Exhibiting advanced APT-like behavior.
Dave Bittner: Hello everyone, and welcome to the CyberWire's Research Saturday. I'm Dave Bittner, and this is our weekly conversation with researchers and analysts tracking down threats and vulnerabilities, solving some of the hard problems of protecting ourselves in a rapidly evolving cyberspace. Thanks for joining us.
Yonatan Striem-Amit: They were deploying pretty advanced APT-like behavior to perform lateral movement, to extract credentials, to move laterally across the endpoints, and really behave as though they were in the know-how of the way that these advanced APT groups work.
Dave Bittner: That's Yonatan Striem-Amit. He's Chief Technology Officer and co-founder at Cybereason. The research we're discussing today is titled, "Prometei Botnet Exploiting Microsoft Exchange Vulnerabilities."
Yonatan Striem-Amit: It's "Prometei" – it's kind of the Russian word for Prometheus...
Dave Bittner: OK.
Yonatan Striem-Amit: ...Which is selected from the internal name found inside the malware. So it's pretty clear the author has actually internally called the project "Prometei."
Dave Bittner: Gotcha. All right. Well, let's start off with some high-level stuff here. I mean, what originally drew this to your attention? How did you get started down this path?
Yonatan Striem-Amit: So naturally, when Hafnium broke out, we were constantly tracking what is going on, who's exploiting this across the world? We've encountered that post the initial exploitation by the Hafnium group, which is considered to be a Chinese group, we've seen secondary attackers adpting very, very quickly and using either the same vulnerability and re-exploiting that, or just exploiting the actual backdoor deployed by the Hafnium group. As we're seeing this application, naturally in our commitment to protect our customers, we have Cybereason are tracking constantly to understand what is happening.
Yonatan Striem-Amit: This led us to discover the Prometei malware being used on these machines. Interestingly, while Prometei used – the group behind Prometei used the Microsoft Exchange Server vulnerability to enter the company, once they were inside, they were deploying pretty advanced APT-like behavior to perform lateral movement, to extract credentials, to move laterally across the endpoints, and really behave as though they were in the know-how of the way that advanced APT groups work
Dave Bittner: Well, describe to us what they're up to here. What is the ultimate goal?
Yonatan Striem-Amit: The reason we think it's a financially motivated group is clearly we're seeing that their activity is about deploying solutions that steal money, that are aimed to use the resources of the victims to mine for Bitcoin, mine for Monero, and use those stolen resources for financial gains. Unlike espionage groups who are often about stealth and exfiltration of data, the Prometei group was using the resources to mine for cryptocurrency, and that was their way of monetizing it.
Dave Bittner: I see.
Yonatan Striem-Amit: Now I find it very, very interesting the way they choose their victims. We at Cybereason have been tracking victim selection of that group, and we're seeing it's really about a very wide – we're seeing victims across the US, across the UK, other European countries, even all the way through South America and East Asia with an explicit attempt to avoid the Eastern Bloc and former Soviet countries and definitely Russia. That's what led us also to think of that as the likely source of their operation. We're not saying that they are, of course, Russian state-sponsored, but we are saying they're likely active from that area.
Yonatan Striem-Amit: And within those countries, they again go very widely. They go after finance, insurance, retail, manufacturing, utilities, travel, construction, really everything will be a victim for them. I find it very curious in the context of the Colonial Pipeline attack, how it really is a very wide net with potential to cause dramatic damages. And while Prometei's method of extracting financial gain is by mining cryptocurrency, it may very easily be sold off to secondary markets, to other groups, or the same group using that to deploy ransom and hold the victims for ransom.
Dave Bittner: Interesting. So, I mean, does it seem to you that as though it's more opportunistic than precisely targeted? For cryptocurrency mining, processing power is processing power?
Yonatan Striem-Amit: Precisely. Their purpose in cybercrime is always the story about how do you get money out of the story here? And while most of the attention these days is going to extracting money by employing ransom for the currency to extract money, hackers are clearly also using mining for cryptocurrency as another way of extracting revenue from their ability to attack. In the case of the Prometei group, they are really going as widely as possible. And in order to avoid actually paying for the computing resources, they just go and steal them from the victims.
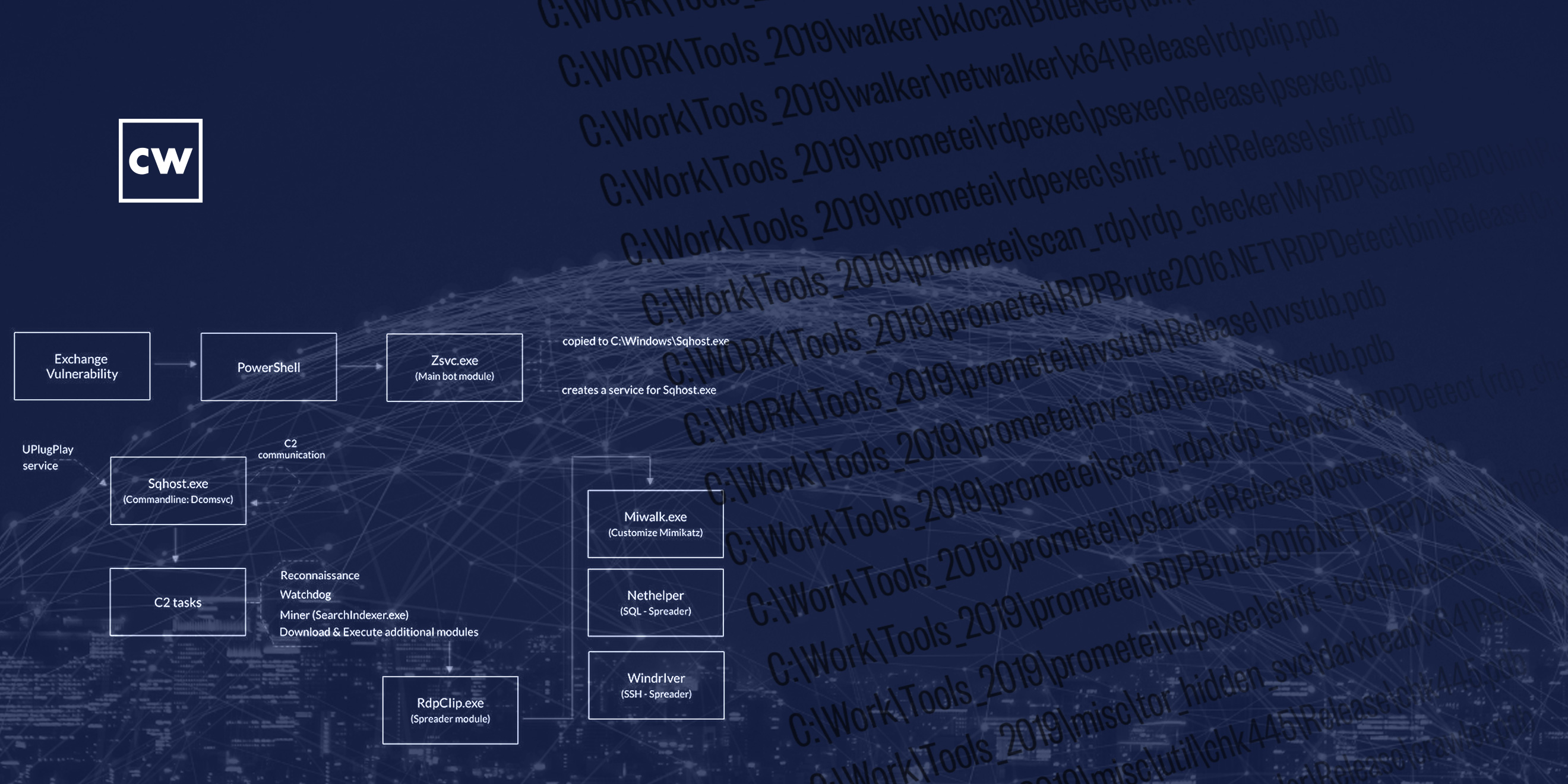
Yonatan Striem-Amit: Now, naturally, the victims here are – it's not just about the Exchange Servers – in order to get the maximum compute capabilities out of the victims, what they're doing is post-entry really migrating and trying to take over as big as possible from the environment in order to turn those into mining rigs for the hackers' behind Prometei. And these methods of lateral movement, this method of asset acquisition, are really reminding us of the tricks and the technologies deployed by nation-state-level groups, whether it's the groups behind SolarWinds or the actual group behind Hafnium or other similar such attacks, everything from using exploitation, everything from those that are infamously leaked from the NSA a couple of years ago, EternalBlue, using BlueKeep, harvesting credentials, exploiting Remote Desktop, SMB, and even stealing a SSH clients and spreading via an SQL server. Another thing that we at Cybereason saw that this group were doing extensively is using a malware can self-adjust to run both on Windows and Linux machines. So, while they enter on the Windows server, they can easily move laterally over into a Linux-based attack, and when you have more Linux-based servers in your environment, again with the purpose of stealing compute power at this point to mine for cryptocurrency.
