New exploits are tricking Chrome.
Dave Bittner: Hello, everyone, and welcome to the CyberWire's "Research Saturday." I'm Dave Bittner, and this is our weekly conversation with researchers and analysts tracking down the threats and vulnerabilities, solving some of the hard problems of protecting ourselves in a rapidly evolving cyberspace. Thanks for joining us.
Dor Zvi: So we came across that exploit from a few samples that we found in the wild and found it was also posted on GitHub by a user named Echo.
Dave Bittner: That's Dor Zvi. He's co-founder and CEO at Red Access. The research we're discussing today is titled "New Chrome Exploit Lets Attackers Completely Disable Browser Extensions."
Dor Zvi: At first, we noticed it was published as an exploit for Chromebook devices. But then when we tested it in our lab, we found it works on other operating systems as well, such as Windows and Linux, and we found that it affects Chrome but also other Chromium-based browsers in the same way. So yeah, it's not surprising because targeting browser extensions isn't something new. But I think, like, as web browsing becomes more and more central to the average user's work life, browsers themselves are becoming increasingly attractive targets to malicious actors.
Dave Bittner: Well, let's go through this together. Can you describe to us exactly what's going on here?
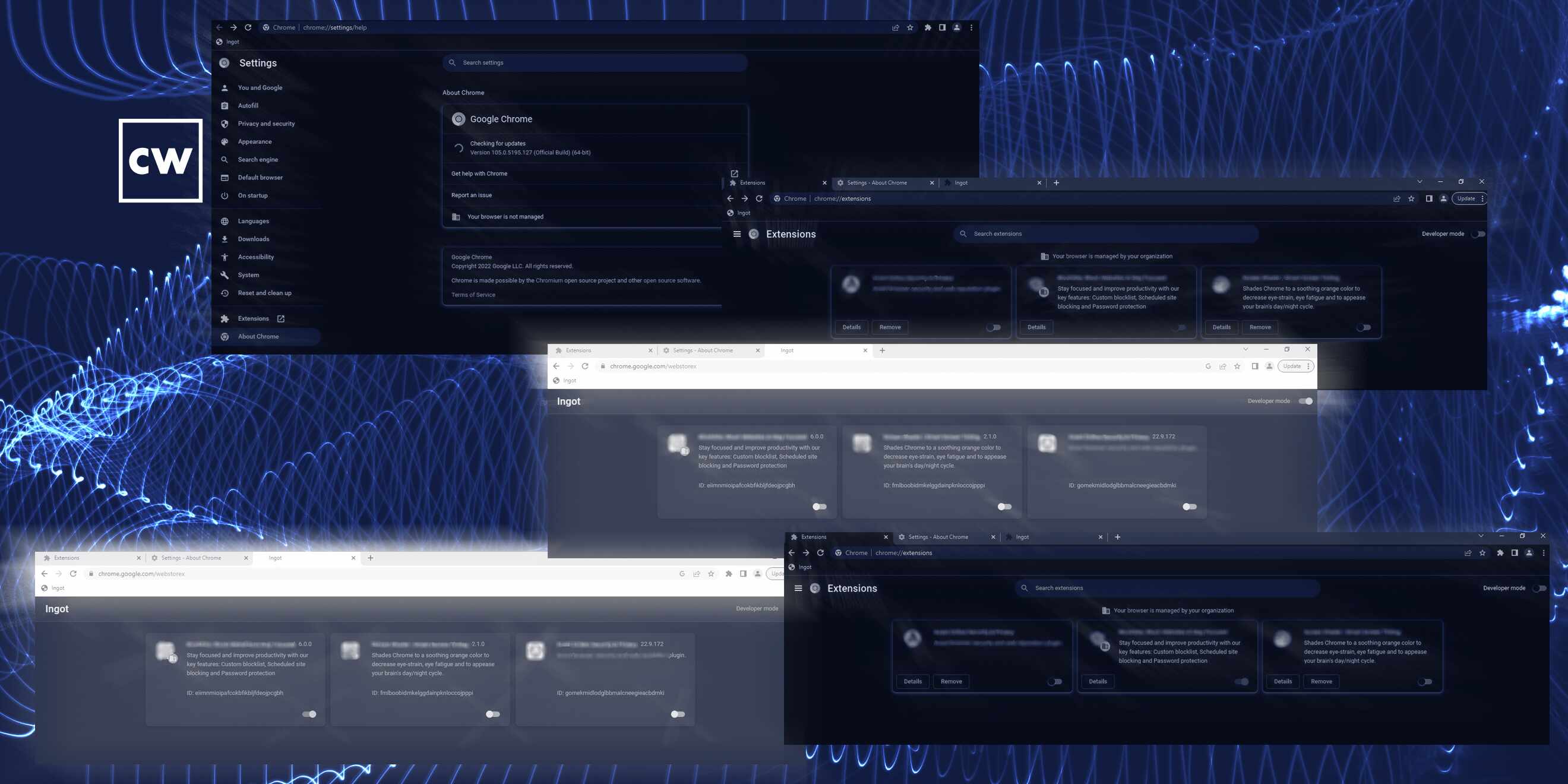
Dor Zvi: Yeah. So the LTBEEF - that's short for literally the best exploit ever found. Now, I wasn't responsible for the name. But that's an exploit that targets Google Chrome and affects Chromium-based browsers as well. It allows attackers to selectively force-disable browser extensions. That exploit consists of a bookmarklet exploit that allows attackers to disable any browser extension installed using a simple, handy user interface that issues commands that Chrome mistakenly identifies as legitimate requests.
