SideCopy malware campaigns expand and evolve.
Dave Bittner: Hello everyone, and welcome to the CyberWire's Research Saturday. I'm Dave Bittner, and this is our weekly conversation with researchers and analysts tracking down threats and vulnerabilities, solving some of the hard problems of protecting ourselves in a rapidly evolving cyberspace. Thanks for joining us.
Asheer Malhotra: So, as part of our proactive hunting processes, we usually keep tabs on the different types of malicious files that we see out in the field, you know, in our telemetry, out on our public repositories. And that's how we got the initial lead for this specific APT and the specific infection chains and the related matter
Dave Bittner: That's Asheer Malhotra from Cisco Talos. The research we're discussing today is titled, "InSideCopy: How this APT continues to evolve its arsenal."
Dave Bittner: Well, let's dig into some of the details here. Can we start off with just an overview of exactly what it is we're talking about here and the types of things that they do
Asheer Malhotra: Sure. So, our research focuses on a group called SideCopy. This is a group that focuses primarily on the Indian subcontinent with a very heavy focus on India and Afghanistan, and a little bit of focus on Pakistan as well. This is a group that primarily targets government entities, specifically military personnel and diplomatic personnel. And then we've seen a few civil servants, you know, traditional government employees being targeted as well. This group tries to carry out espionage using a variety of different malware and accompanying plugins as well. And that's what this whole white paper is all about. That's what our whole research is all about. We basically care about the entire arsenal of this group and we talk about it and we present it
Dave Bittner: Well, let's walk through it together and maybe let's go through from start to finish here. I mean, let's say I'm one of those folks that they're trying to target. How would I find myself initially compromised?
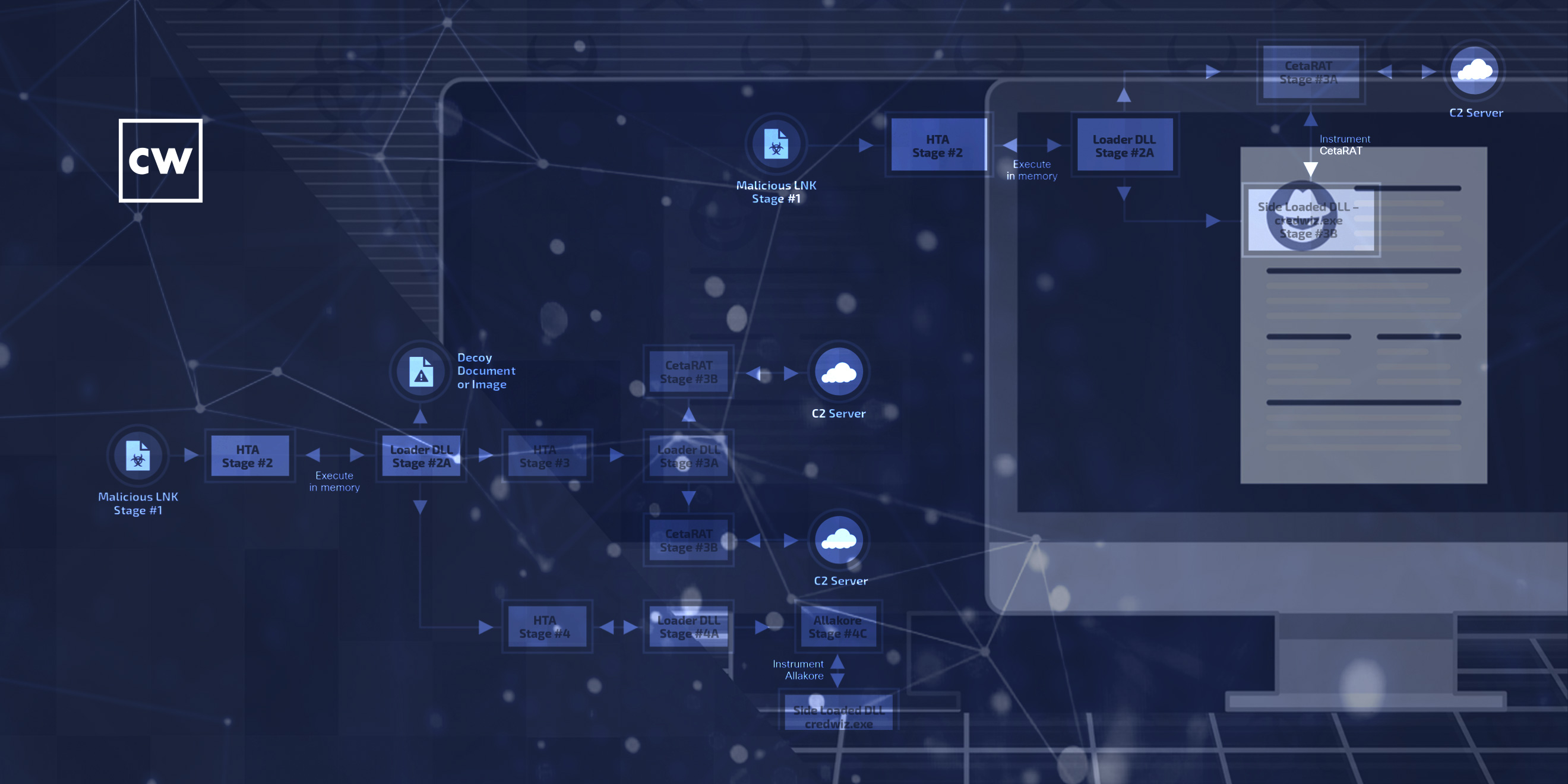
Asheer Malhotra: So, usually you'll get an email in your inbox, which contains a malicious Windows LNK – a malicious LNK file or a malicious shortcut, or you will get a link to the actual malicious shortcut file, and they're basically trying to social engineer you into opening that specific file. Once you open up that file, you know, what follows is a very convoluted chain of infection consisting of different types of HTA files, different types of loader DLLs, ultimately resulting in remote access Trojan, which is a RAT, being deployed on your computer or on your system, on your endpoint. And that's the whole infection process as a whole. They put a lot of effort into social engineering because, you know, they have to entice users into opening up their malicious files, which is why we've seen different types of themes that are related to military and diplomatic – you know, something that piques your interest and tricks you into infecting yourself.