Dave Bittner: Hmm. Well, let's walk through it together. I mean, how does one find themselves falling victim to this? How do they get in and what do they do from there?
Yonatan Striem-Amit: Excellent. We've observed the Prometei group entering through the Microsoft Exchange Server vulnerability. This vulnerability has been in use a lot recently, being exploited with the Hafnium group, which is the Chinese – a Chinese-originated attack. But in the wake of the Hafnium attack, many other cybercriminals went and adopted that same exploit or actually even using the backdoors deployed by the Hafnium group and used that to enter the organization. Once they're inside and have that control over the Exchange Server, they perform tricks around lateral movement, basically having – transitioning the access they have on one asset to complete control over multiple assets
Yonatan Striem-Amit: This is done by a very large array of weaponry that they've brought together. It starts with exploitation. If you have unpatched systems, the Prometei group will use that to move and take over those machines. So, they were using everything from SMB-based attacks with EternalBlue to BlueKeep, and other similar ideas. Secondly, they were using credential harvesting. If anybody ever logged into that Exchange Server, it would have left residue behind on credentials of the person that was used to log in there. For example, the admin that's trying to manage that server. So they'd – by using that credential, they can move to other machines that that same admin has access to.
Yonatan Striem-Amit: They further deploy – use things like Remote Desktop, that we use command of servers and machines, and use that as a communication channels, or SMB, which is a very commonly deployed file-sharing protocol, was also used in the environment. And additionally – and this is pretty interesting – they also used simply SSH. So if you have a server that you can manage with those credentials, they will actually SSH into that server and deploy their malware. So they're very active in trying to get as many of the compute resources of the victim has and subvert them for their cryptomining purposes.
Dave Bittner: To what degree are they trying to be stealthy? Are they trying to hide their tracks? Do they put any limits on the amount of compute power that they take? Do they limit the time of day, for example? Do they have those options built into their software?
Yonatan Striem-Amit: While they have complete control over the software, we haven't seen them try to be extremely evasive. They really are trying to say, how can exploit the most resources that you have right now before we end up getting caught? A lot of time these attacks, once they start seeing that their assets are being taken down, would quickly transform the attack from a cryptomining to something else that is much more – takes a shorter amount of time, for example, such as ransomware. So we will end up seeing – in these similar cases we would end up seeing, once the takedown is starting, this is quickly turning into a ransomware case.
Yonatan Striem-Amit: Another interesting thing they did for resilience, they've actually built a pretty robust command-and-control channel over the Internet. By using servers all over the world and making servers that they can control the malware with, it allows them to really be more resilient, even if some of those servers are discovered and they're taken down or blocked by network security providers, they still have a pretty resilient control mechanism.
Dave Bittner: Now, they go in and they look for other cryptominers and remove them?
Yonatan Striem-Amit: So, that's something interesting they did. They actually, when they log in, especially on Hafnium servers, they actually remove existing backdoors if any is found, and also tried to block the exploitation of the initial vulnerability. Basically, they come in, they kick out from that Exchange Server other adversaries that may have used a similar solution to get there and can get control of that device, and then lock it so that only they have access to it. That's a pretty interesting technique that they use here, effectively taking over the servers and making sure that nobody else can easily from the outside share the resources with them.
Dave Bittner: Now, this was discovered in 2020, but you all have some evidence that it's been running for a good bit longer than that.
Yonatan Striem-Amit: Indeed. We're seeing traces of some of the pieces of the malware all the way back to 2016. And while they didn't seem to be very, very active ahead of time, we do see evidence of development of the malware, the work on this strategy, has been something they've been doing for a while – for at least four years. And we are seeing rapid evolution. There's definitely active R&D work in the Prometei group being driven into the malware, getting more capabilities, bringing more APT-like technologies and ideas into the malware to further derive revenue from them.
Dave Bittner: And what can you determine about the threat actors themselves?
