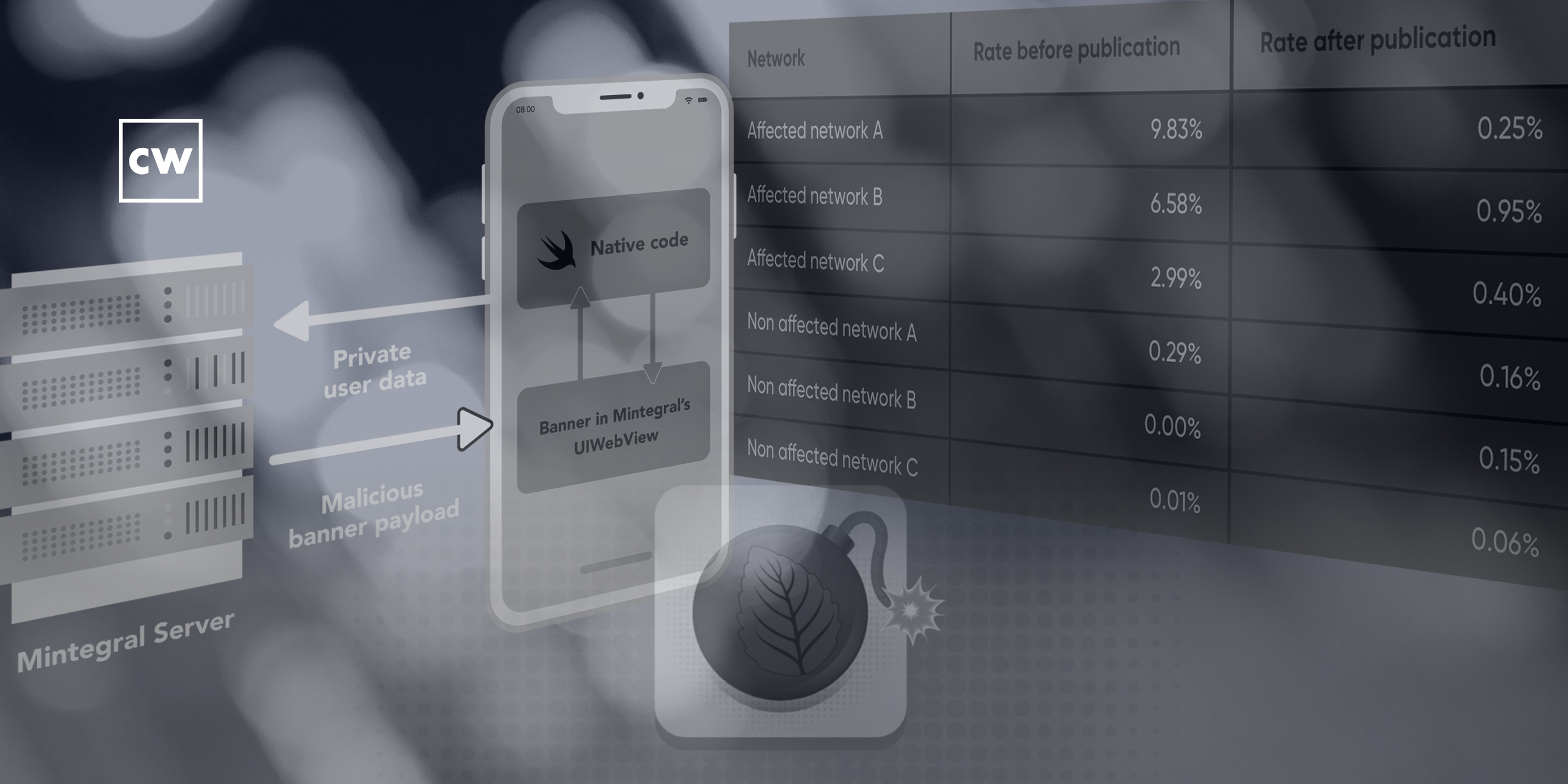
Advertising Software Development Kit (SDK): serving up more than just in-app ads and logging sensitive data.
On August 24, 2020, Snyk announced the discovery of suspicious behaviors in the iOS version of a popular advertising SDK known as Mintegral. At that time, they had confirmed with partners in the advertising attribution space that at minimum, Mintegral appeared to be using this functionality to gather large amounts of data and commit ad attribution fraud. Their research showed that Mintegral was using code obfuscation and method swizzling to modify the functionality of base iOS SDK methods without the application owner’s knowledge. Further, their research proved that Mintegral was logging all HTTP requests including its headers which could even contain authorization tokens or other sensitive data.
Since that time Mintegral announced that they were opening the source of their SDK to the market. While the SDK can only be downloaded by registered partners, a major game publisher shared the source code with Snyk for further analysis. They also continued their research by digging deeper into the Android versions of the SDK in which they hadn’t found similar behaviors at the time of the initial disclosure.
This has resulted in some significant discoveries that necessitate an update to the previous disclosure. Additionally, Mintegral and the community at large have responded to the situation, and Snyk felt a summary of the events was a good way to finalize their research into this SDK.
Joining us on Research Saturday to discuss their research is Snyk's Alyssa Miller.
The original blog and Snyk's update can be found here:



