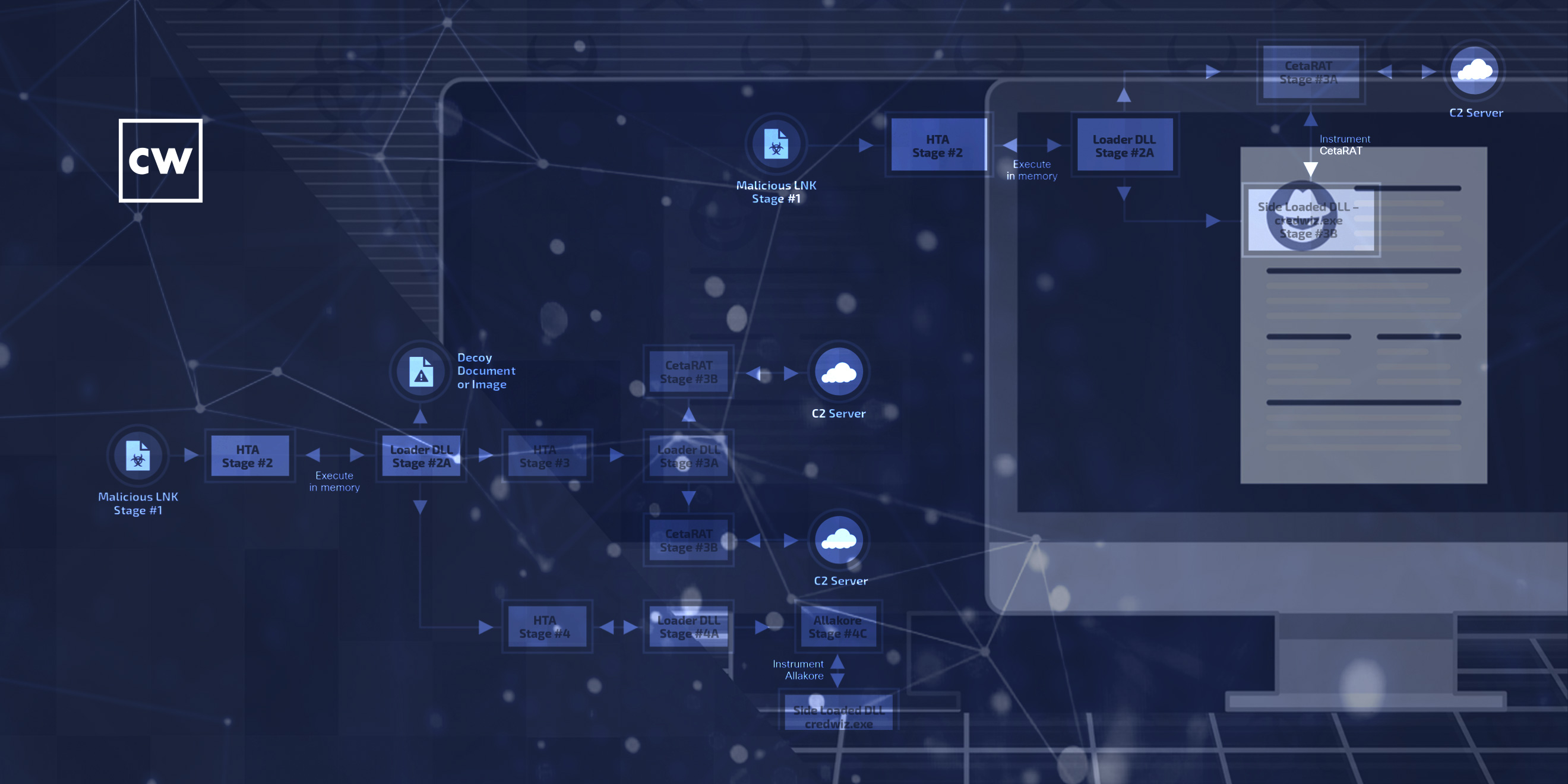
SideCopy malware campaigns expand and evolve.
Guest Asheer Malhotra, Threat Researcher of Cisco Talos Intelligence Group, joins Dave to discuss his team's research "InSideCopy: How this APT continues to evolve its arsenal." Cisco Talos has observed an expansion in the activity of SideCopy malware campaigns, targeting entities in India. In the past, the attackers have used malicious LNK files and documents to distribute their staple C#-based RAT. We are calling this malware "CetaRAT." SideCopy also relies heavily on the use of Allakore RAT, a publicly available Delphi-based RAT.
Recent activity from the group, however, signals a boost in their development operations. Talos has discovered multiple new RAT families and plugins currently used in SideCopy infection chains.
Targeting tactics and themes observed in SideCopy campaigns indicate a high degree of similarity to the Transparent Tribe APT (aka APT36) also targeting India. These include using decoys posing as operational documents belonging to the military and think tanks and honeytrap-based infections.
The research can be found here:



