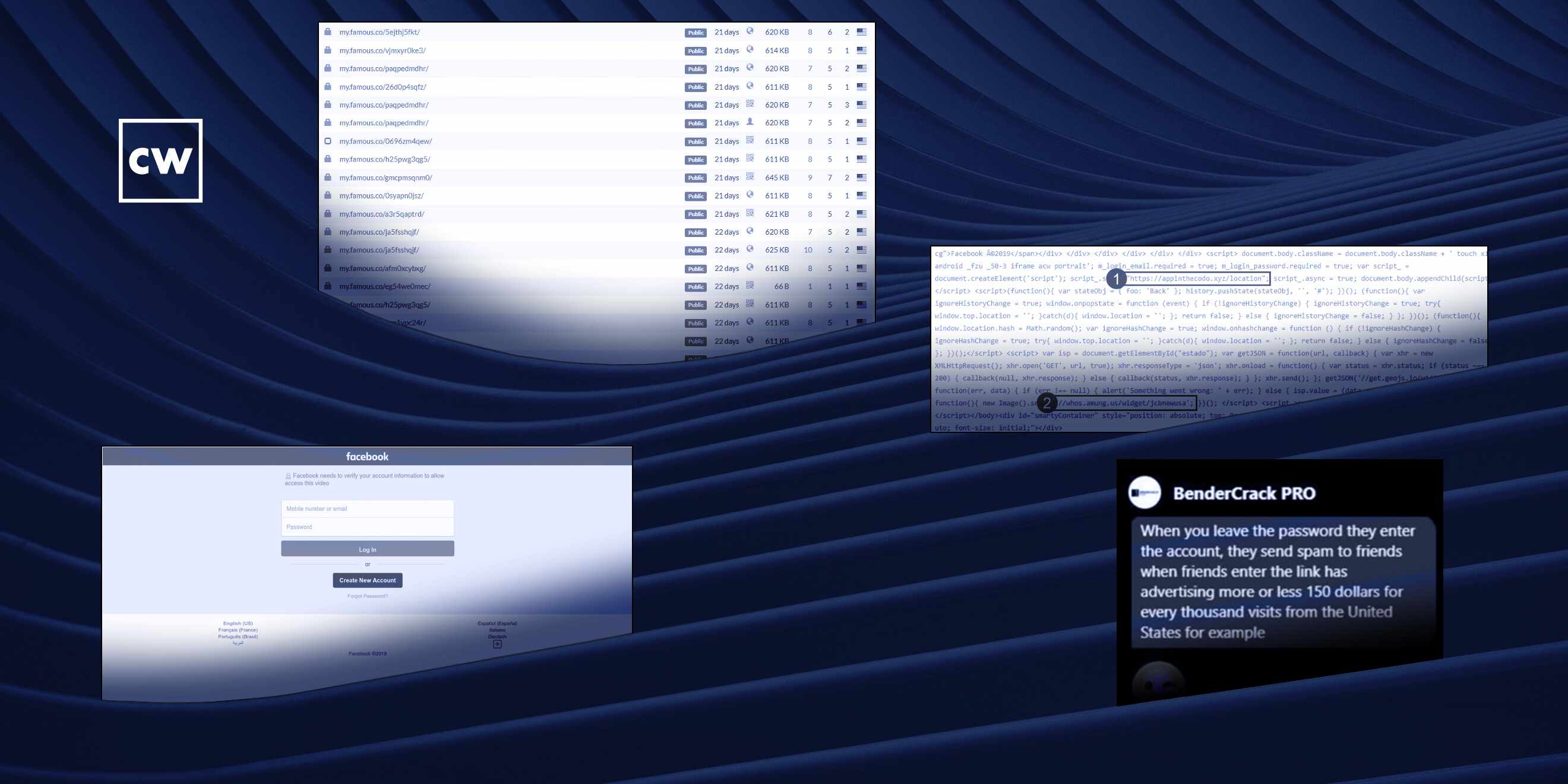
How a wide scale Facebook campaign stole 1 million credentials.
