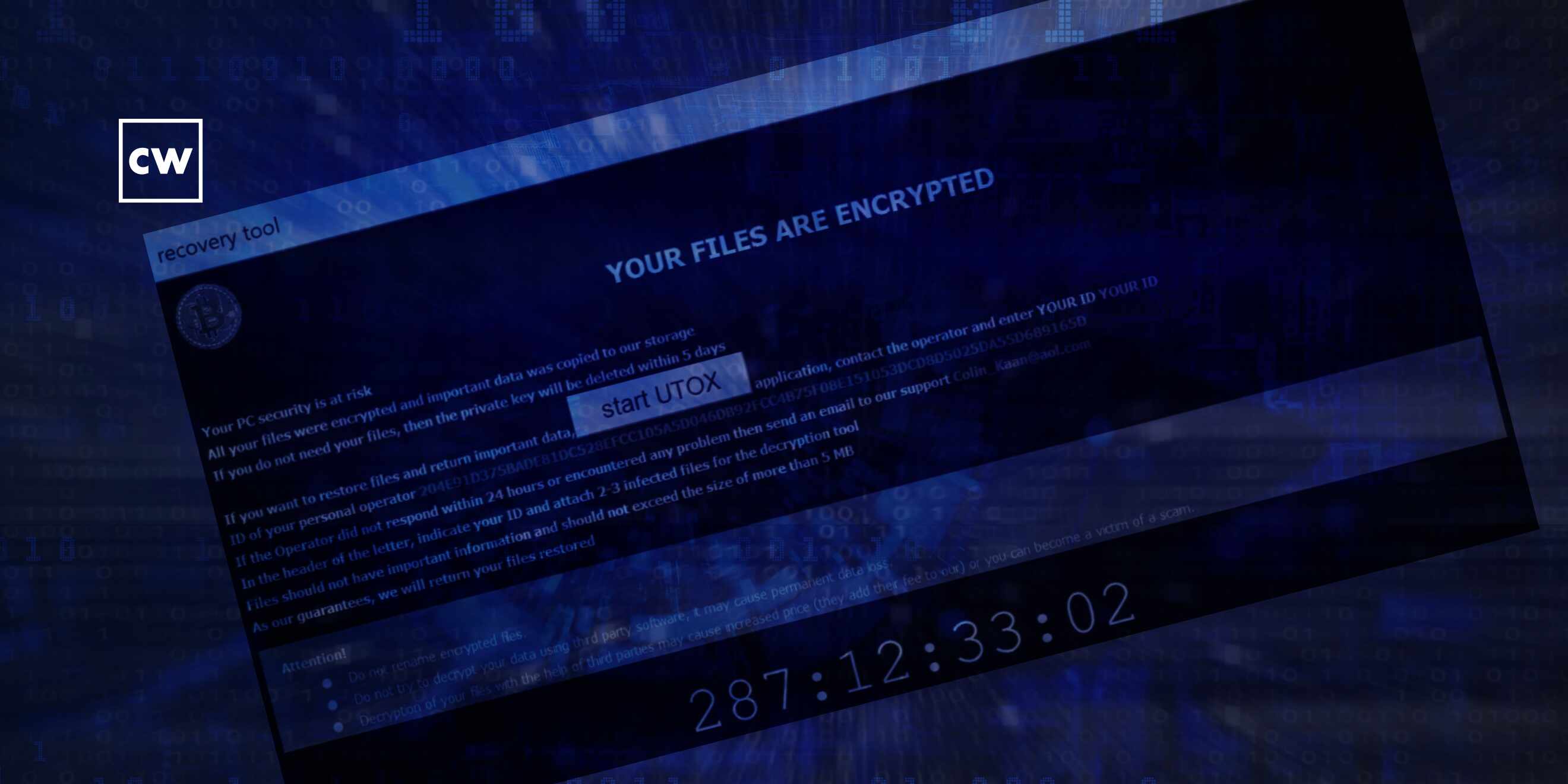
An in-depth look on the Crytox ransomware family.
Dave Bittner: Hello, everyone, and welcome to the CyberWire's "Research Saturday." I'm Dave Bittner, and this is our weekly conversation with researchers and analysts tracking down the threats and vulnerabilities, solving some of the hard problems of protecting ourselves in a rapidly evolving cyberspace. Thanks for joining us.
Deepen Desai: Crytox ransomware has been around since at least 2020, but it hasn't been in the news. We haven't seen anything major back then.
Dave Bittner: That's Deepen Desai from Zscaler. Today we're talking about his team's research on the Crytox ransomware family.
Deepen Desai: In September 2021, the team actually noticed a company named RTL. It's a Netherlands-based company that was hit. And it was publicly acknowledged as well. Although one of the thing that the team noticed back then was the ransom amount was 8,500 euros. And that's very, very small compared to the ransom demands that we see with some of the other ransomware gangs like Conti and Hive and others. So we've been tracking in the payloads. We've been tracking the developments on the campaign side as well. And one of the thing that the team noticed over here was, unlike many of the other ransomware groups, Crytox ransomware does not perform double extortion attacks. It just performs data encryption and, you know, holds it for ransom. It does not perform data exfiltration from the impacted machine.
Dave Bittner: Going a little old school with their ransomware, right?
