Evilnum APT returns with new targets.
Dave Bittner: Hello, everyone, and welcome to the CyberWire's "Research Saturday." I'm Dave Bittner, and this is our weekly conversation with researchers and analysts, tracking down the threats and vulnerabilities, solving some of the hard problems of protecting ourselves in a rapidly evolving cyberspace. Thanks for joining us.
Deepen Desai: What we saw since the beginning of 2022 was a lot of new campaigns where the tactics, techniques and procedures that were being leveraged changed significantly.
Dave Bittner: That's Deepen Desai. He's global CISO and head of security research and operations at Zscaler. The research we're discussing today is titled "Return of the Evilnum APT with Updated TTPs and New Targets."
Deepen Desai: Changing the targets was one of the thing. Changing the way the payloads were being delivered was another. And the overall success in terms of staying undetected, like some of the IOCs that were involved, was also interesting in these campaigns.
Dave Bittner: And does that in general, I mean, point to a well-resourced, you know, well-funded, well-run organization?
Deepen Desai: That is, yes, usually the case of some of these well-funded, well-run APT groups that we observe. It's just that when we see a significant change in some of the techniques that they've been using, I mean, it's definitely much more undertaking on their part to go through. And we will talk about some of those techniques in this call.
Dave Bittner: Well, let's dig into some of the details, then. I mean, do we want to start off - is it useful to have a little bit of history here of where Evilnum began, the types of things that they were known for, before we get into some of the changes?
Deepen Desai: Yeah, absolutely. So I mean, the key targets for Evilnum APT Group have been primarily financial services organizations, and they were targeting companies dealing with trading and compliance, primarily in the region of U.K. and all of Europe, to be honest. So that's where we were seeing a lot of these activity. What changed - and this is as of March of 2022 - we observed the update in terms of the choice of targets, and one of the primary one that really draw our attention was them starting to target an intergovernmental organization which deals with international migration services. And the other interesting part was the timeline of attack, and the nature of the target chosen coincided with the Russia-Ukraine conflict as well.