Nick Ascoli: In early 2021, we had a lot of detections in the platform for fake Facebook login portals that always had a very similar structure to them.
Dave Bittner: That's Nick Ascoli. He's a founder and threat researcher at Foretrace. The research we're discussing today is titled "Phishing Tactics: How a Threat Actor Stole 1 Million Credentials in Four Months."
Nick Ascoli: The only thing that would change between the different pages that were being - ending up in our platform were the server loading the script, the name of the server loading the script, any username associated with a stats tracking application that the adversary was using to monitor the traffic to their webpages. So we pretty quickly figured out that we were able to, without needing to authenticate to the service, use that username in the stats tracking application and view the traffic going to the webpage as well and also view the URLs they were spinning up. So originally, this came on our radar through users clicking links, phishing links, and having them report it to our platform. But we ended up being able to sort of get ahead of the adversary by being able to watch them spin up links, whether they were reported to anyone or not.
Dave Bittner: Yeah, that's interesting. I mean, the whole notion that - I suppose they were doing this for their own convenience, to be able to, you know, to track how they were doing. But, really, that set you on the path.
Nick Ascoli: Yeah. And they are still using it to this day. So the attack continues as we speak, and the same tool suites and the same code base are still in use and still seeing success on Facebook.
Dave Bittner: Well, let's walk through it together here. I mean, exactly what's going on? How would someone find themselves falling prey to this?
Nick Ascoli: So the links originate in Facebook Messenger. So the adversary will successfully harvest someone's Facebook credentials, typically through someone logging in through one of their fake Facebook login portals. They will take those credentials. And based on the speed we've observed, it's very likely automated - and well automated at this point - where when a user enters their credentials in one of their fake login portals, they will automatically log into that individual's account, that individual's Facebook account, and automatically, through Facebook Messenger, deliver whatever the latest link is in their infrastructure, whatever the latest link is that is hosting a fake Facebook login portal, and send it to all of the user's contacts in Facebook Messenger. So that takes it from one user to potentially hundreds, potentially thousands. And using the Graph protocol in Facebook's Messenger, they're able to have the individual - the target recipient's name appear in the URL. So it makes it look a little bit more convincing to the end user. And it's usually a message that is relatively obviously scammy or spammy, like you should see this video of you at the Christmas party or something with a - with their name embedded in the actual link. And then when a user clicks it, it says it takes them to a fake Facebook login page that says in order to view this video, you must log into Facebook first. So it's a relatively innocuous and, to a lay user, a pretty convincing sequence of events.
Dave Bittner: Right. It strikes me, too, that if you get a message from a friend, a Facebook friend, and it says, hey, have you seen this video, that may put you in an emotional state of not wanting to be patient - what video, what could this be? - which may get your guard down.
Nick Ascoli: Exactly. Yeah. They...
Dave Bittner: Yeah.
Nick Ascoli: ...Are intending to make it seem as urgent as possible so that when the URL loads, which sometimes - if you load it via the mobile app, which we see most users doing, they won't actually see the URL. So they won't see that it's a fake, you know, that the actual login portal is not owned by Facebook. If you're on a desktop, you'll see it in the browser. But, you know, to a user who has not gone through, like, phishing education, they might not know the difference. They might think, assume it's some third-party web service that's using Facebook to authenticate you. So they demand some urgency in the links they send in order to get you to do as little research on your end as possible before entering your credentials.
Dave Bittner: Yeah. So let's say I fall for it, and I enter my credentials. What happens next?