Yonatan Striem-Amit: So there's many reasons to believe that they are originated in Russia. Everything from the way they choose targets, and they specifically avoid targets that are in the former Soviet bloc countries – Russia and it's kind of surrounding, immediate neighbors. They also have a couple of words that they use a Russian-based toning, and even the the name "Prometei" was found inside the malware. And this is, of course, the Russian pronunciation for the Prometheus from Greek mythology.
Dave Bittner: Hmm. You know, one of the things that strikes me reading through your research here is the sophistication in the way that there's a lot going on here. This is a bit of a, I don't know, a Swiss Army knife of tools. Once they get inside, they have a lot of options to do the things they need to do.
Yonatan Striem-Amit: Absolutely. Once they get inside, they really have complete control over that machine and they very quickly use that complete control to gain as wide as possible net of control around the entire enterprise, the victim's network environment. So, as many machines, as many servers, as many endpoints they can get their hands on, they will take those for their purposes. Tricks they're using definitely are reminiscent and demonstrate techniques and operation that are used by APT groups. So it's clear to us that there is at least knowledge transfer and a lot of learning happening in the Prometei group for what is being done in a nation-state-funded cybercrime. This is definitely interesting in the way they operate.
Yonatan Striem-Amit: They show sophistication in everything, first from the speed in which they adapted to the Microsoft Exchange vulnerability and adapted that for the use of penetration, all the way through just the Swiss Army knife of technologies that they use to move laterally and get more assets. This is one of the very first cases where we're seeing the group able to seamlessly traverse and create malware for both Windows and Linux to get control of these two very different operating systems and still subvert them to their will. And as many of those cases, the technology they have themselves really gets the flexibility to deploy any payload, any malware they wish. A lot of times this is eventually being used to sell off the assets for post-exploitation, for things like ransomware delivery. It's very common that we would see these groups mining for cryptocurrency for a while – this is the way they choose to monetize – and eventually when they realize that the value of the assets for them is diminished, they would sell it off to other groups in the program, or of course, they themselves, to further extract revenue from those victims.
Dave Bittner: How successful do you sense that they are? I mean, do you have the ability to know to what degree they've been able to spread this around?
Yonatan Striem-Amit: So, we've seen them attacking dozens, at least, of victims, and that's a sign of how prolific they are right now. I would say they're definitely active, and I think the choice of doing that for extracting revenue from cryptocurrency mining also shows us that the more active they are, it's very, very clear how much more revenue they get. They have a clear incentive to go and be very active in order to extract more and more financial gain.
Dave Bittner: And what are your recommendations for organizations to best defend themselves against this group?
Yonatan Striem-Amit: That's a great question. The first and foremost answer is vigilance. Continuous patching is, of course, always a good idea. And then really invest in a good, robust, threat hunting program. We at Cybereason, of course, do that for our customers and really find threats wherever they're happening. So the combination of cybersecurity hygiene and vigilance, and an active threat hunting and response program are the keys to solving this threat, as well as any other threats, from nation-states to cybercriminals.
Dave Bittner: Yeah, I guess it's – I mean, this is really emphasizes that point that you really need to have, I guess, that defense-in-depth. You know, it's not enough to have to have those castle walls up around. You have to be looking for what's going on within your network.
Yonatan Striem-Amit: Absolutely. That's a great observation here. The entry into the Microsoft Exchange Server did use a vulnerability, but a lot of what they did afterwards was just exploiting legitimate credentials left on those servers to move laterally across assets. So just an anti-exploit solution, without a threat hunting component, is really limited here. The answer is really had been that vigilance, a threat hunting program, an EDR solution, can solve you both against ransomware as well as more advanced crimes, and stopping threats as early as possible before the damage is done, before they move laterally across your environment.
Dave Bittner: Our thanks to Yonatan Striem-Amit from Cybereason for joining us. The research is titled, "Prometei Botnet Exploiting Microsoft Exchange Vulnerabilities." We'll have a link in the show, notes.
Dave Bittner: The CyberWire Research Saturday is proudly produced in Maryland out of the startup studios of DataTribe, where they're co-building the next generation of cybersecurity teams and technologies. Our amazing CyberWire team is Elliott Peltzman, Puru Prakash, Kelsea Bond, Tim Nodar, Joe Carrigan, Carole Theriault, Ben Yelin, Nick Veliky, Gina Johnson, Bennett Moe, Chris Russell, John Petrik, Jennifer Eiben, Rick Howard, Peter Kilpe, and I'm Dave Bittner. Thanks for listening.


