here. I mean, how does this affect OT and IoT installations?
Roya Gordon: So with these expansion cards, it's giving the device a capability that it didn't previously have, so expanding the capability. So when our labs conducted the research, we found a vendor who makes these web application expansion cards that gives users root privileges at the device level. And although, again, this is a very convenient piece of technology, we know anything connected to the internet is going to get compromised. And that's kind of why we wanted to push this report out right away. I know this is a part one. Part two is pending because we're still looking into this. And even if you look at the report, we didn't delve into all 13 of the vulnerabilities. We only highlighted the critical ones. And I'm really excited to talk to you about that today because once I was reading through this with the team, I'm like, wow, I think that a lot of people need to understand what an attacker can do to OT and IoT devices if these vulnerabilities are exploited.
Dave Bittner: Well, let's jump right in. What are some of the highlights with some of the vulnerabilities that you all found?
Roya Gordon: OK, so in our blog, you know, we do specify the different firmware versions that are vulnerable. So that's key. We don't want to say, like all of these devices and all of these expansion cards are vulnerable but definitely mostly the version 1.10.0. Now, one of the first and most concerning vulnerabilities is that it allows an attacker who possibly is using brute force - so maybe they're just guessing or using a tool to kind of break into the login portal - or they can use stolen credentials. And we know there's a lot of that circulating on the dark web. But once they attempt to log in, there's a prompt that pops up asking if they want to terminate or override an ongoing session. This function does not provide any verification or checks at all. So an attacker could essentially log in and kill whatever session that's ongoing and then be able to take control of the current session and have access directly to whatever OT and IoT devices that are associated with the expansion card.
Dave Bittner: And we're talking root privileges here, right?
Roya Gordon: Yes.
Dave Bittner: Well, let's go into some of the other things you found here. What other things caught your eye?
Roya Gordon: So once they're in, an attacker can launch essentially a denial of service. So they're denying whoever else had the session open from doing anything. So it's essentially a denial of service. Another vulnerability is a buffer overflow. And that is a very common - what we called a common weakness enumeration. If you look at a whole bunch of other vulnerabilities, you usually see remote code execution, buffer overflow. And a buffer overflow is essentially when there is more data than what the block of memory can hold. So the new data values rewrites the old data values. And if an attacker is doing this, then they're embedding the new values with malicious commands. It could be to erase files, to shut things down. But essentially, they can use that as a way to push malicious commands into OT/IoT devices. And again, there's nothing that's stopping this from happening. This isn't a problem with just this vendor. This is just across the board a common weakness that is in just a lot of devices.
Dave Bittner: Now, you all have been in contact with this particular vendor, yes?
Roya Gordon: Yes.
Dave Bittner: And what's the response been?
Roya Gordon: So we work very closely with our vendors. And that's kind of why it took us a bit to publish this because once we discover these vulnerabilities, we're speaking with the vendor. They're verifying that there are vulnerabilities. Then they're working on the fix. And we can't publish these vulnerabilities without there being a fix because we'll just be telling threat actors, hey, these are vulnerable. And then they'll just go ahead and exploit. So it takes a bit of time. It takes a bit of working with the vendor. Again, that's why we're holding off on part two because there's fixes that's in the works. And once those fixes happen, then we can go ahead and release the additional vulnerabilities that we found.
Roya Gordon: But in our blog, we have links to all 13 of the vulnerabilities. They're in the National Vulnerability Database. So once you all click on the links, it takes you to the description of the vulnerability, the different CWEs that's linked to MITRE that actually shows you how you can implement workarounds to those CWEs. But yeah, we have a very good relationship with the vendor. And we also have the vendor review any of our technical content about vulnerabilities to make sure that we're on the same page. We're not seeing something that they don't agree with. So yeah, it's a very good ongoing relationship with this vendor.
Dave Bittner: And just to be clear, you outline in the research that the vendor is an organization called Lanner?
Roya Gordon: Yes.
Dave Bittner: And what is their specialty?
Roya Gordon: So they create the expansion cards for the BMCs. So...
Dave Bittner: I see.
Roya Gordon: Yeah, so that's their specialty. They're just trying to create the same kind of BMC capability and extend that out to OT and IoT devices. But it has a web interface. And in our blog, you can see the screenshots of everything. And again, you know, it's convenient because you're able to physically see what kinds of controls that you're implementing onto the OT and IoT device. But again, we just need to make sure that things like logging in is secure and, you know, the memory buffer has alerts and it has blocks and it's not going to rewrite the current data. But, you know, again, really unique and good piece of technology, and that's why our team - that's why we do what we do. We're trying to help vendors create more secure products. It's good to be technologically advanced but in a secure way. So that's kind of why our team looked into this as well. And of course, anything involving OT and IoT, any devices that are kind of bridging that gap to the internet, we look into and we work with vendors on helping them secure it.
Dave Bittner: In your research, did you uncover any incidences of this being exploited?
Roya Gordon: No. We haven't seen this exploited in the wild. Of course, you never know what's going on on the dark web, but we can't say that we know threat actors are exploiting this intentionally. But again, that's why we are rushing to make sure we publish this so that the vulnerability can be patched; it can be secured. So there is a new version out, but again, we're working with the vendor that's going to update and create another new version that's going to address the additional vulnerabilities. But no immediate threat as of now as of what we know.
Dave Bittner: So what are your recommendations here? I mean, I think, you know, there are the obvious steps if your equipment is from this provider, but is there broader advice, too, for folks who are taking advantage of this remote configuration capability with their own equipment?
Roya Gordon: Yeah. Absolutely. So again, this is really only for companies that are using this specific vendor, so we can't say that all expansion cards for BMCs are vulnerable 'cause we haven't looked into those devices. But, you know, obviously, first and foremost, get the newest version because it has addressed these vulnerabilities that we found. So we would recommend updating the expansion card. Any time we're publishing our research, we're publishing the CVE, there is a patch or there's some type of update that the vendor has done. So we definitely recommend whoever is using this Lanner expansion card with the vulnerable version number to update it to the latest.
Roya Gordon: But another tip that I usually advise is to look at all the common weakness enumerations. They're the CV - CWEs. They're the flaws that are usually associated with the vulnerability. So what are the common things that threat actors do once they've exploited a device? So when you click on the link to the different vulnerabilities, it's going to link you to NVD, and then from there you can further look at the list of CWEs. Click on those link, and when you go to Miter, it's going to tell you in detail any kind of workaround you need to do to make sure that a threat actor can't take advantage of the buffer overflow function, or they're not able to do remote code execution. There's additional small security that you can implement so that if a threat actor does exploit this, they can't even take advantage of some of those weaknesses.
Dave Bittner: Our thanks to Roya Gordon from Nozomi Networks for joining us. The research is titled "Vulnerabilities in BMC Firmware Affect OT and Iot Device Security." We'll have a link in the show notes.
Rick Howard: Arm your team with the latest news and trends in the evolving cybersecurity landscape with CyberWire Pro Enterprise. Our unlimited Pro content will allow you and your team to accelerate and sustain cybersecurity awareness and knowledge. Get access to searchable and accessible news in cybersecurity, business, policy, privacy, disinformation and more. Find out about our education and military discounts by inquiring at thecyberwire.com/pro.
Dave Bittner: The CyberWire "Research Saturday" podcast is a production of N2K Networks, proudly produced in Maryland out of the startup studios of DataTribe, where they're co-building the next generation of cybersecurity teams and technologies. This episode was produced by Liz Irvin and senior producer Jennifer Eiben. Our mixer is Elliott Peltzmann. Our executive editor is Peter Kilpe, and I'm Dave Bittner. Thanks for listening.