Nick Ascoli: So they will log into your account, presumably automatically, and spam that link out to as many contacts as they can find in Facebook Messenger. So it seems like most of the traffic we've observed as of late is focused in regions pretty consistently. So once the link ends up, most of the traffic is in the United States. I think that's where a lot of Facebook's user base is, especially that uses messenger, but once we see a link arrive in Argentina or Jamaica, for example, we'll then see it fly all over the country, like hundreds and hundreds of visitors, quickly into the tens of thousands of visitors from those countries. The threat actor themselves is not targeting a particular geography. They're just targeting Facebook. They make more money from American users because the ad services that they redirect you to after you enter your credentials pay a little bit more for users coming from America. But typically we see it fly across countries very, very quickly once one person in a new geography gets the link. So there is no regional focus. It's relatively predictable in its pattern. Once it arrives in a country, you know, it'll be entering the messenger inboxes of tons of people in that country and proliferating naturally that way.
Dave Bittner: Well, you mentioned it briefly. So after I put in my login credentials to the fake Facebook website, the fake Facebook login page, then it sends me to an ad page?
Nick Ascoli: Yeah. So they have a couple really interesting techniques that demonstrate some frightening but also, you know, on the threat actor side, relatively interesting and somewhat impressive trends. But what they do now is once you've entered your credentials on the page, they will redirect you several times through different ad tracking services. So on the ad tracking services side, they're occasionally malvertising. They're occasionally legitimate advertising services. On the advertiser side, all they're seeing is someone who's signed up with their ad. Their web advertising service is throwing tons of traffic their way. They think that's great. You're cutting logs on their advertisement. So the threat actor is getting paid. What it's actually doing, though, is simply sending you through rows and rows and rows of refreshes. So it's like, just, you'll see the URL change. If you're doing this like forensically, in a browser, you'll see a change so many times before eventually dropping you on either some scam page asking you for more information, which is simply hosted by an malvertiser, or to a legitimate website that they're getting - they were just in the last tale in the redirect. And they are where you're ultimately landing. So you're never landing on a Facebook video. You're landing on some other website that the threat actor is collecting revenue from in exchange for referring people to that website.
Dave Bittner: And so they get paid, whatever, the fraction of a penny or who knows what, for merely having you quickly drive by?
Nick Ascoli: Yeah. So what we put together was - a researcher in 2021, when we originally picked this up, Mantas Sasnausaks with OWASP, found that the threat actor had a Facebook page associated with the website they were using to host this code called Bender Crack Pro. They messaged Bender Crack Pro, the administrator of that Facebook page, and they asked how much money they were making. And the Bender Crack Pro administrator responded with, we make about $150 for every 1,000 visitors from the United States.
Nick Ascoli: So based on the scale of the campaign, what we put together was each site - and they were spending up rapidly. You know, in short, once Mantis put this research out at the end of 2021, we saw things slow down. And then when - Q1 and Q2 2022, things really sped up. Like, the threat actor got a lot more sophisticated in the automation, and the proliferation of the campaign was just organically explosive. And the view count that we landed at was we were averaging, before they changed the URLs on one particular landing page, they would get around a million visitors. And we located about 400 individual landing pages, which we have no way of confirming if that's the entirety of the attack. It seems like it's probably not. It's more likely than not a fraction of it.
Nick Ascoli: But through the entire, you know, 1 million views on the 400 to 405 webpages we landed on, that's about 400 million page views so far in the campaign, most of that traffic being in 2022, which if you if you apply the price state associated with the viewer to that number, it nets them somewhere around $60 million in just ad revenue. So we're not talking about things that threat actors also usually do with harvested credentials, which is reselling them or potentially marketing them on several different marketplaces for selling stolen credentials. But in ad revenue alone, if we use their figure, we're putting it at about $60 million. Now, is that realistic? Probably not. But based on the sheer volume of traffic, like, we peg it at roughly 400 million paid views, they are definitely making quite a bit of money simply through ad redirects.
Dave Bittner: Wow. Now they've also got your Facebook credentials. Is - do we have any sense that they're bundling those up and selling those?