Deepen Desai: Exactly. It is one of the old-school ways of doing things. There are a couple other things we noticed. I mean, they did make it easier for the victims to communicate back with the threat actors. So they were dropping this, you know, peer-to-peer instant messenger app called Tox (ph) on the infected machine. And you just click on it, and you are basically able to communicate and negotiate the ransom amount with the threat actor.
Dave Bittner: Can you walk us through what's going on technically behind the scenes here? Is there any interesting aspects to that part of it?
Deepen Desai: Yeah, in terms of the encryption, I mean, there's nothing that is different than what we have seen before. I mean, it's using AES-CBC with a per-file 256-bit key that is protected with a locally generated RSA public key. And it uses this to encrypt local disks, network drives, and, you know, at all of those location you will see a ransom note with a five-day timer. You know, that's basically notifying the victim that your files have been encrypted - pay or you will lose all the data.
Dave Bittner: And so you still have the ability to pay on that machine. I mean, they don't completely disable it. You can communicate with them.
Deepen Desai: Yeah. You're basically using the messenger application to communicate, and then they will provide the link for performing the payment.
Dave Bittner: Is there any sense that if you follow through with them and you pay the ransom, you'll get your files back?
Deepen Desai: For most ransomware groups, we do observe that you do get a key back - right? - which will allow you to decrypt your files. So while we didn't go that route to confirm it, at least for the publicly known case, they did get the key and were able to restore their file.
Dave Bittner: It's interesting that the ransom demand is so low. And, you know, I wonder if they're comparatively trying to fly under the radar compared to some of the bigger players here.
Deepen Desai: Yeah. That does sort of raises eyebrow. Like, why so low? Maybe they're trying to do more development and more testing and then, as you pointed out, staying under the radar so that there's no law enforcement action as well, given so much focus on the ransomware threat actors these days. We also noticed, actually, while the team was analyzing some of the payloads, that the encryption mechanism that they have used - it's actually prone to some weaknesses that could actually allow some brute-forcing methods, you know, that can result in us decrypting the files as well. So definitely not one of those, you know, sophisticated ransomware payloads. It still probably appears to be a work in progress.
Dave Bittner: And is the group trying to prevent analysis from researchers like yourself? Do they have elements of that in there?
Deepen Desai: They did have some basic anti-debug, anti-analysis technique, but nothing to write home about.
Dave Bittner: OK, nothing sophisticated. I mean, is that pretty much what you're seeing here with this group, that we wouldn't rate their sophistication as being particularly high?
Deepen Desai: That is accurate, yes.
Dave Bittner: Yeah. And so in terms of folks best protecting themselves against this specific group, what are your recommendations?
Deepen Desai: Yeah. So I think the guidance over here is to look at the ransomware problem holistically. Every time I speak to, you know, some of the large organization security leaders, I always ask them to look at the problem in four buckets. What are you doing to reduce your external attack surface? Because when these gangs go after you, they will first try to find out what all things are exposed. And they may come through one of the users falling for a phishing attack. They may come after you through an asset that is exposed to the internet. It could be a server. It could be a work load. It could be your system sitting in the corporate environment. It could be a VPN, as I'm - as we have seen before. But so look at what you can do to reduce that external attack surface. Second is provide consistent security on all internet-bound traffic with full SSL inspection. And that's where a proxy-based architecture really helps out. The goal over there is to prevent that initial infection.
Deepen Desai: The third bucket is, what can you do to prevent that latter propagation phase? That's where majority of these ransomware gangs does a lot of damage. Having one system going down with a ransomware attack versus the entire environment going down is the difference between it being a small incident or org-scale breach. So for their user to have segmentation, app to have microsegmentation plays a very important role in containing this incident to a single host versus entire environment. And then finally, in this case, Crytox is not exfiling data, but more than 50% of the ransomware threat actors that we're tracking perform data exfiltration as well. So you need to have consistent data loss prevention strategy for all your internet-bound traffic, right? And that's where, again, SSL inspection plays a very important role because these guys are just using public cloud, you know, SaaS locations to even exfil your data from the infected machines.
Dave Bittner: Yeah, it's really interesting to see as the ransomware, I don't know, ecosystem continues to evolve that we have players coming in and running at all different levels. You know, I think it's perhaps easy to say that these folks are kind of at the entry level - you know, not terribly sophisticated, not asking for a lot of money, trying to go unnoticed. And then you have that all the way up to the big players and everything in between.
Deepen Desai: Yeah, exactly. Yeah. It's a gamut. It's a pyramid model where there's, like, you know, highly sophisticated gangs at the top. And then there's, like, dozens and dozens of these new kids on the block or more work-in-progress kind of ransomware gangs.
Dave Bittner: Yeah. All right. Well, Deepen Desai, thanks for joining us.
Dave Bittner: Our thanks to Deepen Desai from Zscaler for joining us. The research is on the Crytox ransomware family. We'll have a link in the show notes. This CyberWire podcast is proudly produced in Maryland out of the startup studios of DataTribe, where they're co-building the next generation of cybersecurity teams and technologies. Our amazing CyberWire team is Rachel Gelfand, Liz Irvin, Elliott Peltzman, Tre Hester, Brandon Karpf, Eliana White, Puru Prakash, Justin Sabie, Tim Nodar, Joe Carrigan, Carole Theriault, Ben Yelin, Nick Veliky, Gina Johnson, Bennett Moe, Chris Russell, John Petrik, Jennifer Eiben, Rick Howard, Peter Kilpe, and I'm Dave Bittner. Thanks for listening. We'll see you back here next week.