Dave Bittner: So, we feel as though they're being fairly successful on the social-engineering end of things
Asheer Malhotra: Yeah, they use a variety of themes. So, basically the way this infection works is that when you when you open up a malicious shortcut file during the infection process, they display a decoy document to you, or a decoy picture to you. And that document usually pertains to a military topic or a diplomatic topic. And that's how we feel that they're targeting specific personnel in, you know, the military and the diplomatic community as well in certain geographies.
Dave Bittner: So, meanwhile, behind the scenes, while this RAT is being deployed, what's going on there? How are they able to allow that to get its purchase on your system?
Asheer Malhotra: Oh, yeah. So, it starts with the with the malicious shortcut file. And the malicious shortcut file basically goes out and downloads something called an HTA file. It's an HTML application. This is kind of like an HTML file, but it can be opened using a native Windows application that is not a Web browser. And they can use that malicious HTA file, which can contain different types of scripts, you know, subscripts in them, like JavaScript or VBScript. And these files are hosted on an attacker-controlled website or an attacker-controlled IP address. And that HTA file is what contains the actual payload, which is in turn, you know, deobfuscated and then deployed onto the victim's endpoint.
Dave Bittner: So, can you take us through the spectrum of different RATs that they have available to them, the various things they're looking to install, and the capabilities there
Asheer Malhotra: Right. So, primarily they rely on two types of RAT families, which are two RAT families. The first one is CetaRAT and the second one is Allakore RAT. CetaRAT is a custom RAT that they've built in-house. They use the C# programming language and it's basically a .NET-based RAT family. The second right that they use is called Allakore. It's a commodity RAT. It's been available out in the wild – the source code for it has been available out in the wild for quite some time now. This is a Delphi-based RAT family, and we've seen that CetaRAT and Allakore RAT have increasingly been deployed by these threat actors since their discovery in 2019.