Nick Ascoli: So we haven't seen the particular credentials harvested for sale on any forums that can be accessed easily. Now, whether they're a part of invite-only forums or some, you know, deeper marketplaces that are a little more difficult to access in the practices of threat research, we don't know. It's very - it seems unlikely that they're not doing something else with the credentials afterwards, because Facebook credentials seem to only be increasing in value despite the sheer volume of them that exist in the wild. Because increasingly, businesses rely on Facebook for marketing, especially small businesses. And plenty of large and midsize companies rely on Facebook for marketing and advertising. So the value of credentials, depending on which credentials have been harvested, can be quite a bit. So the odds that they're not reselling them is low, but we haven't actually seen them reselling them in the wild. So they might be using reusing them for internal things or they might not be reselling them at all. But it wouldn't be consistent with the typical practices of an internet fraudster.
Dave Bittner: Now, in terms of these fake landing pages, what is your sense for how long they stay up before they have to cycle through a new one?
Nick Ascoli: Yeah, we see them typically around for one to two days. So they are in what we presume to be an automated fashion, or at least in the speed that we've observed, is very likely automated using legitimate web services. The ones we've seen in the wild are glitch.me, onepage.io is something they're using as of right now, SamCart, amaze.co. So they use a lot of legitimate web services who are not blocking their activity at all. They're not blocking their accounts. They're not stopping them from using their web service to proliferate these attacks. So the threat actor is signing up for one of these services and then on a daily basis spinning up new domains and sending them out.
Nick Ascoli: So the benefit to them is one, even if a URL does get burned or reported as phishing, they're creating new ones on a daily basis automatically anyway to proliferate the attack. And two, their use of these legitimate services makes it really difficult for Facebook or other social media networks to block them because real businesses are using glitch.me me and onepage.io and SamCart for legitimate business on these social networks.
Nick Ascoli: So the challenge for Facebook is if they block that outright, the parents - you know, the parent domain of onepage.io or samcart.com, they're blocking a lot of legitimate business going on on their website and in Facebook Messenger. So the adversary is able to skirt detections by using these legitimate webpages to host their malicious content. And we see them rotate through these different quick deploy web application services on a weekly to biweekly basis and spinning up new domains on a daily to by-daily basis.
Dave Bittner: Is there anything that Facebook could be doing here to clamp down on the abuse of Messenger?
Nick Ascoli: So Facebook does a lot. They have a threat intel team that is dedicated to solving problems like this. I think the recent use of legitimate platforms for these campaigns has been what's made it so challenging for them. So what they can do probably better for the user is education. This is, you know, this is certainly a question of tooling, but it's also a question of education for the user. Someone who has gone through some kind of phishing exercise or training is probably not going to click these links. But given that we've seen hundreds of millions of people click these links, that does not account for, you know, an overwhelming majority of Facebook users.
Nick Ascoli: So whether it's flagging links, as, you know, you might not want to click this, educating users better on what scams might look like in Facebook Messenger or cooperating more with these legitimate application service providers that are abused so frequently in Facebook, I think there are definitely things that can be done. But the use of legitimate web services presents a unique challenge to them that I'm sure has been difficult to tackle.
Dave Bittner: And what about multifactor authentication? I mean, that - I suppose that would slow down the abuse of Messenger, but you're still going to find yourself redirected to all the ad sites, right?
Nick Ascoli: Yup. The adversary will still make money, but they will not be able to use your account to proliferate the attack. So the use of multifactor authentication will do damage to the adversary, to the life cycle of the adversary's attack. But it certainly won't stop them from making money.
Dave Bittner: So what are your recommendations then? I mean, for folks to best protect themselves against this, you mentioned education. What else is in play here?