Dave Bittner: Who do we suppose is behind Evilnum? Do we have a good sense there?
Deepen Desai: That's where the attribution in terms of the country behind it - I would stay away from that for this group. I mean, there are a couple of regions. But yeah, this one, we'll stay away from that.
Dave Bittner: Well, let's dig into some of the other things that you're observing here. I mean, what are they up to these days that caught your eye?
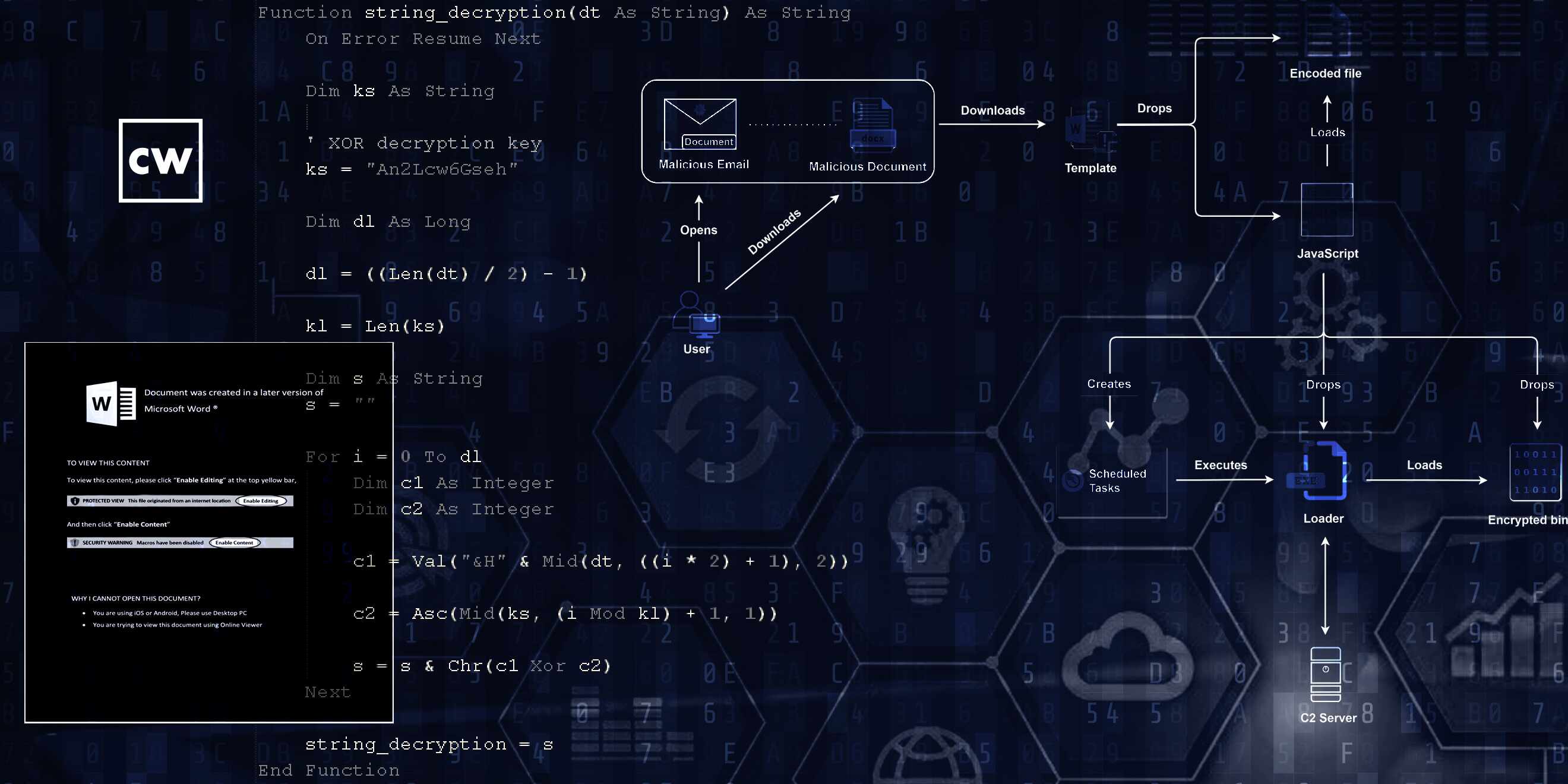
Deepen Desai: Right. So I'll dive into the campaign that we uncovered and then publish our analysis. So No. 1, back in the day, they were using - and this is as early as last year - some of the campaigns that the team observed, we noticed them using mostly Windows shortcut files, which is LNK files sent inside a zip archive, which are usually sent with - through email attachments or getting a user to click on the link to download them. In the most recent one - and I'm talking about the March one - they started leveraging macro documents and using template injection technique, which is used by many other groups as well.
Deepen Desai: But what was unique over here was they were also making use of something that we call VBA code stomping technique. And I'll explain it in easier terms what that means. But - so it's a macro document using template injection, leveraging VBA stomping technique. The outcome of this is it is able to bypass a lot of static analysis tools as well as also deters, you know, reverse engineering from other security analysts. What the VBA code stomping technique does is it essentially, you know, destroys the original source code, and only a compiled version of the VBA macro code is stored inside the document. It's also known as p-code, right? And then that's what causes the static tools at times to not detect this.
Dave Bittner: So it makes it more challenging to reverse-engineer.
Deepen Desai: Yes, and that as well. So detecting it using those static analysis tools by various security engines - that becomes challenging. And also, to analyze by the researchers using automation as well as even manually, you know, you need to have a few extra steps before you figure out what's going on. Now, so that's the stage one - starts with that. Then it delivers a heavily obfuscated JavaScript, which is further used to download and decrypt the encrypted binary on the endpoint. And so that's another way in which they are keeping that final payload shielded from getting detected.