Dave Bittner: Well, walk me through exactly how an attacker would go about doing this.
Dor Zvi: All right. So it is actually triggered by JavaScript in URL. And the powerful thing about it is that it even overrides any security policy group configured on the device. So even if a user doesn't have any privileges to disable browser extensions, this exploit overrides and disables them. And the funny thing is that if there is a security policy group, then the user will not be able to turn them back on. I think that, like, many companies and personal users are using some browser extensions to block ads, to manage their data or even as a browser-level antivirus. Now, the ease with which this weakness simply turns them off, that's what's scary here. So regarding for your question, I think, like, there are multiple ways an attacker can use to trigger that exploit - basically, just to get a user to visit a URL with that JavaScript, whether it's using phishing or via a file containing a link or via ads or any other way, especially when this JavaScript code looks legitimate. And that's what makes that exploit so easy to use. So we've seen many attacks that require user interaction, and this is - this one is another classic example of it.
Dave Bittner: Does this require any user interaction? Other than visiting that URL, does the user have to do anything, or are there any alerts that they would see?
Dor Zvi: Yes, it is. It requires the user to save a bookmark, which - inside that bookmark URL, there will be a JavaScript code.
Dave Bittner: And so then when the user visits that bookmark, that's what executes the code?
Dor Zvi: Exactly.
Dave Bittner: So when that code is executing, is there anything visible to the user? Do they - are there any screens that pop up, or are they in any way aware of what's going on here?
Dor Zvi: No, no. That's completely seamless. And I think, like, turning browser extensions off, it can affect the user experience as well as the security level. So at best, the attacker will disable ad-blocking extension, and you will notice that. But in the same way, it can be an extension that organizations use for browser protection. And in such a case, the attacker may turn off scanning mechanisms and then easily attack and remain under the radar. So you will not notice any change.
Dave Bittner: Does the attacker have any visibility into the user's environment? Are they able to select which extensions they're able to disable, or is it an all-or-nothing kind of thing?
Dor Zvi: So yeah, they basically see all installed extensions, and they can selectively force-disable the one that they want to disable. It can be all of them, but it can be a specific one that they chose.
Dave Bittner: Wow. And would an administrator have any notice that this had taken place?
Dor Zvi: It can be. It depends on how they manage their browser extensions. But usually there is no alerting system on such solutions or extensions. So it can be both.
Dave Bittner: I see. Now, have you all come across examples of this being used in the wild?
Dor Zvi: Yes, we did. We did. It was kind of a social attack page that triggers you - try to trick you to save bookmark of that specific website. They use Amazon gift card image or free iPhone message that once you click and save it bookmark, you should receive something. But that's, I think, the social side of it. And once you saved it, that's it.
Dave Bittner: And what do you suppose they're after here? I mean, disabling extensions in someone's Chrome browser - are they looking to, you know, disable antivirus in the browser? What do you think they're after here?
Dor Zvi: Right. So that's basically just a type of technique to go under the radar and avoid the security. So it can be used in the personal market to run ads or just a kind of social attack. And it can also be a first stage of a more sophisticated attack on a big company that - being used to disable their security. So there is no specific type of attacker that will use that. It's more the technique of how can we go under the radar and avoid in-browser security?
Dave Bittner: And you and your colleagues, in this report, you point out that we're seeing more and more attention to browser extensions from some of these bad guys.
Dor Zvi: Yes. I think that browsing today is at the core of the hybrid work, and as such, it has become a main target for attackers. We see, like, browsers are frequently updated by their providers to fix vulnerabilities and zero-days that have been discovered. However, browsing is far from being the only risky application in the browsing space. There are many web-based desktop applications that we use on a daily basis for work, such as file-sharing applications, video conferencing, chat or cloud applications that contain browsing risks that are not browser-based. So the data that we share, the files we download, the links we click on, they all can contain risks related to browsing, and that's where attackers are taking advantage and targeting browsing applications.
Dave Bittner: Has this been patched yet? Has - or has Chrome been patched to prevent this now?
Dor Zvi: Yes. It is patched on Version 106. And yeah, Google patched it.
Dave Bittner: And so if I'm running, you know, another Chromium-based browser, odds are, if I'm keeping up to date, I'll be safe there as well.
Dor Zvi: Yes.
Dave Bittner: So what are your recommendations, then, in terms of people protecting themselves against this sort of thing?
Dor Zvi: So I think this brings us to the central issue and critical consideration of deciding on which cybersecurity solutions to invest in. I think that the case here is a solution that operates on the same layer it's meant to protect, and that can lead to a security issue. So rather than operating as a separate, superior security layer, these extensions here rely upon the integrity of the very thing they are meant to protect, which is the browser itself. So I recommend using security solutions that operate on a separate, fully independent layer that will not be affected by exploits or vulnerabilities within the environment they are meant to secure.
Dave Bittner: Our thanks to Dor Zvi from Red Access for joining us. The research is titled "New Chrome Exploit Lets Attackers Completely Disable Browser Extensions." We'll have a link in the show notes.
Dave Bittner: The CyberWire "Research Saturday" podcast is a production of N2K Networks, proudly produced in Maryland out of the startup studios of DataTribe, where they're co-building the next generation of cybersecurity teams and technologies. This episode was produced by Liz Irvin and senior producer Jennifer Eiben. Our mixer is Elliott Peltzman. Our executive editor is Peter Kilpe. And I'm Dave Bittner. Thanks for listening.