Nick Ascoli: I think education for the users is obviously No. 1 here. Knowing how to recognize a fake link or a suspicious link or a typosquatted or look-alike domain is incredibly important, but tooling is also important. What we've seen in our testing of these domains is when we run them through, you know, popular domain reputation scanning services, we're seeing these domains come back clean, despite being active phishing infrastructure and being suspicious in several ways. So I think it is also on domain reputation analysis engines and tooling, which is supposed to be protecting users from visiting these links, which is failing the user in these cases, to improve the quality and integrity of their detections, of the - whatever algorithmic functions they're using to determine the trustworthiness of a page. Because in an overwhelming majority of reputation analysis engines, we're seeing these domains pass the test because their parent domain is trusted, their content does not look suspicious. And sometimes, they're waiting several seconds to actually load the Facebook login portal and they're loading, like, some innocuous page first to skirt detection by traditional, you know, domain reputation or DNS blocking tools. So the problem is definitely multifaceted and a combination of user education and improvements in tooling, both by Facebook and by domain reputation analysis services.
Dave Bittner: Do we have any sense for who's behind this or, you know, what part of the world they're coming from?
Nick Ascoli: We traced this particular adversary back to Colombia, and we're cooperating with the FBI and Interpol in their investigation into the activity, which, as I said, still continues today. It's still a very active campaign. And we were able to do quite a bit of attribution because in the adversaries' early days of this campaign, particularly the beginning of 2022 and the end of 2021, they were relatively lazy from an operational security perspective. So within the code, there were several comments indicating what website was used to generate this code. And by tracking down the owner of that particular website, which in this case - I mentioned earlier Bender Crack Pro, this Facebook page. In the code on virtually all of these Facebook landing pages until about two weeks ago, there was a line that said in Spanish developed for bendercrack.com.
Nick Ascoli: Now, when we looked in the Wayback Machine at bendercrack.com, we saw an inventoried copy of the page, an archived copy of the page, which contained the phone number of the administrator of the page. They said, sorry, we've been taken down due to copyright complaints, but here's where you can reach out to me. Using that phone number, we were able to connect it with several email addresses, which were used for different scam campaigns online and one which was associated with an individual who we tracked down to be offering several different hacking services and operating several illicit businesses online, mostly related to social media hacking services. Operational security has improved recently. They've removed parts of code that can be attributed directly to them, but just shy of two years, their name was almost directly associated with an overwhelming majority of the fake login portals that we found.
Dave Bittner: I suppose it's worth mentioning, too - I mean, it's - I don't know. Personally, it's hard to have a tremendous amount of sympathy for the online advertisers, but they're falling victim here as well. They think their message is being put in front of people when it's really not.
Nick Ascoli: They are, yeah, and so are the legitimate web application service providers. The advertisers are being duped by these adversaries and paying them out in large amounts. So the advertisers are losing money because these advertisements aren't legitimately landing in front of a user. Only really one of them in the chain of redirects is. But also the application service providers that the user - the adversary is using to spin up these webpages are being abused. Their trust with these other platforms are being abused. And when you go into tools like urlscan.io and run through some of these parent domains, you see so much malicious activity associated with these quick web deploy services, which are offering a legitimate service to an overwhelming majority of the internet but are being in no small way abused by malicious actors online.
Dave Bittner: Our thanks to Nick Ascoli from Foretrace for joining us. The research is titled "Phishing Tactics: How a Threat Actor Stole 1 Million Credentials in Four Months." We'll have a link in the show notes.
Dave Bittner: The CyberWire podcast is proudly produced in Maryland out of the startup studios of DataTribe, where they're co-building the next generation of cybersecurity teams and technologies. Our amazing CyberWire team is Rachel Gelfand, Liz Irvin, Elliott Peltzman, Tre Hester, Brandon Karpf, Eliana White, Puru Prakash, Justin Sabie, Tim Nodar, Joe Carrigan, Carole Theriault, Ben Yelin, Nick Veliky, Gina Johnson, Bennett Moe, Chris Russell, John Petrik, Jennifer Eiben, Rick Howard, Peter Kilpe, and I'm Dave Bittner. Thanks for listening. We'll see you back here next week.