Deepen Desai: And here as well, we saw several new techniques - the way the code is obfuscated, right? I mean, you will see many other groups leveraging obfuscated JavaScripts as well. But there are a few things that we have documented in our analysis. One of the ones that I would call out is them making use of this shuffling technique. In easier terms, think of an obfuscated JavaScript code where there are - there's, like, a array of strings and those strings are basically getting replaced by the actual code on - when the code becomes deobfuscated. And there are a lot of automated tools that are able to do this process of deobfuscation automatically. With this shuffling technique, there is an added layer of obfuscation that happens before you are able to replace those strings or variables with the actual piece of code.
Deepen Desai: So that also breaks a lot of the automation and makes it difficult for the static tools to detect. So that's the second stage payload where this obfuscated JavaScript is involved, and that is responsible for, as I said, decrypting the binary payload. And at the binary payload stage, they're, again, using a technique called Heaven's Gate technique. And this is not a new technique. It has been used by other groups as well. It's basically a method for running, you know, 64-bit code in a 32-bit process. And, again, the goal over here is to evade some of the security scanners when they're trying to deliver this malicious payload.
Dave Bittner: Is it a case with - obfuscation, as you're describing here - is this a bit of a cat-and-mouse thing where you'll see innovation from the APT group? And then eventually, will the tools used to analyze it catch up to that?
Deepen Desai: Absolutely. Yes. I mean, these are - there are new techniques that we observe being used by them. And we always talk about how these APT groups have access to many of the tools that, you know, us as security researchers have access to as well, like things like VirusTotal or their own version of VirusTotal, for instance, where they will test out a security scanner. They will test out even the publicly exposed sandboxes and figure out ways to get around them. And then once those payloads are used in some of these attacks, security folks discover them. They will try to make sure that the engines are updated to handle that newer technique as well.
Deepen Desai: So it is cat-and-mouse game now. The amount of coverage that you are able to achieve with those updates - right? You shouldn't just add coverage for what you just observed but also take into account future variations, right? They did this. They could do similar things on 10 other areas. That will be the difference between the future campaigns being successful - as successful as the one which we just talked about.
Dave Bittner: Is it fair to say that - for folks like yourself who are looking into this sort of thing, that, you know, that's part of the fun - is figuring out, you know, what's going on here and trying to see where they're going next?
Deepen Desai: Absolutely. I mean, that's why most security folks will say there's never a dull day. You're always learning...
Dave Bittner: Right.
Deepen Desai: ...Newer stuff, right? There's constant evolution happening on both sides of the table.
Dave Bittner: Well, let's talk about persistence. How do they maintain that?
Deepen Desai: Yeah. So in this case - and that was another part where they were trying to evade detection, where they were taking - they were making use of sort of well-known process names from Windows OS when the binary is getting dropped, so it's basically a spoofed legitimate Windows - as well as some of the third-party binary names that were being leveraged for dropping. And to achieve persistence, they will basically create a scheduled task that will ensure that the payload executes every time their Windows system starts.
Dave Bittner: Is there effort to hide that as well, the scheduled task, to evade detection?
Deepen Desai: I mean, that's where the names that they're choosing as well as the directory structure - if you notice, they're putting the binary inside Microsoft font-related folders.
Dave Bittner: I see.
Deepen Desai: And then the name chosen for the scheduled task is also update model task. So it's fairly generic leveraging Microsoft font directory structure. So, yes, that basically helps them hide the persistent command.
Dave Bittner: I see. No, it makes total sense. Well, let's move on to the next stage, then. I mean, where are they actually dropping on the system?
Deepen Desai: Yeah. So this is where once the binary is dropped in that font folder, that's where it will be executed from. And even on the execution stage, I mentioned about Heaven's Gate technique, and that's how the actual malicious payload, the backdoor payload that will be responsible for C&C activity, will get decrypted in the memory. This binary will then choose the C&C domain for performing the command-and-control activity, receiving commands, responding back with information that the threat actor is interested in.
Deepen Desai: Here as well, when we looked at the domains that were involved, many of them were registered to match the target organization. And so some of them were typosquatted (ph). Some of them were matching well-known services. Some of them were even matching the teams that were going on. So if you look at it, there's a domain called covdd.org - right? - so COVID-related domain. There was azuredcloud.com - another typosquatted domain. Azure Cloud is what is being used. There's a misspelled one for Norton Analytics where the N is missing as part of the analytics. So many of these domains, they manage to keep undetected for months, actually.
Dave Bittner: And then so ultimately, what are they after here?
Deepen Desai: So this is definitely a financially motivated group. They're after your dollars, right? They will steal information. Yeah, exactly. And, you know, we've seen in the past them using crypto team, finance teams. Their main motive is to gain dollars. So crypto finance and immigration is what we have seen in the past two years being leveraged as teams by this group.
Dave Bittner: And so what are your recommendations, then, for organizations to best protect themselves?
Deepen Desai: Yeah. So in this case, again, I always go back to the zero-trust fundamental pillars, right? Especially in this day and age where you have this hybrid remote workforce and folks coming into the office, folks still working remote or doing both, you need to ensure you have consistent security being applied to all your endpoints - right? - when they're egressing into the internet.
Deepen Desai: So the four pillars that I always call out is - prevent compromise. That's where you ensure consistent security policies are applied, no matter where your endpoints are. Prevent lateral movement. The damage is fairly limited when they manage to hit one of your endpoint. But the - as soon as that blast radius increases from one endpoint to your entire network, that's when it translates into an organization-wide breach, right? And in this case, they will have access to a much broader data set. So have controls in place like user to app, app-to-app microsegmentation, to prevent that lateral movement. Prevent data exfiltration, where you're actually inspecting everything that leaves your endpoint - very important to block this type of exfiltration attempts. And then finally, you know, you need to reduce your external attack surface. Anything that is exposed to the internet is what many of these threat actors go after, the easy entry points into your environment.
Deepen Desai: Now, one specific engine, which I would like to say is a must-have for most enterprises - that's what most security peers, leaders that I talk to believe as well - it's having the ability to perform in-line cloud sandboxing, right? As I describe, payloads are new. The techniques that they were using - brand-new. So unless you detonate that payload and observe the behavior - right? - and block it at the time the attack is happening, you know, that specific engine plays a very important role in achieving that.
Dave Bittner: You know, it also strikes me that this could be a good case for the use of threat intelligence. You know, if you're - have someone on the lookout for things like the typosquatting, as you were saying, you know, registering domains that are similar to things that are of interest to your organization, that could have value as well.
Deepen Desai: Absolutely. Yeah. Keeping an eye on newly registered domains, as you mentioned, typosquatted domain detection, and then ultimately, when you discover these kind of things, sharing is caring, and having all the security vendors, all the security community - making them aware of these new TDPs, so we all, as a group, come up with new countermeasures, whether it's adding coverage for the IOCs observed or whether it's adding coverage for the overall techniques that we're seeing so that even if the IOCs change, we're still able to block these type of attacks.
Dave Bittner: Our thanks to Deepen Desai from Zscaler for joining us. The research is titled, "Return of the Evilnum ATP with Updated TTPs and New Targets." We'll have a link in the show notes.
Dave Bittner: The CyberWire podcast is proudly produced in Maryland out of the startup studios of DataTribe, where they're co-building the next generation of cybersecurity teams and technologies. Our amazing CyberWire team is Rachel Gelfand, Liz Irvin, Elliott Peltzman, Tre Hester, Brandon Karpf, Eliana White, Puru Prakash, Justin Sabie, Tim Nodar, Joe Carrigan, Carole Theriault, Ben Yelin, Nick Veliky, Gina Johnson, Bennett Moe, Chris Russell, John Petrik, Jennifer Eiben, Rick Howard, Peter Kilpe, and I'm Dave Bittner. Thanks for listening. We'll see you back here next week.