Asheer Malhotra: Other than these two primary RAT families, we've also found four new custom RAT families. We found DetaRAT, which is, you know, another C#-based custom RAT family. We named it DetaRAT, because, you know, I'm very bad at naming RATs.
Dave Bittner: (Laughs
Asheer Malhotra: Then we found ReverseRAT, we found MargulasRAT, and then we found another one that's called ActionRAT. So, ActionRAT is a RAT family that is also Delphi-based and it's also C#-based. There's two versions that they've been doing. If you just take a preliminary glance at it, it looks like Allakore RAT, but it's really not Allakore RAT. It's completely different. And this is a new RAT family that we found being used by the attackers.
Asheer Malhotra: Other than the four custom RAT families, we also found three new commodity RATS being used by the attackers. One is called Lilith, one is called Epicenter RAT. Both of these RAT families are not very popular, but they've been available out in the wild for a long time. These are commodity RATs, the source code is available online. And, you know, attackers usually use commodity RATs to throw off attribution, so that they don't have to develop stuff in-house. That's one. The other is that, you know, attribution becomes difficult because these RAT families, commodity RAT families are used by crimeware syndicates and also by APT groups.
Asheer Malhotra: The third commodity RAT family that we discovered was njRAT. And they've heavily started using this since the beginning of this year, since January 2021. And njRAT family – it's a very popular RAT family. You know, there's a number of APT groups, there's a number of crimeware groups that have used njRAT over the years since it became available out in the wild.
Asheer Malhotra: So, yeah, that's basically two primary RAT families, followed by four custom RAT families, and three commodity RAT families. Other than that, we also know that come during the post-infection phase – you know, once they've deployed these RATs and they've established a foothold on the system – they will then start deploying plugins, which are independent, dedicated malware components that run mutually exclusive of each other on the system to serve specific purposes. For example, we found different types of file managers and file utilities that can be used to enumerate files and download files and exfiltrate files.
Asheer Malhotra: We found different types of credential stealers that steal credentials from different kinds of Web browsers – you know, Firefox, Chromium-based Web browsers, Internet Explorer, et cetera. We also found a peculiar plugin which is Golang-based. It's basically used for file enumeration, but it's also used to steal specific types of database files that belong to a multifactor authentication application that is developed and operated by the government of India. And this is interesting because they have a very heavy focus on stealing credentials. So these attackers basically try to, you know, get database files that lets them access restricted networks, or let them access restricted email boxes, or lets them get into VPNs by using authentication. That's one side of the coin here.
Asheer Malhotra: On the other hand, we've also seen the attackers set of fake login pages for the government of India's web mail. Basically, this is a page that masquerades as a legitimate login portal for your email via the Web browser. And you enter your user ID and your password and you basically end up divulging them, these credentials to the attackers. Based on their heavy focus on the credential stealing and the heavy focus on the RATs, they wanted access to restricted networks and restricted resources. And they want to establish that foothold. They want to maintain persistent access into these networks and into these resources, which is basically, you know, your typical espionage over the wire
Dave Bittner: Do you have any sense for how precise they're being? In other words, are they targeting a specific RAT and a specific set of plugins to specific people in specific positions?
Asheer Malhotra: So, primarily they target military personnel and diplomatic entities. There are a few RATs that we haven't seen being deployed yet, but we've discovered that, you know, there is a definitive link between SideCopy and the RATs that we've disclosed in our research. Other than that, it depends on the situation. Like, the RATs are used to do preliminary reconnaissance, figure out whether the target is of value to them so that they can in turn deploy more RATs and more plugins onto that endpoint and establish, you know, a more permanent foothold on the victim's computer and on their restricted networks.
Dave Bittner: How noisy is this if someone, for example, has endpoint protection running on their system? Is it likely that it's going to be flagged here
Asheer Malhotra: Yes. So, this will be flagged and detected, provided that you have you know, you have proper cyber hygiene. You restrict different types of file parts and you restrict different types of file behaviors and you detect different types of file behaviors. Don't click or don't open files that you're not sure about, which is like security 101. If you're suspicious of something, don't open that. But then yet again, you know, people do open stuff. People, you know, we are all curious animals. So people do end up getting infected. So, coupled with the right threat intelligence, however, like the one we provide, you know, you can you can easily block this RAT if you follow proper guidelines of security
Dave Bittner: And suppose someone has been infected with it, are there methods by which they try to maintain persistence
Asheer Malhotra: It's primarily the RATs. The reason why they use a variety of RATs is probably because, you know, they want to go undetected. And even if one of their families is detected and disclosed, they can still rely on the other ones, which is why they have this huge sort of arsenal that they can deploy when they need.
Dave Bittner: And do we have any notion who's behind this
Asheer Malhotra: We know that these guys are, you know, they primarily focus on the Indian subcontinent. In terms of tactics, there is a very close resemblance to another APT group that's called Transparent Tribe. The code name is also a APT36 or Mythic Leopard. This is another APT group that doesn't use the same infection chain. They have their own set of malware, completely different set of malware. But the tactics that they use, both of these groups are very similar. They target the same geographies. They use the same kind of lures. They use the same kind of malicious documents and the same kind of themes that both of these groups use. All we can say right now is that, you know, they have a very heavy focus on the Indian subcontinent.
Dave Bittner: Now, in terms of the various RATs that they're deploying here, would a victim find themselves typically infected with a single RAT or would they throw more than one at someone?
Asheer Malhotra: Yes. So, when they started out their infection genes, they would primarily use a RAT – just one RAT family. And this was back in 2019. Since 2019, into 2020 and 2021, they have increasingly started deploying a combination of RATs. In one instance – in more than one more than one instance, we found the attackers deploy CetaRAT and Allakore RAT on the same endpoint. Then in another instance, we saw them deploy CetaRAT and ActionRAT in one instance. There were certain infection chains which were – where the attackers would deploy multiple copies of CetaRAT along with Allakore RAT on the same endpoint. You know, it's a bit of an overkill, but it shows their commitment towards infecting their victims. And it kind of shows over-engineering as well, you know, because their infection genes are highly modularized. They're all over the place. They don't need to be so modularized and they don't need to deploy so many RATs on the endpoint at the same time. But it also shows that commitment, you know, as I said, to infect their victims.
Dave Bittner: Yeah, that's interesting. So, to wrap up here, I mean, what are your recommendations then? What are the best ways for folks to protect themselves against this sort of thing
Asheer Malhotra: Right. So, I always say this with multiple infection chains and multiple RAT families. It's very important to have a layered defense model. You know, you should have protection over email. You should have protection over networks. You should have protection over, you know, the endpoint as well, et cetera, et cetera, so that, you know, you can catch and block these attacks at different stages of the infection chain, you know, so that if you miss one, you can catch them during the other. And that's what's really important. You have to block these attacks, because these are essentially, you know, government-sponsored or they're motivated by national interests. So they're highly dangerous groups that are operating very dangerous malware. They're not driven by profit, they're driven by espionage. So it's very important to have a very layered defense model so that you can protect yourself across different attacks surfaces, if I may say.
Dave Bittner: Our thanks to Asheer Malhotra for joining us. The research is titled, "InSideCopy: How this APT continues to evolve its arsenal." We'll have a link in the show notes.
Dave Bittner: The CyberWire Research Saturday is proudly produced in Maryland out of the startup studios of DataTribe, where they're co-building the next generation of cybersecurity teams and technologies. Our amazing CyberWire team is Elliott Peltzman, Puru Prakash, Justin Sabie, Tim Nodar, Joe Carrigan, Carole Theriault, Ben Yelin, Nick Veliky, Gina Johnson, Bennett Moe, Chris Russell, John Petrik, Jennifer Eiben, Rick Howard, Peter Kilpe, and I'm Dave Bittner. Thanks for listening.


