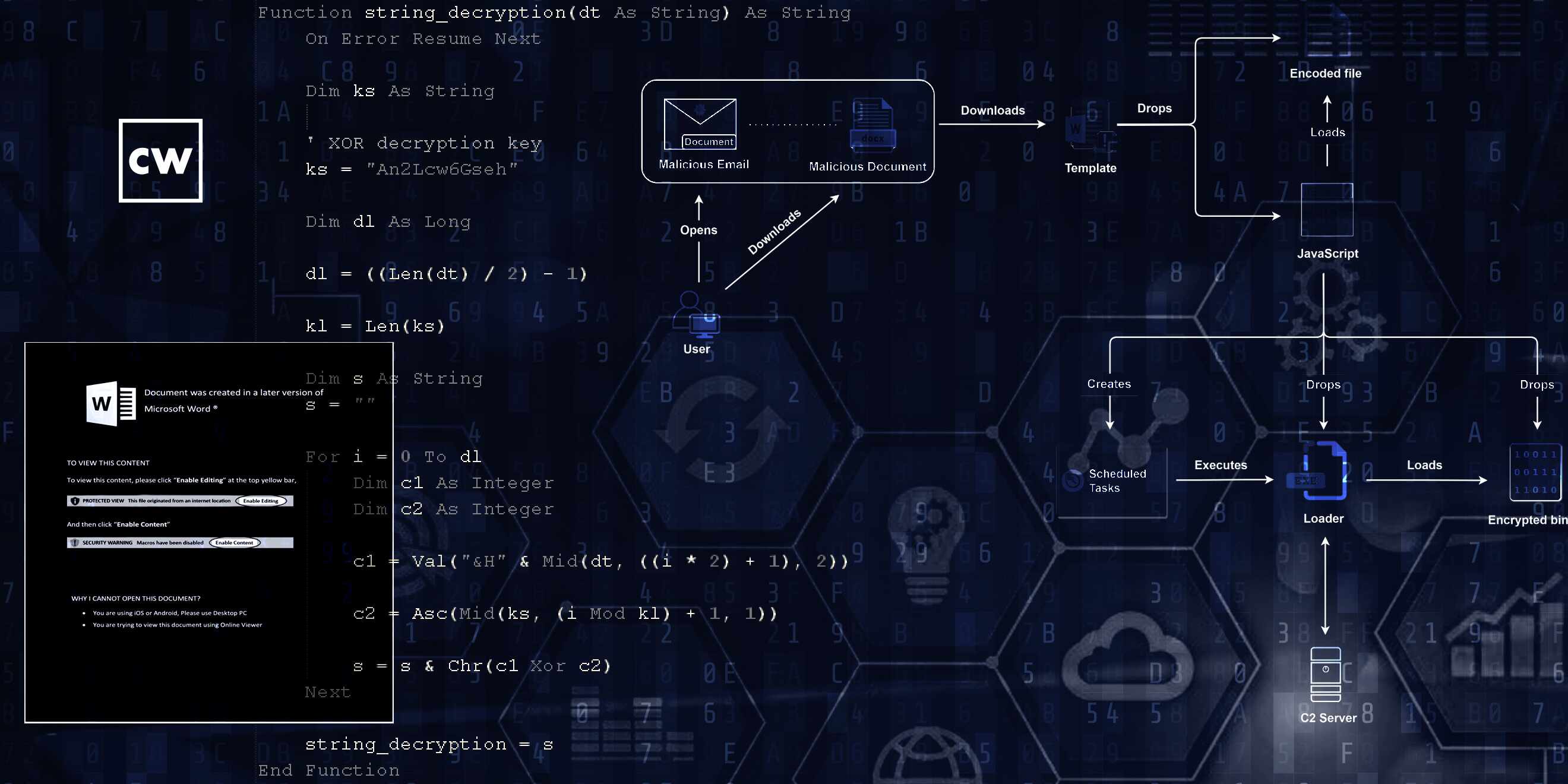
Evilnum APT returns with new targets.
Deepen Desai from Zscaler ThreatLabz joins Dave to discuss their work on "Return of the Evilnum APT with updated TTPs and new targets." Zscaler’s ThreatLabz team recently caught a new Evilnum APT attack campaign that uses the document template on MS Office Word to inject a malicious payload to the victim's machine. There are three new instances used of the campaign, including updated tactics, techniques, and procedures.
Researchers have been closely monitoring Evilnum APT’s activity. They say ThreatLabz identified several domains associated with the Evilnum APT group, which has led them to discover that the "group has been successful at flying under the radar and has remained undetected for a long time."
The research can be found here:



